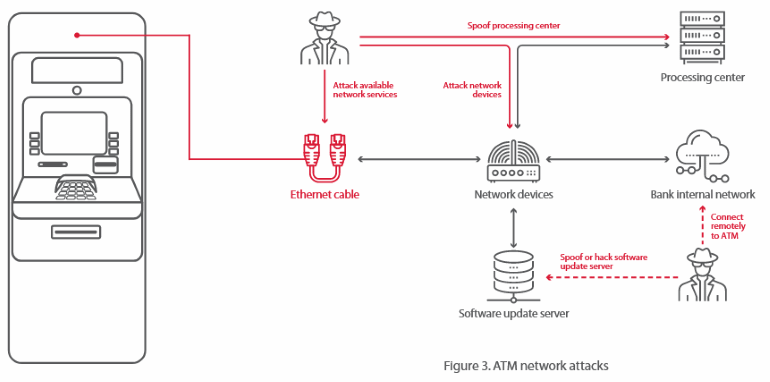
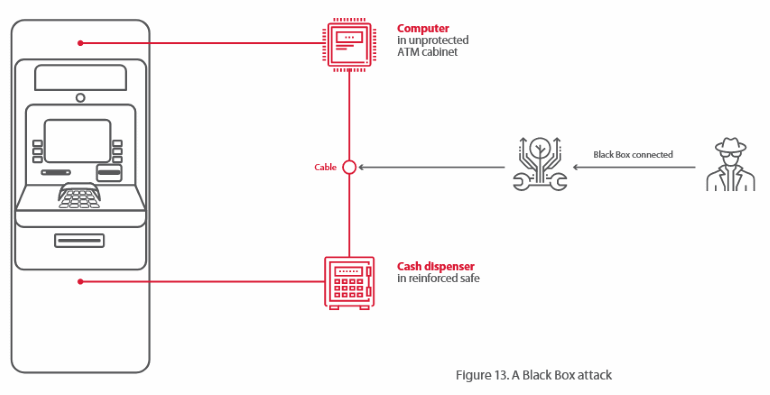
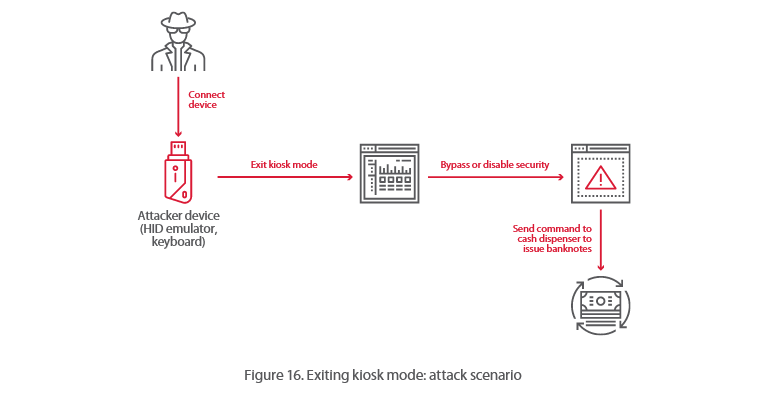
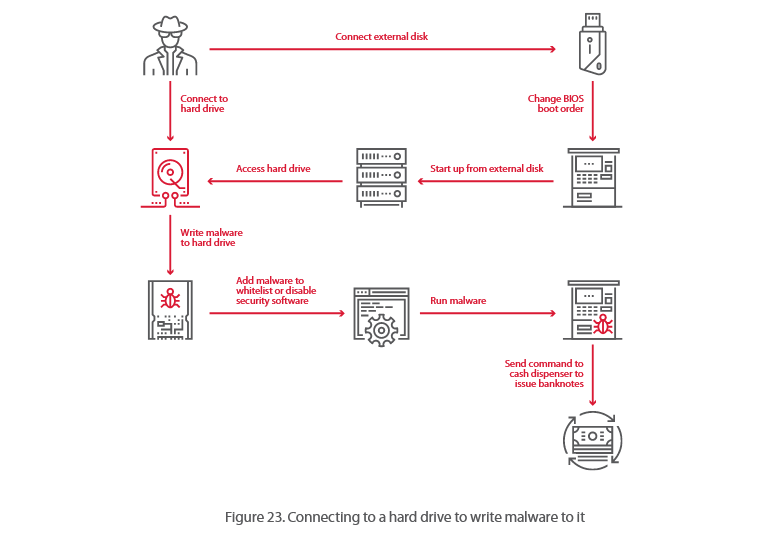
On the same day that certain types of British state-backed hacking now need a judge-issued warrant to carry out, GCHQ has lifted the veil and given the infosec world a glimpse inside its vuln-hoarding policies.
