At the heart of Walled Culture the book (free digital versions available) lies the dispiriting saga of how the EU Copyright Directive came into being. It began in early 2013 with the usual “stakeholder dialogue”, in which the European Commission sought the views of the various constituencies affected. It generated an unprecedentedly large response that was surprising given the dry and dusty nature of copyright law. As the European Commission’s Report on the consultation noted:
The public consultation generated broad interest with more than 9,500 replies to the consultation document and a total of more than 11,000 messages, including questions and comments, sent to the Commission’s dedicated email address. A number of initiatives were also launched by organized stakeholders that nurtured the debate around the public consultation and drew attention to it.
Some 5,600 citizens took the trouble to respond, despite the lack of an easy online interface to do so: responses required a document to be completed then emailed. Numerous problems with the existing copyright system were raised, particularly in the light of the shift from analogue to digital technologies. Despite that welcome engagement, and the many substantive issues that were raised, the public’s comments and concerns were almost entirely ignored in the final result of the legisltative process. Instead, the EU Copyright Directive gave yet more rights to copyright holders, and undermined the freedom of speech and privacy rights of ordinary people.
[…]
The standard mechanism for giving the copyright world what it wants, while pretending to respect democratic processes, has been set in motion again. The European Commission has just launched a “Call for Evidence in view of the assessment of the Recommendation on combatting online piracy of sports and other live events”. The Recommendation referred to there was published two years ago. It explores the unauthorised retransmissions of live sports and other live events online, the next battleground for the copyright world, ever-keen to expand its rights and powers.
[…]
Those further measures are likely to involve yet more one-sided legislation in favour of the copyright world, as with the EU Copyright Directive. Such laws are already being discussed in the US. But there is a significant difference between what happened back in 2013, and the latest call for evidence. In 2013, people were warning about the possible effects of various bad policy options that might be adopted. The copyright world naturally dismissed those concerns as fear mongering, which allowed its allies within the European Parliament to push through precisely those bad policy options in the final text of the Directive.
But when it comes to unauthorised retransmissions of live events, we already have a wealth of evidence of how disproportionate attempts to rein in such streams can be harmful. The main example of what not to do comes from Italy, whose Piracy Shield is shaping up to be the worst copyright enforcement scheme since France’s Hadopi (also discussed in detail in Walled Culture the book).
The central problem is overblocking. For example, back in March last year, Walled Culture reported that one of Cloudflare’s Internet addresses had been blocked by Piracy Shield. There were over 40 million domains associated with the blocked address. Compounding the problem is a lack of transparency about which sites are being blocked, and the failure to provide a rigorous and rapid complaint procedure for fixing such far-reaching blunders. […] the damage could easily go well beyond the inconvenience of millions of people being blocked from accessing their files on Google Drive, as happened last year.
[…]
Despite these serious issues, Italy seems determined to make Piracy Shield even worse by building it out in a number of ill-advised ways, including the extension of blackout orders to VPNs and public DNS providers, and the obligation for search engines to de-index sites. Worryingly, a new “Study on the Effectiveness and the Legal and Technical Means of Implementing Website-Blocking Orders” from the World Intellectual Property Organisation (WIPO) holds up Italy’s approach as an example of a “well-functioning site-blocking system”.
Nor is Italy alone in demonstrating the harms this approach to dealing with unauthorised rebroadcasts of sports events gives rise to. In Spain, attempts by La Liga, the country’s top professional football league, to tackle the problem have also led to overblocking,
[…]
German ISPs have been implementing a secret block list of allegedly infringing sites, including those offering streams, for years, and without any court oversight. The lack of transparency of this approach was underlined when the list was accidentally exposed before being hidden away once more.
As the above makes clear, the blocking of allegedly infringing streaming sites is already happening across the EU in an uncontrolled way, and with little to no effective judicial oversight. The copyright industry can present this as a kind of fait accompli, and ask the EU to bring in laws to formalise the situation. In doing so, they will skirt over the numerous and deep-seated problems with this approach, not least overblocking, which shuts down entirely innocent sites and offers little or no redress for the harm this causes.
The latest Call for Evidence on this important area is open until 28 May 2025. It would be good if companies, organisations and individuals could use this opportunity to alert the European Commission to the evident dangers of Piracy Shield and similar approaches, in the hope that existing implementations might be dismantled, or at least reined in, and new ones restricted.
[…]
French courts too are ordering Cloudflare to block streaming sites, […]

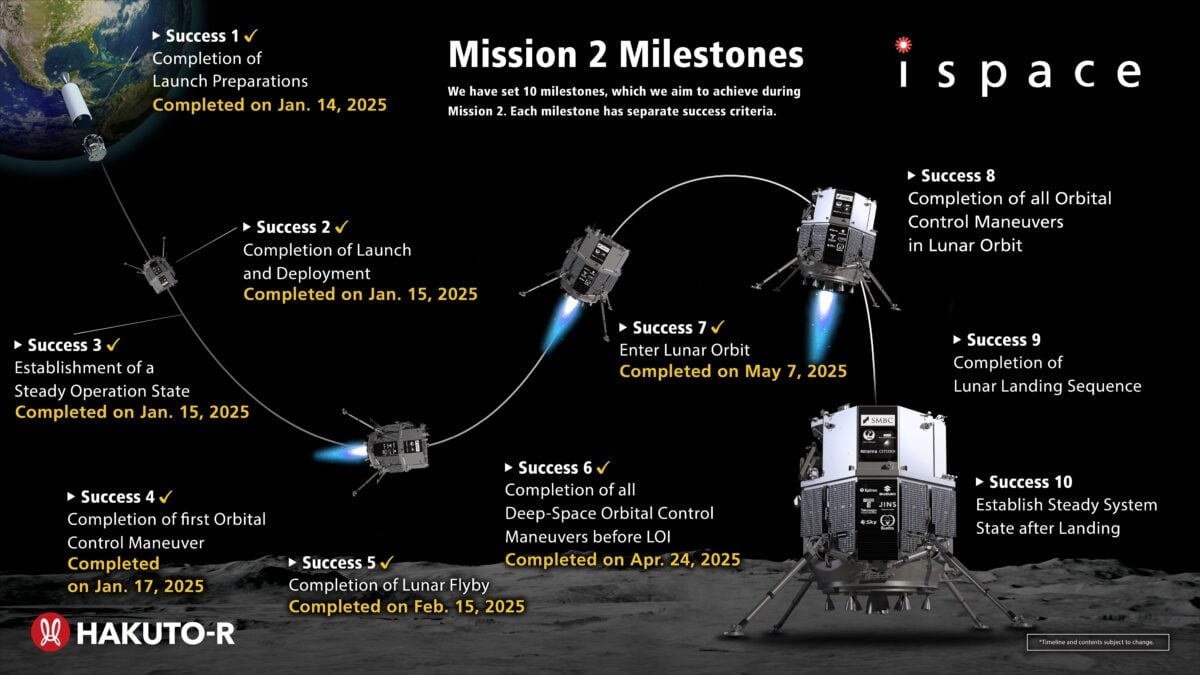 RESILIENCE was launched on January 15th, 2025, at 12:44 p.m. PST (03:44 p.m. EST)
RESILIENCE was launched on January 15th, 2025, at 12:44 p.m. PST (03:44 p.m. EST)