Name /
Pronunciation |
Abbr. |
English Name |
Genitive /
Pronunciation |
Downloads |
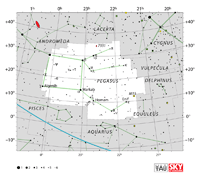
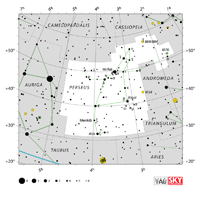
| Andromeda
an-DRAH-mih-duh |
And |
the Chained Maiden |
Andromedae
an-DRAH-mih-dee |
 Constellation charts Constellation charts
GIF (117 KB)
PDF (829 KB)
TIF
Constellation boundary
TXT (2 KB) |
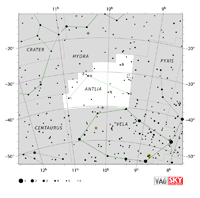
| Antlia
ANT-lee-uh |
Ant |
the Air Pump |
Antliae
ANT-lee-ee |
 Constellation charts Constellation charts
GIF (111 KB)
PDF (815 KB)
TIF
Constellation boundary
TXT (1 KB) |
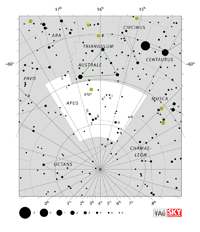
Apus
APE-us, APP-us |
Aps |
the Bird of Paradise |
Apodis
APP-oh-diss |
 Constellation charts Constellation charts
GIF (155 KB)
PDF (836 KB)
TIF
Constellation boundary
TXT (1 KB) |
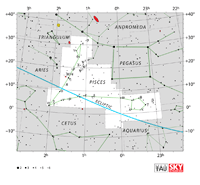
| Aquarius
uh-QUAIR-ee-us |
Aqr |
the Water Bearer |
Aquarii
uh-QUAIR-ee-eye |
 Constellation charts Constellation charts
GIF (124 KB)
PDF (879 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Aquila
ACK-will-uh, uh-QUILL-uh |
Aql |
the Eagle |
Aquilae
ACK-will-ee, uh-QUILL-ee |
 Constellation charts Constellation charts
GIF (108 KB)
PDF (820KB)
TIF
Constellation boundary
TXT (1 KB) |
| Ara
AIR-uh, AR-uh |
Ara |
the Altar |
Arae
AIR-ee, AR-ee |
 Constellation charts Constellation charts
GIF (114 KB)
PDF (807 KB)
TIF
Constellation boundary
TXT (1 KB) |
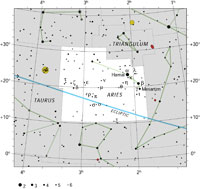
| Aries
AIR-eez, AIR-ee-yeez |
Ari |
the Ram |
Arietis
uh-RYE-ih-tiss |
 Constellation charts Constellation charts
GIF (118 KB)
PDF (805 KB)
TIF
Constellation boundary
TXT (1 KB) |
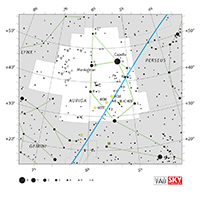
| Auriga
aw-RYE-guh |
Aur |
the Charioteer |
Aurigae
aw-RYE-ghee |
 Constellation charts Constellation charts
GIF (122 KB)
PDF (381 KB)
TIF
Constellation boundary
TXT (1 KB) |
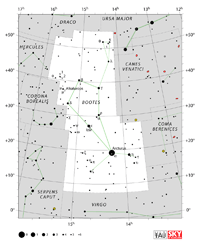
| Boötes
bo-OH-teez |
Boo |
the Herdsman |
Boötis
bo-OH-tiss |
 Constellation charts Constellation charts
GIF (147 KB)
PDF (823KB)
TIF
Constellation boundary
TXT (1 KB) |
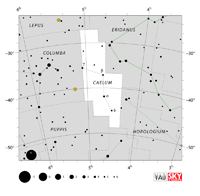
| Caelum
SEE-lum |
Cae |
the Engraving Tool |
Caeli
SEE-lye |
 Constellation charts Constellation charts
GIF (97 KB)
PDF (780 KB)
TIF
Constellation boundary
TXT (1 KB) |
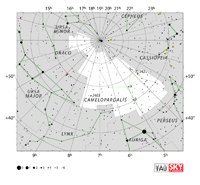
| Camelopardalis
cuh-MEL-oh- PAR-duh-liss |
Cam |
the Giraffe |
Camelopardalis
cuh-MEL-oh- PAR-duh-liss |
 Constellation charts Constellation charts
GIF (156 KB)
PDF (888 KB)
TIF
Constellation boundary
TXT (2 KB) |
| Cancer
CAN-ser |
Cnc |
the Crab |
Cancri
CANG-cry |
 Constellation charts Constellation charts
GIF (108 KB)
PDF (814 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Canes Venatici
CANE-eez (CAN-eez) ve-NAT-iss-eye |
CVn |
the Hunting Dogs |
Canum Venaticorum
CANE-um (CAN-um) ve-nat-ih-COR-um |
 Constellation charts Constellation charts
GIF (106 KB)
PDF (790 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Canis Major
CANE-iss (CAN-iss) MAY-jer |
CMa |
the Great Dog |
Canis Majoris
