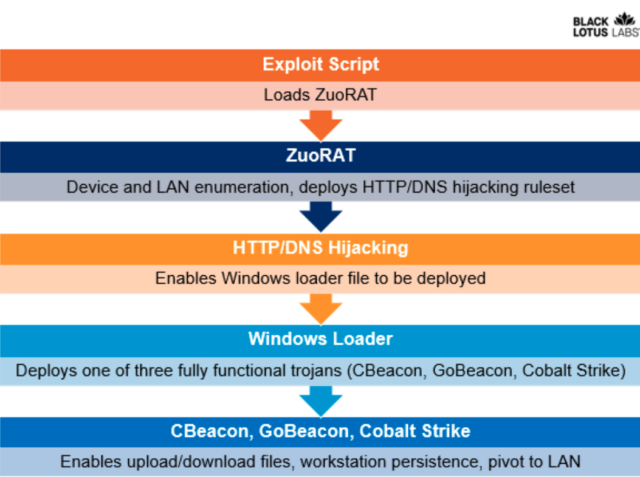
Numerous companies, including Facebook, Marketo, Olytics, and HubSpot, utilize custom URL query parameters to track clicks on links.
For example, Facebook appends a fbclid query parameter to outbound links to track clicks, with an example of one of these URLs shown below.
https://www.example.com/?fbclid=IwAR4HesRZLT-fxhhh3nZ7WKsOpaiFzsg4nH0K4WLRHw1h467GdRjaLilWbLsWith the release of Firefox 102, Mozilla has added the new ‘Query Parameter Stripping’ feature that automatically strips various query parameters used for tracking from URLs when you open them, whether that be by clicking on a link or simply pasting the URL into the address bar.
Once enabled, Mozilla Firefox will now strip the following tracking parameters from URLs when you click on links or paste an URL into the address bar:
- Olytics: oly_enc_id=, oly_anon_id=
- Drip: __s=
- Vero: vero_id=
- HubSpot: _hsenc=
- Marketo: mkt_tok=
- Facebook: fbclid=, mc_eid=
[…]
To enable Query Parameter Stripping, go into the Firefox Settings, click on Privacy & Security, and then change ‘Enhanced Tracking Protection’ to ‘Strict.’
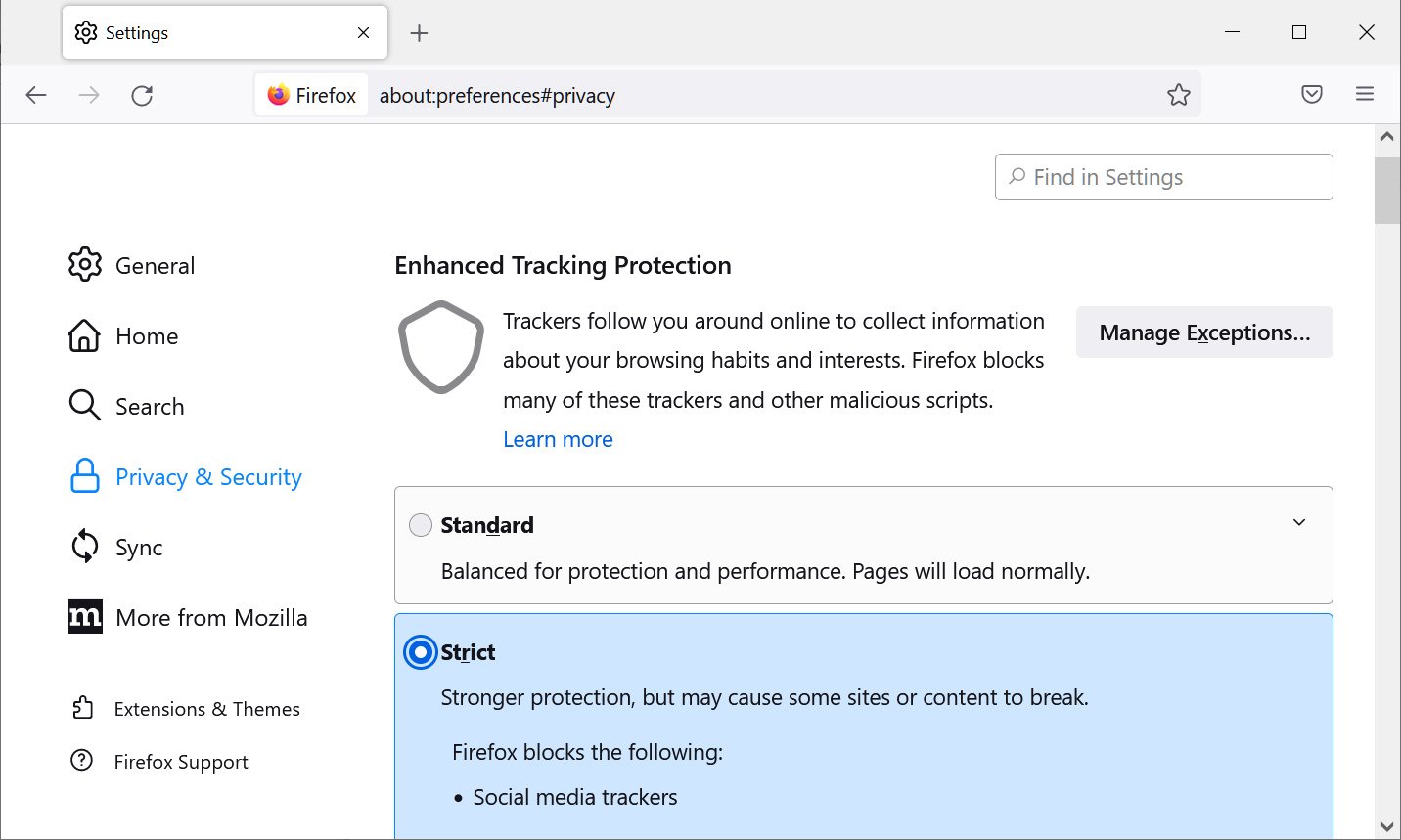
Source: BleepingComputer
However, these tracking parameters will not be stripped in Private Mode even with Strict mode enabled.
