Security researchers say the Diameter protocol used with today’s 4G (LTE) telephony and data transfer standard is vulnerable to the same types of vulnerabilities as the older SS7 standard used with older telephony standards such as 3G, 2G, and earlier.
Both Diameter and SS7 (Signaling System No. 7) have the same role in a telephony network. Their purpose is to serve as an authentication and authorization system inside a network and between different telephony networks (providers).
SS7 was developed in the 1970s and has been proven insecure for almost two decades [1, 2, 3, 4, 5]. Because of this, starting with the rollout of 4G (LTE) networks, SS7 was replaced with the Diameter protocol, an improved inter and intra-network signaling protocol that’s also slated to be used with the upcoming 5G standard.
The difference between these two is that while SS7 did not use any type of encryption for its authentication procedures, leading to the easy forgery of authentication and authorization messages, Diameter supports TLS/DTLS (for TCP or SCTP, respectively) or IPsec.
4G operators often misconfigure Diameter
But according to research published last month by Positive Technologies detailing Diameter’s use among mobile networks across the globe, the protocol’s features are rarely used.
In practice telecom operators almost never use encryption inside the network, and only occasionally on its boundaries. Moreover, encryption is based on the peer-to-peer principle, not end-to-end. In other words, network security is built on trust between operators and IPX providers.
The incorrect use of Diameter leads to the presence of several vulnerabilities in 4G networks that resemble the ones found in older networks that use SS7, and which Diameter was supposed to prevent.
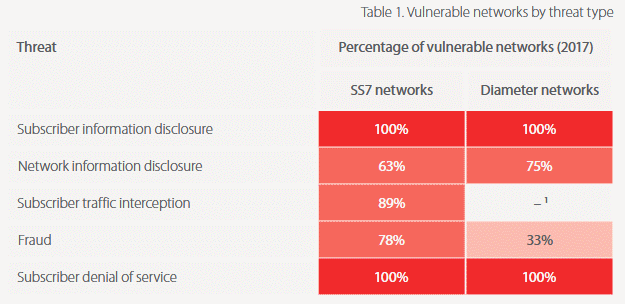
Researchers say that the Diameter misconfigurations they’ve spotted inside 4G networks are in many cases unique per each network but they usually repeat themselves to have them organized in five classes of attacks: (1) subscriber information disclosure, (2) network information disclosure, (3) subscriber traffic interception, (4) fraud, and (5) denial of service.
1+2) Subscriber and network information disclosure
The first two, subscriber and network information disclosure, allow an attacker to gather operational information about the user’s device, subscriber profile, and information about the mobile network in general.
Such vulnerabilities can reveal the user’s IMSI identifier, device addresses, network configuration, or even his geographical location —helping an attacker track users of interest as they move about.
3) Subscriber traffic interception
The third vulnerability, subscriber traffic interception, is only theoretically possible because both SMS and call transmission often establish channels with previous-generation protocols that do not use the Diameter protocol for authentication.
Nonetheless, Positive Technologies researchers warn that if the attacker is set on SMS and call interception, he can at any time downgrade a Diameter-capable 4G connection to a previous-generation connection and use flaws in SS7 and other protocols to carry out his attack.
For example, SMS interception is possible because most 4G networks send SMS messages via a 3G channel where SS7 is used instead of Diameter for user and network authentication, while phone call channels are handled via VoLTE, a protocol that has been proven insecure and susceptible to such attacks in 2015.
Even if networks handle SMS and phone calls via a pure 4G channel, then the attacker only needs to pose as an inferior network to carry out a MitM attack via an older protocol.
4) Fraud
Attackers can also use Diameter flaws to allow free use of the mobile network for a specific subscriber profile, leading to financial losses for the operator.
There are two types of such attacks, each of which is based on modifying the subscriber profile. The first type involves modifying the billing parameters stored in the subscriber profile and is quite difficult to implement in practice, since it requires knowledge of the operator’s network configuration on the part of the attacker. The values of these parameters are not standardized and depend on the specific operator; they could not be retrieved from a subscriber profile in any of the tested networks. The second type of attack is the use of services beyond restrictions, causing direct financial damage to the operator.
5) Denial of service attacks
Last but not least, Diameter flaws allow denial-of-service attacks that prevent a 4G user from accessing certain 4G features or allow an attacker to limit the speed of certain features, causing problems for a connected device.
Positive Technologies experts warn that the denial-of-service Diameter vulnerabilities “could lead to sudden failure of ATMs, payment terminals, utility meters, car alarms, and video surveillance.”
This is because these types of devices often use 4G SIM card modules to connect to their servers when located in a remote area where classic Internet connections are not possible.
All mobile networks are vulnerable to either SS7 or Diameter flaws
The cyber-security firm says that from all the mobile networks it analyzed in the past years, since it began looking into SS7 and Diameter vulnerabilities, all mobile networks it examined are vulnerable to one or another, or both, leading to unique cases where any mobile networks it inspected ws vulnerable to some sort of network-level hacking.

Positive Technologies warns that with the rise of Internet of Things devices, some of which rely on 4G connections when a WiFi network is not in range, such flaws are the equivalent of having an open door for hackers to target such equipment via the 4G network.
“Such frightening consequences are only the tip of the iceberg,” experts wrote in their latest Diameter report. The company, which is known for providing security testing and monitoring of mobile networks, urges 4G operators to get with the times and invest into the security of their networks.
The “Diameter Vulnerabilities Exposure Report 2018” is available for download here. Positive Technologies previous analyzed the SS7 protocol in 2016 and the Diameter protocol in 2017.
In March 2018, ENISA (European Union Agency for Network and Information Security) published an official advisory about SS7 and Diameter vulnerabilities in modern 4G networks.
Last week, a team of academics disclosed a set of vulnerabilities in 4G (LTE) networks at the “data layer,” the one responsible for data transfer, and not the signal level where Diameter is located at.