CANE-iss (CAN-iss) muh-JOR-iss |
 Constellation charts Constellation charts
GIF (134 KB)
PDF (849 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Canis Minor
CANE-iss (CAN-iss) MY-ner |
CMi |
the Lesser Dog |
Canis Minoris
CANE-iss (CAN-iss) mih-NOR-iss |
 Constellation charts Constellation charts
GIF (83 KB)
PDF (766 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Capricornus
CAP-rih-CORN-us |
Cap |
the Sea Goat |
Capricorni
CAP-rih-CORN-eye |
 Constellation charts Constellation charts
GIF (98 KB)
PDF (818 KB)
TIF
Constellation boundary
TXT (1 KB) |
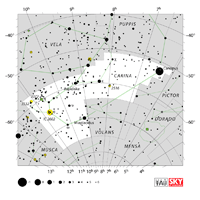
| Carina
cuh-RYE-nuh, cuh-REE-nuh |
Car |
the Keel |
Carinae
cuh-RYE-nee, cuh-REE-nee |
 Constellation charts Constellation charts
GIF (143 KB)
PDF (882 KB)
TIF
Constellation boundary
TXT (1 KB) |
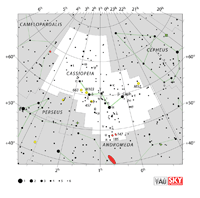
| Cassiopeia
CASS-ee-uh-PEE-uh |
Cas |
the Seated Queen |
Cassiopeiae
CASS-ee-uh-PEE-ye |
 Constellation charts Constellation charts
GIF (139 KB)
PDF (846 KB)
TIF
Constellation boundary
TXT (1 KB) |
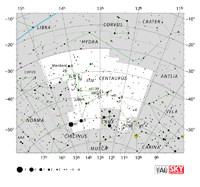
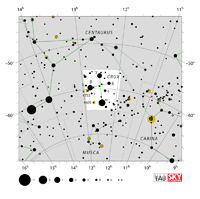
| Centaurus |
Cen |
the Centaur |
Centauri |
 Constellation charts Constellation charts
GIF (178 KB)
PDF (549 KB)
TIF
Constellation boundary
TXT (1 KB) |
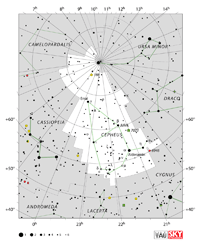
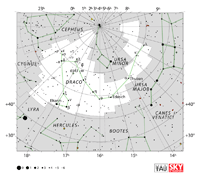
| Cepheus |
Cep |
the King |
Cephei |
 Constellation charts Constellation charts
GIF (200 KB)
PDF (873 KB)
TIF
Constellation boundary
TXT (2 KB) |
| Cetus
SEE-tus |
Cet |
the Sea Monster |
Ceti
SEE-tie |
 Constellation charts Constellation charts
GIF (122 KB)
PDF (873 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Chamaeleon
cuh-MEAL-yun, cuh-MEAL-ee-un |
Cha |
the Chameleon |
Chamaeleontis
cuh-MEAL-ee-ON-tiss |
 Constellation charts Constellation charts
GIF (183 KB)
PDF (834 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Circinus
SER-sin-us |
Cir |
the Compass |
Circini
SER-sin-eye |
 Constellation charts Constellation charts
GIF (131 KB)
PDF (818 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Columba
cuh-LUM-buh |
Col |
the Dove |
Columbae
cuh-LUM-bee |
 Constellation charts Constellation charts
GIF (99 KB)
PDF (797 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Coma Berenices
COE-muh BER-uh-NICE-eez |
Com |
the Bernice’s Hair |
Comae Berenices
COE-mee BER-uh-NICE-eez |
 Constellation charts Constellation charts
GIF (101 KB)
PDF (788 KB)
TIF
Constellation boundary
TXT (1 KB) |
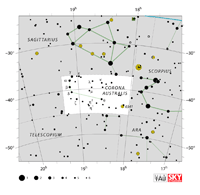
| Corona Australis
cuh-ROE-nuh aw-STRAL-iss3 |
CrA |
the Southern Crown |
Coronae Australis
cuh-ROE-nee aw-STRAL-iss3 |
 Constellation charts Constellation charts
GIF (107 KB)
PDF (787 KB)
TIF
Constellation boundary
TXT (1 KB) |
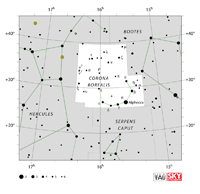
| Corona Borealis
cuh-ROE-nuh bor-ee-AL-iss3 |
CrB |
the Northern Crown |
cuh-ROE-nee bor-ee-AL-iss3 |
 Constellation charts Constellation charts
GIF (89 KB)
PDF (771 KB)
TIF
Constellation boundary
TXT (1 KB) |
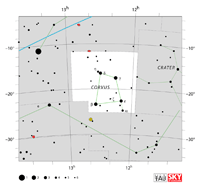
