SINGAPORE – In a move to help the international community combat the coronavirus pandemic, the Government will be making the software for its contact-tracing application TraceTogether, which has already been installed by more than 620,000 people, freely available to developers around the world.
In a Facebook post on Monday (March 23), Minister-in-charge of the Smart Nation Initiative Vivian Balakrishnan said that the app, developed by the Government Technology Agency (GovTech) and the Ministry of Health, will be open-sourced.
This means that the software’s source code will be made freely available and may be redistributed and modified.
“We believe that making our code available to the world will enhance trust and collaboration in dealing with a global threat that does not respect boundaries, political systems or economies,” said Dr Balakrishnan, who is also Foreign Minister.
“Together, we can make our world safer for everyone.”
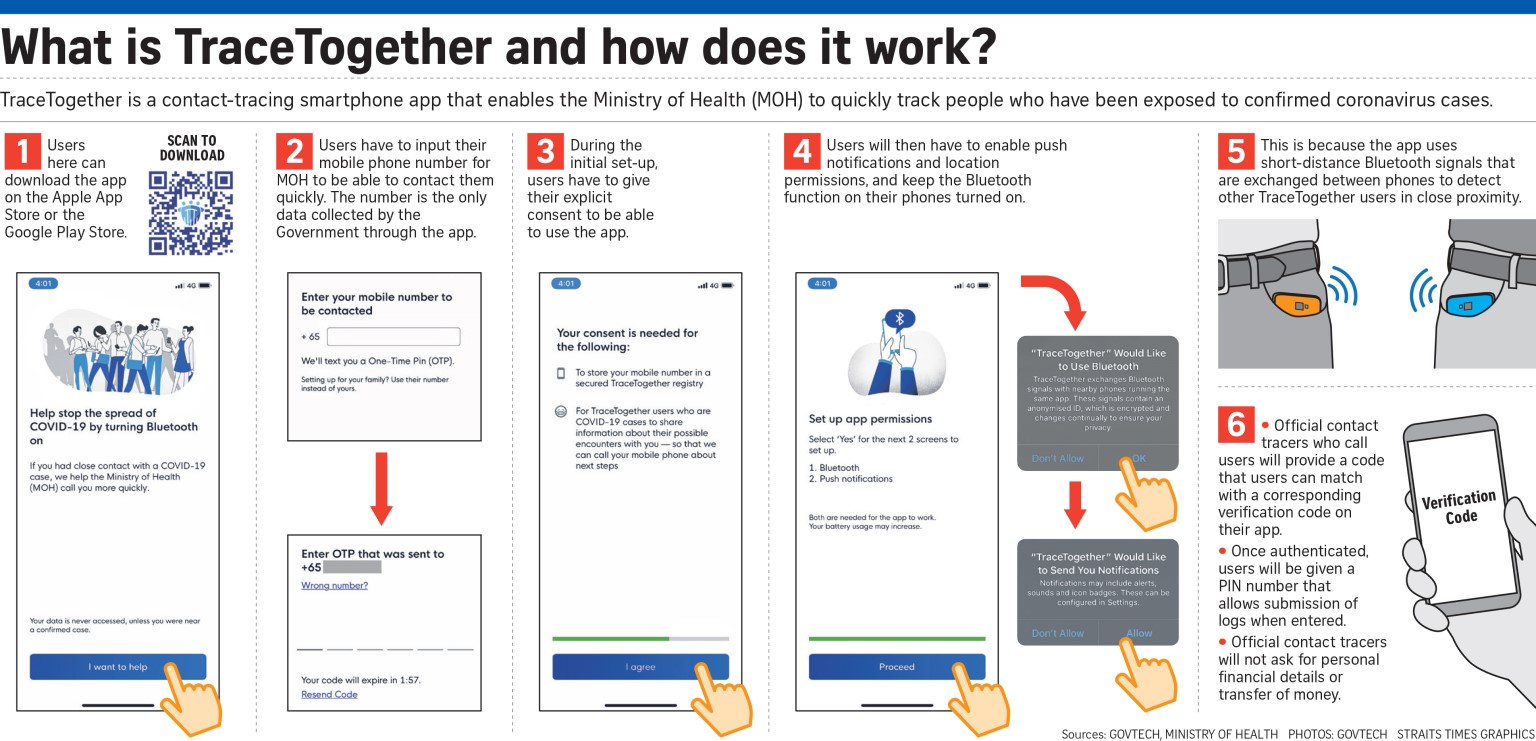
Launched last Friday, the TraceTogether app can identify people who have been within 2m of coronavirus patients for at least 30 minutes, using wireless Bluetooth technology. Its developers say the app is useful when those infected cannot recall whom they had been in close proximity with for an extended duration.
For the app to start tracing, the Bluetooth setting on mobile phones has to be turned on.
If a user gets infected, the authorities will be able to quickly find out the other users he has been in close contact with, allowing for easier identification of potential cases and helping curb the spread of the virus.
Official contact tracers will provide a code that users can match with a corresponding verification code on their app. Once authenticated, users will get a PIN that allows data to be submitted.
Contact tracers will not ask for any personal financial details or request that money be transferred over the phone.
In his post on Monday, Dr Balakrishnan said that the GovTech team was working “around the clock” to finalise documents to allow others to use the BlueTrace protocol – the building blocks of the TraceTogether app. He added that TraceTogether has been installed by more than 620,000 users so far.
Dr Janil Puthucheary, Minister-in-charge of GovTech, also weighed in on the app in a radio show on Monday, saying that a team of about 40 engineers spent more than 10,000 man-hours developing TraceTogether.
Dr Janil also encouraged more people to download TraceTogether as added protection.
TraceTogether’s developers uploaded a manifesto for BlueTrace on the app’s website on Monday, calling for international adoption of contact-tracing solutions in today’s globalised world as weapons to turn the tide against the Covid-19 outbreak.
“Covid-19 and other novel viruses do not respect national boundaries. Neither should humanity’s response. In a globalised world, with high volumes of international travel, any decentralised contact-tracing solution will need mass adoption to maximise network effects,” stated the app developers’ manifesto.
Interested parties can contact the TraceTogether team via e-mail or check this website for more information.