To also enable the feature in Private Mode, enter about:config in the address bar, search for strip, and set the ‘privacy.query_stripping.enabled.pbmode‘ option to true, as shown below.
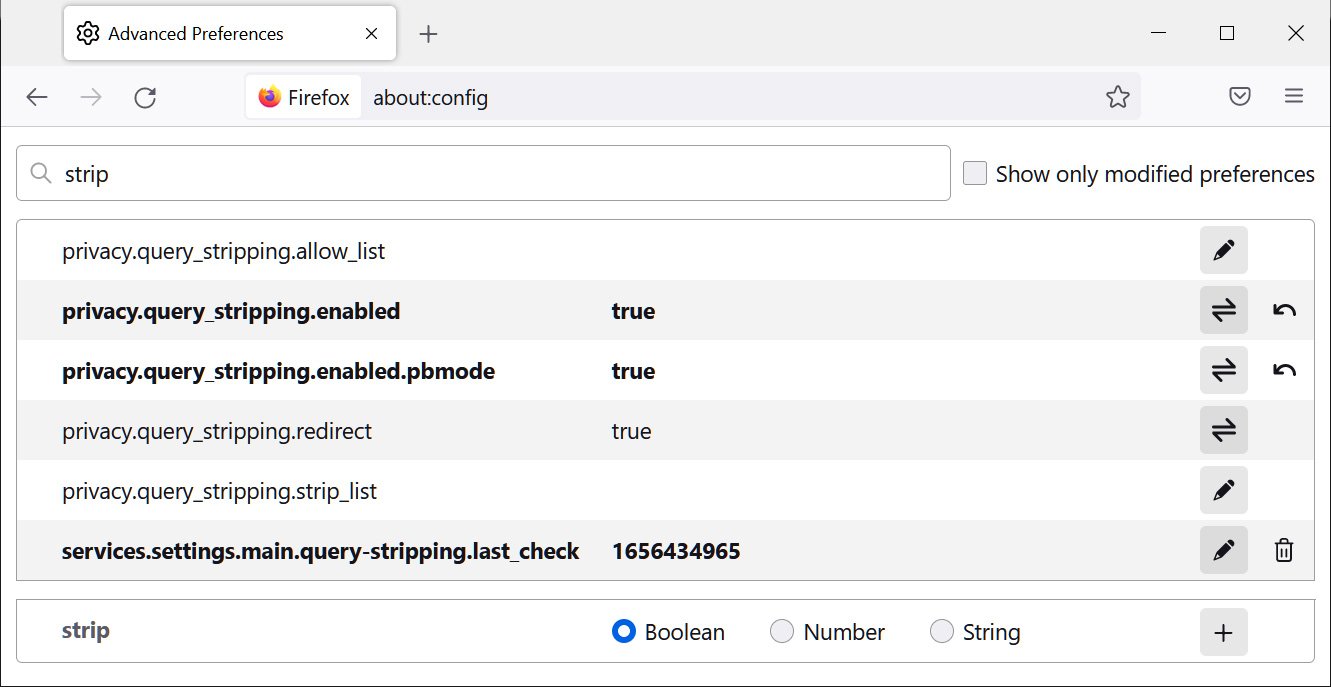
Source: BleepingComputer
It should be noted that setting Enhanced Tracking Protection to Strict could cause issues when using particular sites.
If you enable this feature and find that sites are not working correctly, just set it back to Standard (disables this feature) or the Custom setting, which will require some tweaking.
Source: New Firefox privacy feature strips URLs of tracking parameters