The spying agency’s internal Equities Process is the way by which it decides whether or not to tell tech vendors that its snoopers have discovered a hardware or software vulnerability.
A hot topic for many years, vuln disclosure (and patching) is a double-edged sword for spy agencies. If they keep discovered vulns to themselves, they can exploit them for their own ends, for which the public reason is given as disrupting “the activities of those who seek to do the UK harm” – including Belgian phone operators.
If GCHQ discloses vulns it has found to the affected vendor, that can “benefit global users of the technology”, in the agency’s words, as well as tending to build trust – something the Peeping Tom agency is dead keen on following the international damage done to its reputation after the Snowden disclosures.
However, in a briefing note today the agency revealed it may keep vulns in unsupported software to itself. “Where the software in question is no longer supported by the vendor,” it said, “were a vulnerability to be discovered in such software, there would be no route by which it could be patched.”
Only last year Microsoft prez Brad Smith was raging against GCHQ’s American cousins, the NSA, for the “stockpiling of vulnerabilities by governments” – though, as we revealed, Microsoft had been sitting on a pile of patches that were only provided to corporate customers and not the public, so not everyone in this debate is squeaky clean.
Lovely bureaucracy
When it decides whether or not to give up a vuln, GCHQ said three internal bodies are involved: the Equities Technical Panel, made up of “subject matter expert” spies; the GCHQ Equity Board, which is chaired by a civil servant from GCHQ’s public-facing arm, the National Cyber Security Centre (NCSC), and staffed by people from other government departments; and the Equities Oversight Committee, chaired by the chief exec of the NCSC, Ciaran Martin.
Broadly speaking, Martin gets the final word on whether or not a vuln is “released” to be patched. Those decisions are “regularly reviewed at a period appropriate to the security risk” and, regardless of the risk, “at least every 12 months”.
What do they review? Operational necessity (“How reliant are we on this vulnerability to realise intelligence?”) is one criterion, as well as the impact on other British government departments’ activities. Questions about whether the vuln could be spotted independently by others and used to harm business and private citizens is considered under the general category of “defensive risk”, but appears to be less of a priority than looking at whether the state will find its wings clipped as a result of disclosure.
Even then, the agency would rather nudge industry into applying “configuration changes” to mitigate against vulns rather than seeing a proper patch deployed after disclosure. The reason is obvious: not everyone implements config changes, meaning some GCHQ targets may continue to be vulnerable to “network exploitation”.
“Assessment in relation to a number of these factors is based on standardised criteria and past experience, including applying the use of the Common Vulnerability Scoring System where appropriate,” said GCHQ.
Good stuff, now go and get a proper warrant
Today a post-Snowden legal tweak comes into force: state employees wanting to hack targets’ networks and devices must now get a judge-issued warrant, under section 106 of the Investigatory Powers Act.
“Such warrants can then be issued from 5th December. However unless urgent, the warrant will need to be reviewed and approved by a Judicial Commissioner,” noted the Society for Computers and Law in an update about the new law. It added that from January, law enforcement agencies will have to use this process to insert probes into suspected hackers’ gear.
Using hacking tools to investigate alleged crimes that fall under sections 1 to 3 of the Computer Misuse Act 1990 is now subject to the “equipment interference warrant” procedure, rather than the bog-standard Police Act 1997 “property interference authorisation”.
The difference is that state-backed hackers set out to find “communications, private information or equipment data”, which therefore needs a different set of legal protections than the Police Act process, which was written around slightly different scenarios such as planting tracker bugs on cars. ®
Bootnote
“In exceptional cases, the CEO of the NCSC may decide that further escalation via submissions to Director GCHQ and, if required, the Foreign Secretary should be invoked,” said the GCHQ press briefing note, giving rise to images of spy agency suits pacing in circles around a smoking server and chanting Jeremy Hunt’s name, falling to their knees in gratitude when the mystical foreign secretary himself appears in a flash of lightning, ready to dispense vuln-disclosing justice.
We encourage GCHQ-based readers to send us videos of this process if this is actually what goes on.
Source: GCHQ opens kimono for infosec world to ogle its vuln disclosure process • The Register