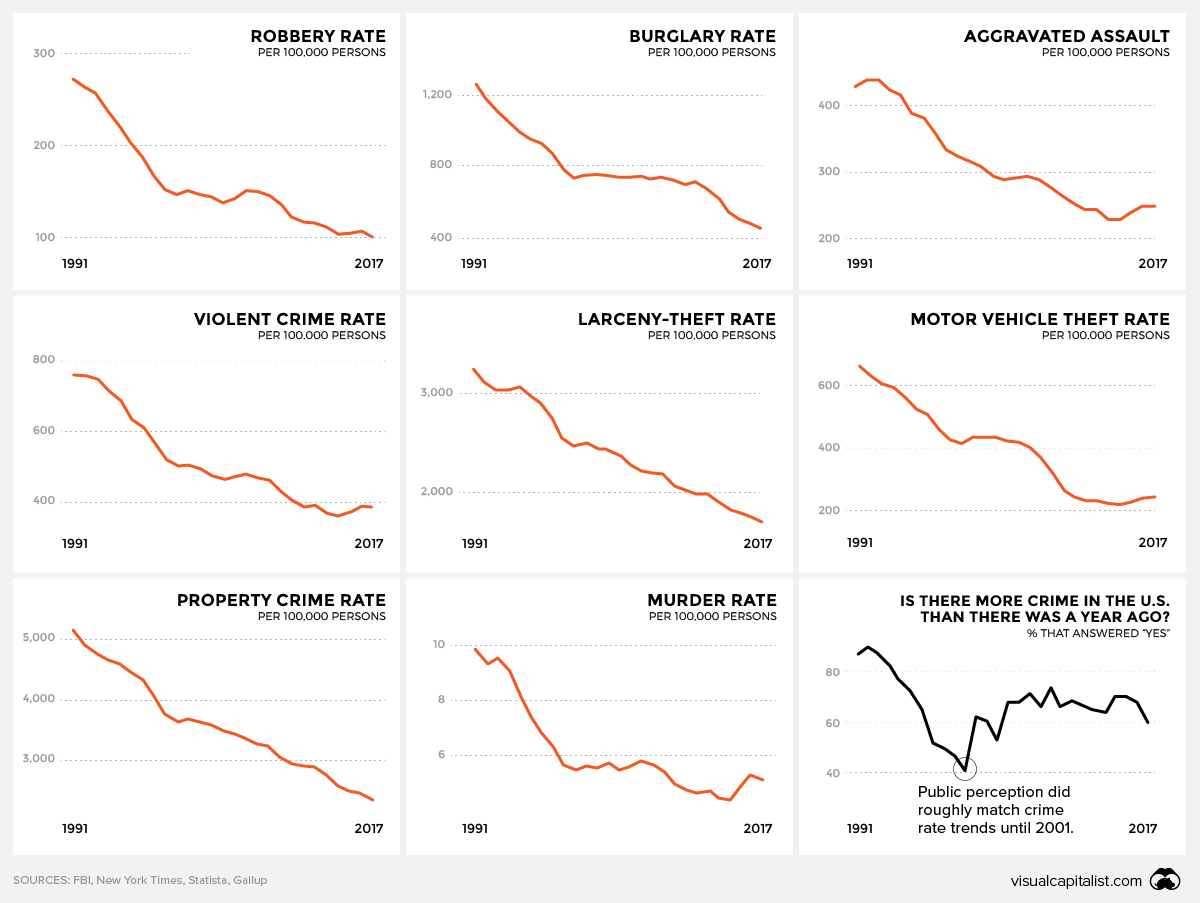
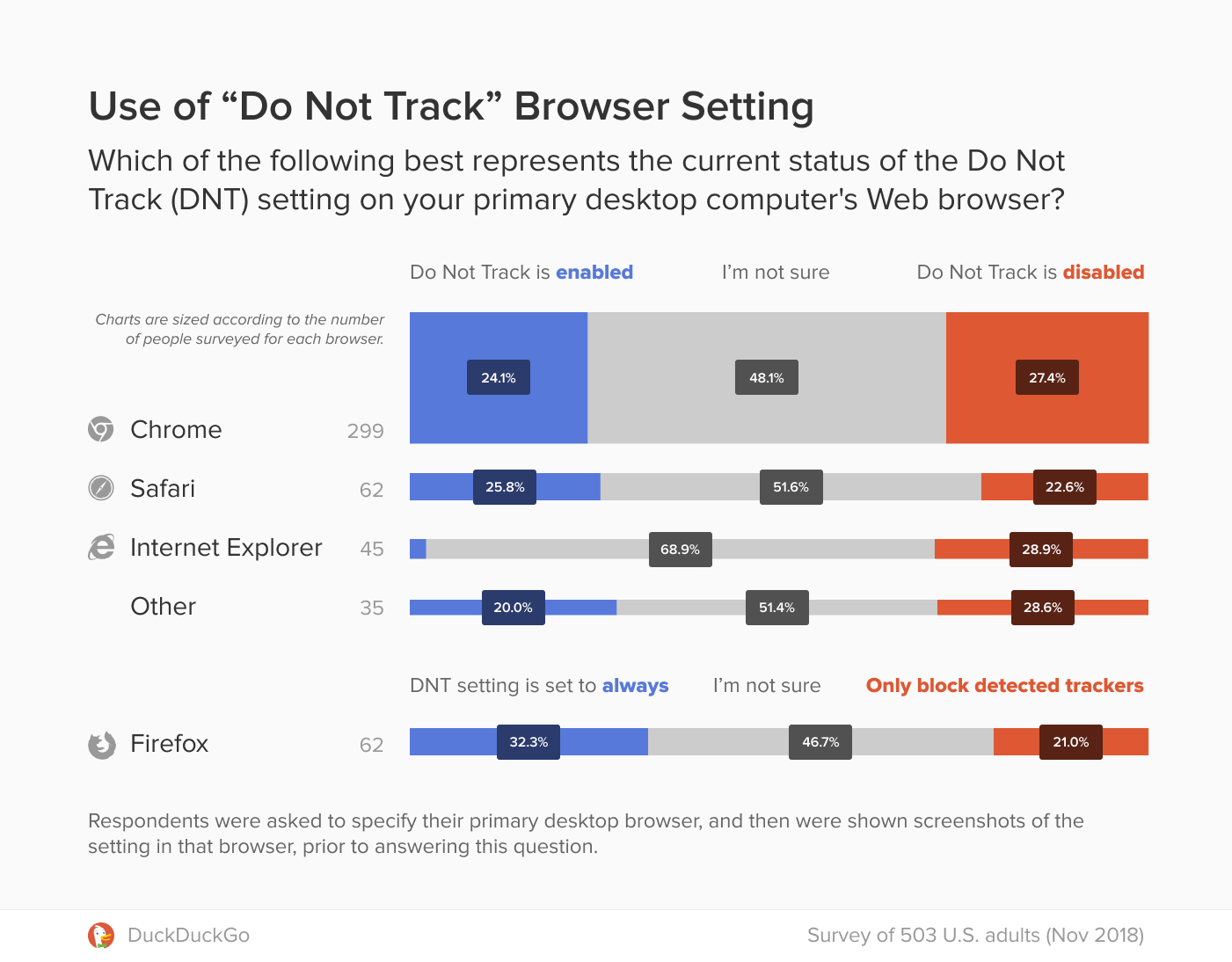
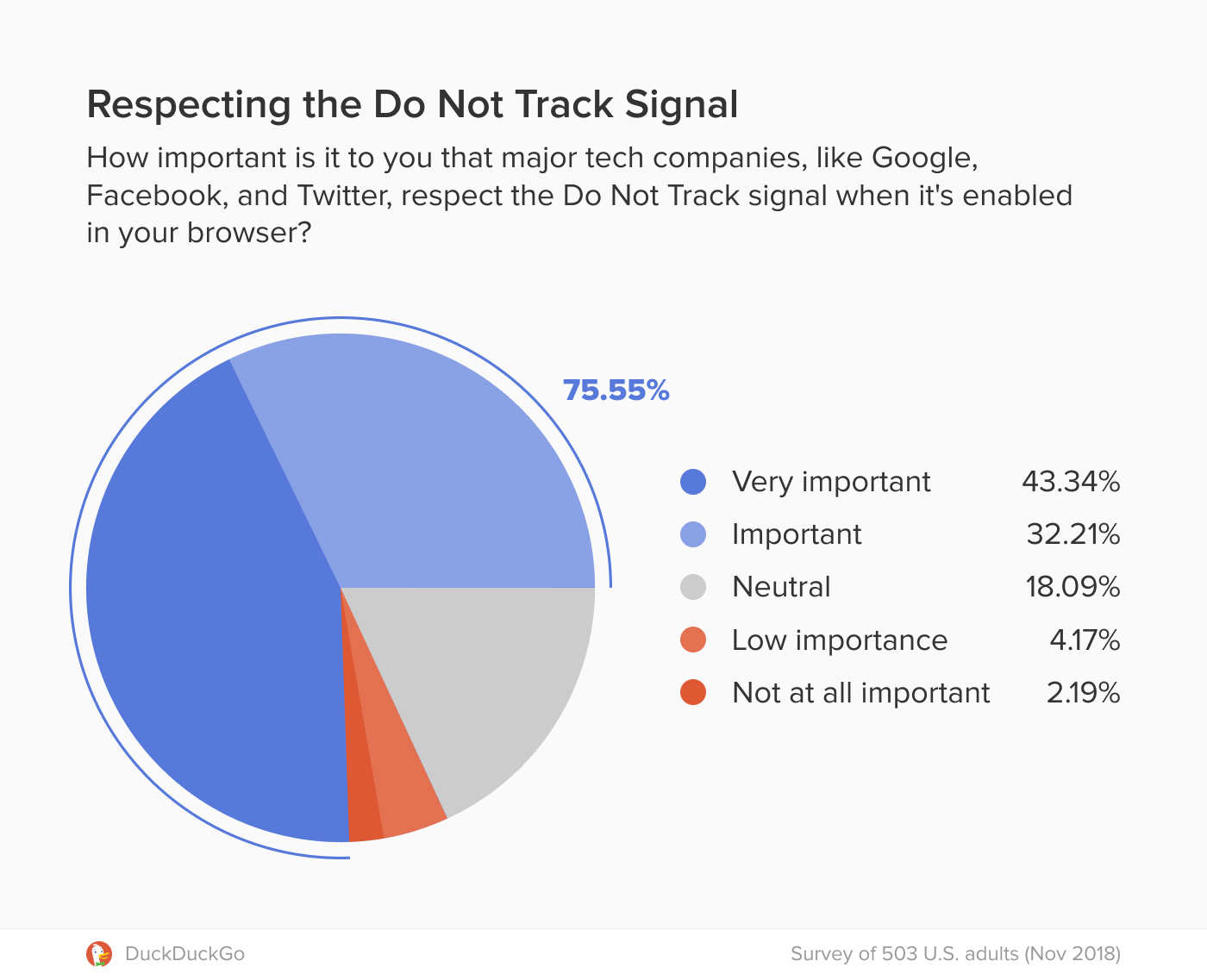
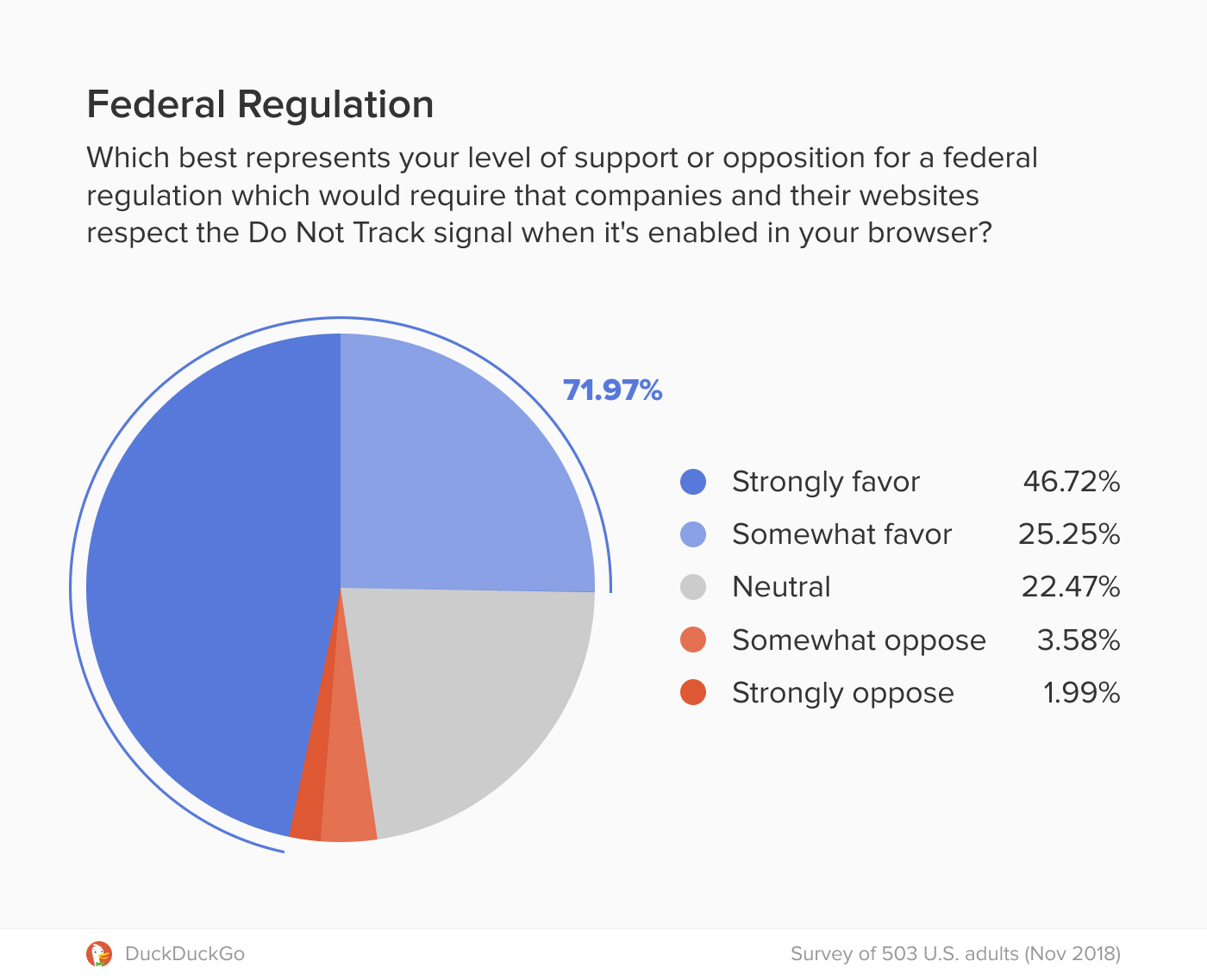
Scientists from ITMO in collaboration with international colleagues have proposed new DNA-based nanomachines that can be used for gene therapy for cancer. This new invention can greatly contribute to more effective and selective treatment of oncological diseases. The results were published in Angewandte Chemie.
Gene therapy is considered one of the promising ways of treating oncological diseases, even though the current approaches are far from perfect. Oftentimes, the agents fail to discern malignant cells from healthy ones, and are bad at interacting with folded RNA targets.
