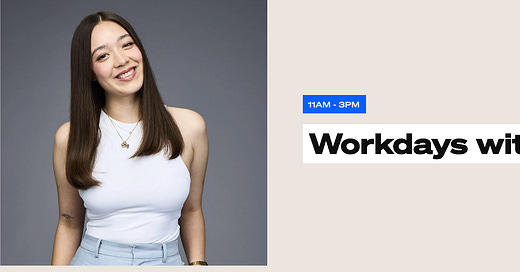
I got an interesting tipoff the other day that Sydney radio station CADA is using an AI avatar instead of an actual radio host.
The story goes that their workdays presenter – a woman called Thy – actually doesn’t exist. She’s a character made using AI, and rolled out onto CADA’s website.
[…]
What is Thy’s last name? Who is she? Where did she come from? There is no biography, or further information about the woman who is supposedly presenting this show.
Compare that to the (recently resigned) breakfast presenter Sophie Nathan or the drive host K-Sera. Both their show pages include multi-paragraph biographies which include details about their careers and various accolades. They both have a couple of different photos taken during various press shoots.
But perhaps the strangest thing about Thy is that she appears to be a young woman in her 20s who has absolutely no social media presence. This is particularly unusual for someone who works in the media, where the size of your audience is proportionate to your bargaining power in the industry.
There are no photos or videos of Thy on CADA’s socials, either. It seems she was photographed just once and then promptly turned invisible.
[…]
I decided to listen back to previous shows, using the radio archiving tool Flashback. Thy hasn’t been on air for the last fortnight. Before then, the closest thing to a radio host can be found just before the top of the hour. A rather mechanical-sounding female voice announces what songs are coming up. This person does not give her name, and none of the sweepers announce her or the show.
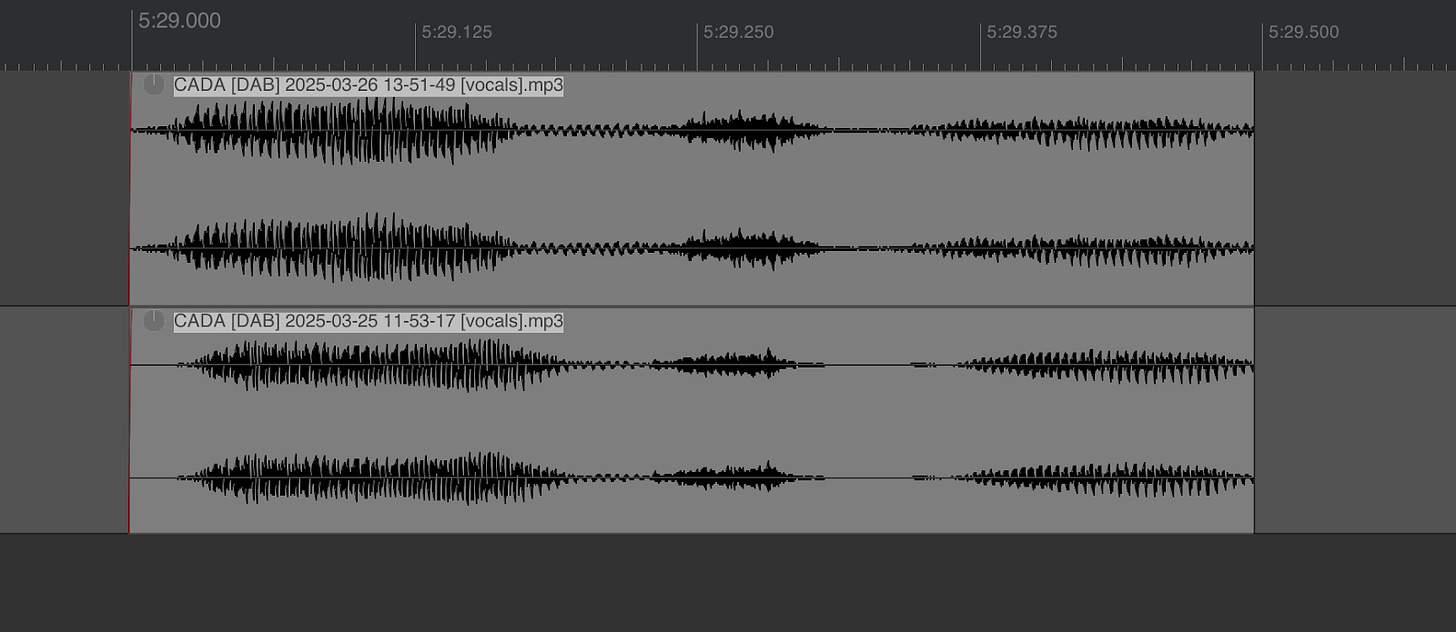
I noticed that on two different days, Thy announced ‘old school’ songs. On the 25th it was “old school Beyonce”, and then on the 26th it was “old school David Guetta”. Across two different days, the intonation was, I thought, strikingly similar.
To illustrate the point, I isolated the voice, and layered them on to audio tracks. There is a bit of interference from the imperfectly-removed song playing underneath the voice, but the host sounds identical in both instances.
Despite all this evidence, there’s still is a slim chance that Thy is a person. She might be someone who doesn’t like social media and is a bit shy around the office. Or perhaps she’s a composite of a couple of real people: someone who recorded her voice to be synthesised, another who’s licensing her image.
[…]
Source: Meet Thy – the radio host I don’t think exists
[…] An ARN spokesperson said the company was exploring how new technology could enhance the listener experience.
“We’ve been trialling AI audio tools on CADA, using the voice of Thy, an ARN team member. This is a space being explored by broadcasters globally, and the trial has offered valuable insights.”
However, it has also “reinforced the power of real personalities in driving compelling content”, the spokesperson added.
The Australian Financial Review reported that Workdays with Thy has been broadcast on CADA since November, and was reported to have reached at least 72,000 people in last month’s ratings.
[….]
CADA isn’t the first radio station to use an AI-generated host. Two years ago, Australian digital radio company Disrupt Radio introduced its own AI newsreader, Debbie Disrupt.
Source: AI host: ARN radio station CADA called out for failing to disclose AI host
Now both of these articles go off the rails about using AI and saying that the radio station should have disclosed that they were using an AI. There is absolutely no legal obligation to disclose this and I think it’s pretty cool that AI is progressing to the point that this can be done. So now if you want to be a broadcaster yourself you can enforce your station vision 24/7 – which you could never possibly do on your own.
ElevenLabs — a generative AI audio platform that transforms text into speech
And write, apparently. Someone needed to produce the “script” that the AI host used, which may also have had some AI involvement I suppose, but ultimately this seems to be just a glorified text to speech engine trying to cash in on the AI bubble. Or maybe they took it to the next logical step and just feed it a playlist and it generates the necessary “filler” from that and what it can find online from a search of the artist and title, plus some randoms chit chat from a (possibly) curated list of relevant current affairs articles.
Frankly, if people couldn’t tell for six months, then whatever they are doing is clearly good enough and the smarter radio DJs are probably already thinking about looking for other work or adding more interactive content like interviews into their shows. Talk Show type presenters probably have a little longer, but it’s probably just a matter of time for them too.
Source: https://radio.slashdot.org/comments.pl?sid=23674797&cid=65329681