Ccleaner v5.33, software that allows you to clean up the cruft that comes with use and with newly installed machines, was infected with Floxif malware which installed itself on peoples machines together with the ccleaner. Floxif is a malware downloader that gathers information about infected systems and sends it back to its Command & Control server.
[…]
The malware collected information such as computer name, a list of installed software, a list of running processes, MAC addresses for the first three network interfaces, and unique IDs to identify each computer in part. Researchers noted that the malware only ran on 32-bit systems. The malware also quit execution if the user was not using an administrator account.
Bleeping Computer: CCleaner Compromised to Distribute Malware for Almost a Month
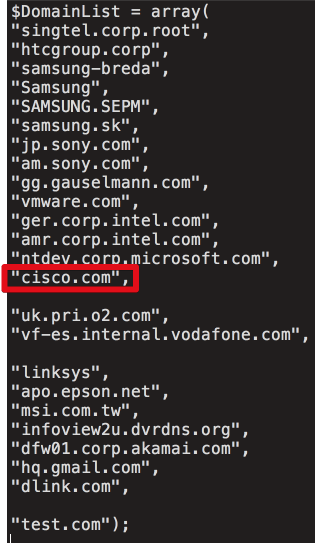
In analyzing the delivery code from the C2 server, what immediately stands out is a list of organizations, including Cisco, that were specifically targeted through delivery of a second-stage loader. Based on a review of the C2 tracking database, which only covers four days in September, we can confirm that at least 20 victim machines were served specialized secondary payloads. Below is a list of domains the attackers were attempting to target.
 Talos Intelligence: CCleaner Command and Control Causes Concern – with more technical details on the source and methodology of the malware
Talos Intelligence: CCleaner Command and Control Causes Concern – with more technical details on the source and methodology of the malware
According to Avast, the database where the CCleaner hackers were collecting data from infected hosts ran out of space and was deleted on September 12, meaning information on previous victims is now lost to investigators and the number of computers infected with the second-stage backdoor payloads may be larger than initially believed.
This means there could still be — and there certainly are — more large technology firms that currently have a backdoor on their network.
[…]
The server would store this information into a MariaDB (MySQL fork), and would run a series of filters on each infected host to determine if to send a second-stage payload, a very stealthy backdoor trojan.
Based on analysis from Cisco Talos published yesterday, the C&C server looked for computers on the networks of large tech corporations.
Based on a list recovered by researchers, targeted companies included Google, Microsoft, HTC, Samsung, Intel, Sony, VMWare, O2, Vodafone, Linksys, Epson, MSI, Akamai, DLink, Oracle (Dyn), Gauselmann, and Singtel.
The attacker’s database recorded information on all computers infected with the first and second-stage malware. There were 700,000 entries for computers infected with the first-stage malware, and only 20 for the second-stage malware.
[…]
The new information was extracted from the server’s logs and shows that the server was set up just days before attackers embedded their malware to the CCleaner binaries.
Despite the server being up for more than a month, Cisco noted that the database contained information on infections that were active between September 12 and September 16, and nothing more.
Avast says that after a deeper analysis of the logs, they find evidence that the server’s disk storage had been filled, and attackers had to delete the collected data they recorded up to that point (they most likely downloaded it before deleting it).
[…]
What this means is that data for 28 days of infections is now lost. Investigators are now unable to determine if other tech companies have now backdoors on their networks.
This means that any company that has ever deployed CCleaner on its network must now wipe systems clear, just to be sure the second-stage malware is not hidden somewhere on its network.
Bleeping computer: Info on CCleaner Infections Lost Due To Malware Server Running Out of Disk Space

 Talos Intelligence: CCleaner Command and Control Causes Concern – with more technical details on the source and methodology of the malware
Talos Intelligence: CCleaner Command and Control Causes Concern – with more technical details on the source and methodology of the malware