In order to solve this issue, scientists, including a Russian team from ITMO University headed by professor Dmitry Kolpashchikov, proposed special nanomachines. They sought to develop particular molecules, deoxyribozymes, which can interact with targeted RNA, bind them, unfold and cleave. According to the idea, these nanomachines have to recognize DNA oncomarkers and form complexes that can break down messenger RNA of vital genes with high selectivity, which will then result in apoptotic death of malignant cells.
The researchers tested the efficiency of the new machines in a model experiment and learned that they can cleave folded RNA molecules better than the original deoxyribozymes. They showed that the design of the nanomachine makes it possible to break down targeted RNA in the presence of a DNA oncomarker only, and the use of RNA-unfolding arms provides for better efficiency. The scientists also learned that the nanomachine can inhibit the growth of malignant cells, though cellular experiments didn’t show high specificity. The researchers associate this result with a possibly poor choice of the RNA target and a low stability of DNA structures in the cell.
The new approach differs fundamentally from the ones used before. The existing gene therapy agents are aimed at suppressing the expression of oncological markers. In the research in question, the scientists focused on the messenger RNA of vital genes, and the oncological marker was used as an activator. This makes it possible to apply the DNA nanomachine in treating any kind of cancer by using new DNA oncomarkers for activating the breakdown of targeted molecules.
The new invention opens new ways of treating oncological diseases. Still, there are many experiments to be conducted before it can be applied in therapy.
“For now, we are trying to introduce new functional elements in the framework that will contribute to a more effective recognition of oncological markers, and are also optimizing the DNA nanomachine for various RNA targets. In order to improve the efficiency and selectiveness of our constructions in cellular conditions, we are selecting new RNA targets and studying the stability of DNA machines in cells, which we plan to improve with the help of already existing chemical modifications,” comments Daria Nedorezova, Master’s student at ITMO University.
Read more at: https://phys.org/news/2019-02-nanomachines-taught-cancer.html#jCp
Source: Nanomachines taught to fight cancer