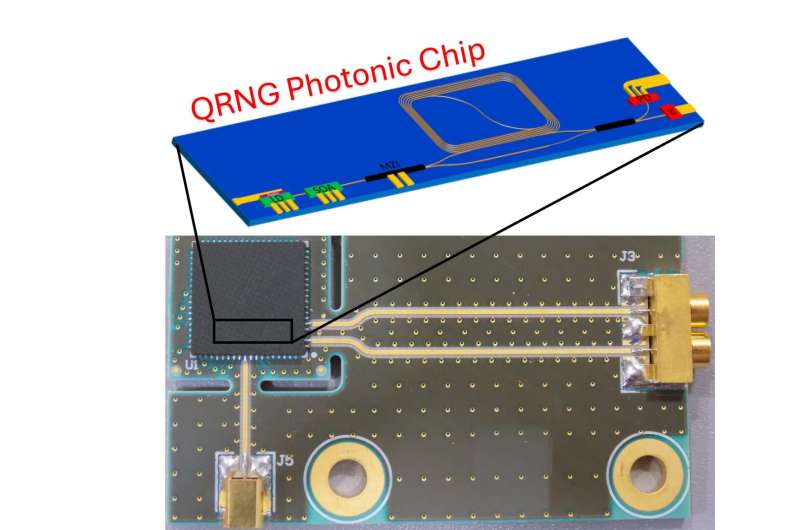
Researchers have developed a chip-based quantum random number generator that provides high-speed, high-quality operation on a miniaturized platform. This advance could help move quantum random number generators closer to being built directly into everyday devices, where they could strengthen security without sacrificing speed.
True randomness is essential for secure online banking, private messaging, and protecting sensitive data from hackers, and the rising need for stronger digital protection is driving fast-growing demand for high-quality random numbers generated at high speeds.
“The quantum properties of light make it possible to produce numbers that are truly random, unlike the numbers generated by computer algorithms, which only imitate randomness,” said research team leader Raymond Smith from Toshiba’s Cambridge Research Laboratory in the United Kingdom. “However, making this technology practical for real-world use requires the optical components that create these quantum effects to be as small as possible so they can fit inside other systems.”
In the journal Optica Quantum, the researchers describe a new quantum random number generator design that can recover the quantum signal even when it’s buried in noise, which has been challenging to accomplish with chip-integrated devices. The new device can generate unpredictable random numbers at a rate of 3 gigabits per second, fast enough to support the security needs of large-scale data centers.
“A major application of random number generators is in protecting sensitive data and communications using encryption keys,” said Smith. “Our technology can generate those keys at high speed and with strong security guarantees. High-speed random numbers are also critical for scientific simulations and artificial intelligence and for ensuring fairness in applications like online gaming or digital lotteries.”
[…]
Source: Quantum random number generator combines small size and high speed