Microsoft reckons 0.5 per cent of Azure Active Directory accounts as used by Office 365 are compromised every month.
The Window giant’s director of identity security, Alex Weinert, and IT identity and access program manager Lee Walker revealed the figures at the RSA conference last month in San Francisco.
“About a half of a per cent of the enterprise accounts on our system will be compromised every month, which is a really high number. If you have an organisation of 10,000 users, 50 will be compromised each month,” said Weinert.
It is an astonishing and disturbing figure. Account compromise means that a malicious actor or script has some access to internal resources, though the degree of compromise is not stated. The goal could be as simple as sending out spam or, more seriously, stealing secrets and trying to escalate access.
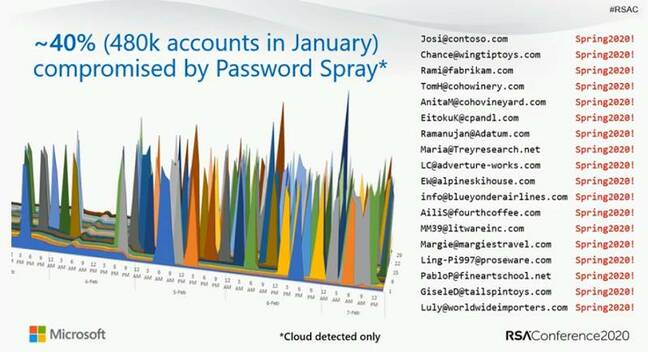
How do these attacks happen? About 40 per cent are what Microsoft calls password spray attacks. Attackers use a database of usernames and try logging in with statistically probable passwords, such as “123” or “p@ssw0rd”. Most fail but some succeed. A further 40 per cent are password replay attacks, where attackers mine data breaches on the assumption that many people reuse passwords and enterprise passwords in non-enterprise environments. That leaves 20 per cent for other kinds of attacks like phishing.
The key point, though, is that if an account is compromised, said Weinert, “there’s a 99.9 per cent chance that it did not have MFA [Multi Factor Authentication]”. MFA is where at least one additional identifier is required when logging in, such as a code on an authenticator application or a text message to a mobile phone. It is also possible (and preferable) to use FIDO2 security keys, a feature now in preview for Azure AD. Even just disabling legacy authentication helps, with a 67 per cent reduction in the likelihood of compromise.