HKD, a spinoff IPO with 51 employees within the space of a few days had a stock price explosion up to around $2555 per stock from around $75 starting on 28th July. No buy button was disabled (as was the case with Gamestop / $GME) and within a few days the rug was pulled on 3rd of August leading to a (current) value of around $1000. This is around the time of the very confusing $GME stock dividend split (splividend) which has caused chaos with brokers not issuing the split shares or dividend to clients with $GME stock. Redditors were caught completely flat footed by this, but the media has been blaming Reddit with headlines like the following
Newly minted meme stock darling AMTD slides after eye-popping surge – Reuters
AMTD Digital stock, HKD, is up more than 14,000% since its IPO. Is it a new meme stock? – USA Today
How a little-known stock soared 21,000% to overtake Costco – (CNN Business)The Reddit retail army is back.
As for Redditors, they are looking for the culprits
If you’re wondering why HKD is up 4500% in two weeks, it’s because the Rothschilds are involved
They are trying to frame HKD as the next GME, claiming WSB is behind it. Smells very much like mayo.
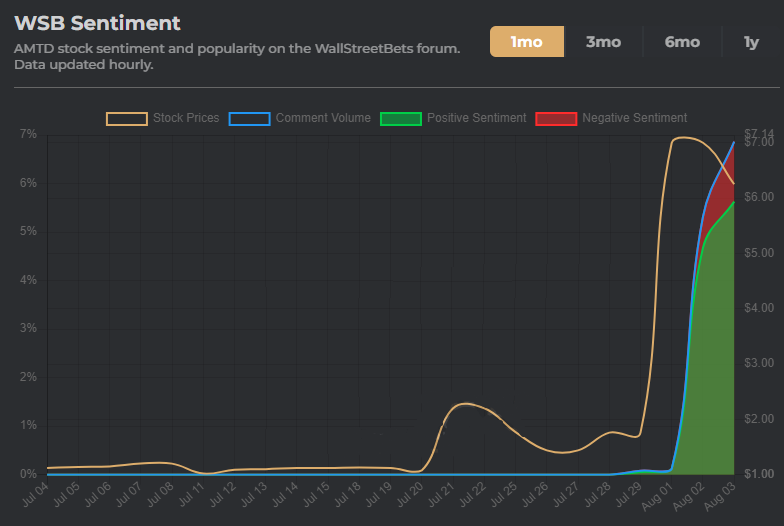
Redditors are affronted that this stock is being treated differently from $GME – a stock that was being short squeezed for no reason apart from monetary gains for huge institutional investors such as Ken Griffin and Citadel and many more.
They are also trying to figure out what it actually is that HKD actually does
You asked what HKD actually does? Ok, but this is gonna be painful…
TLDR: They took over an insurer in HK (Hong Kong) when China took over. They also bought up a couple insurers in Singapore. They may offer some fintech services and possibly a small media platform for some SE Asia internet celebs. Their “SpiderNet” is, according to them, their most profitable system. It appears to just be a business network that you have to pay to be a part of. It all sounds like a corporate crime syndicate straight out of a comic book.
They mention a “controlling shareholder” a few times, which I assume is AMTD Idea Group, a holding company. They’ve been investigated for some very fradulastic crap, which I will be writing up next. (https://hindenburgresearch.com/ebang/)
HKD, AMTD, WTF? The stock you haven’t heard of that’s up 30,000% in 2 weeks
This stock just IPO’d, is based in a foreign country, and has run 30,000% in two weeks on very low volume. Translation: Please do not read this and conclude, “Wow, what a great stock that I should definitely buy!” — That is absolutely NOT what we’re saying here
the website’s explanation of SpiderNet is extremely vague.
What can be gleaned from the website is:
- AMTD provides investment banking and asset management services to clients on an international basis
- AMTD Digital raised $125M in its New York IPO — the largest listing by a Chinese company in 2022
- It owns the SpiderNet platform
That’s really all the website explains. After digging through a few press releases, we were able to determine that the SpiderNet platform intends to provide capital and technology to digital startups, as well as provide networking services to other digital startups. In turn, SpiderNet collects a fee from its members, which is where it gets almost all of its revenue.
In short: AMTD Digital is a Hong Kong based fintech play which essentially provides loans and services to startups in exchange for fees.