| Corvus
COR-vus |
Crv |
the Crow |
Corvi
COR-vye |
 Constellation charts Constellation charts
GIF (74 KB)
PDF (763 KB)
TIF
Constellation boundary
TXT (1 KB) |
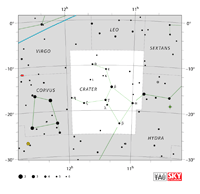
| Crater
CRAY-ter |
Crt |
the Cup |
Crateris
cruh-TEE-riss |
 Constellation charts Constellation charts
GIF (75 KB)
PDF (787 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Crux
CRUCKS, CROOKS |
Cru |
the Southern Cross |
Crucis
CROO-siss |
 Constellation charts Constellation charts
GIF (119 KB)
PDF (811 KB)
TIF
Constellation boundary
TXT (1 KB) |
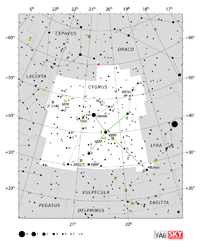
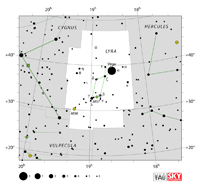
| Cygnus
SIG- SIG-nu |
Cyg |
the Swan |
Cygni
SIG-nye |
 Constellation charts Constellation charts
GIF (174 KB)
PDF (866 KB)
TIF
Constellation boundary
TXT (1 KB) |
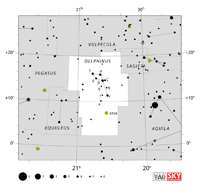
| Delphinus
del-FINE-us, del-FIN-us |
Del |
the Dolphin |
Delphini
del-FINE-eye, del-FIN-eye |
 Constellation charts Constellation charts
GIF (81 KB)
PDF (767 KB)
TIF
Constellation boundary
TXT (1 KB) |
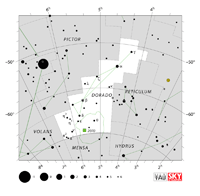
| Dorado
duh-RAH-do |
Dor |
the Swordfish |
Doradus
duh-RAH-dus |
 Constellation charts Constellation charts
GIF (108 KB)
PDF (795 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Draco
DRAY-co |
Dra |
the Dragon |
Draconis
druh-CONE-iss |
 Constellation charts Constellation charts
GIF (153 KB)
PDF (898 KB)
TIF
Constellation boundary
TXT (2 KB) |
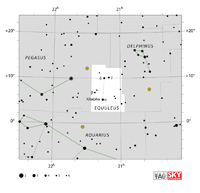
| Equuleus
eh-QUOO-lee-us |
Equ |
the Little Horse |
Equulei
eh-QUOO-lee-eye |
 Constellation charts Constellation charts
GIF (69 KB)
PDF (749 KB)
TIF
Constellation boundary
TXT (1 KB) |
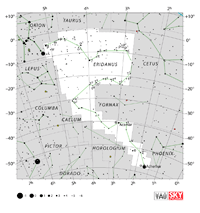
| Eridanus
ih-RID-un-us |
Eri |
the River |
Eridani
ih-RID-un-eye |
 Constellation charts Constellation charts
GIF (167 KB)
PDF (941 KB)
TIF
Constellation boundary
TXT (2 KB) |
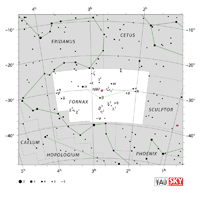
| Fornax
FOR-naks |
For |
the Furnace |
Fornacis
for-NAY-siss |
 Constellation charts Constellation charts
GIF (108 KB)
PDF (811 KB)
TIF
Constellation boundary
TXT (1 KB) |
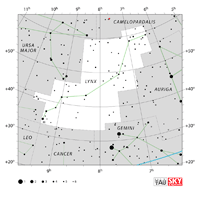
| Gemini
JEM-uh-nye, JEM-uh-nee |
Gem |
the Twins |
Geminorum
JEM-uh-NOR-um |
 Constellation charts Constellation charts
GIF (122 KB)
PDF (832 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Grus
GRUSS, GROOS |
Gru |
the Crane |
Gruis
GROO-iss |
 Constellation charts Constellation charts
GIF (127 KB)
PDF (829 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Hercules
HER-kyuh-leez |
Her |
the Hercules |
Herculis
HER-kyuh-liss |
 Constellation charts Constellation charts
GIF (156 KB)
PDF (829 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Horologium
hor-uh-LOE-jee-um |
Hor |
the Clock |
Horologii
hor-uh-LOE-jee-eye |
 Constellation charts Constellation charts
GIF (107 KB)
PDF (788 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Hydra
HIGH-druh |
Hya |
the Female Water Snake |
Hydrae
HIGH-dree |
 Constellation charts Constellation charts
GIF (127 KB)
PDF (929 KB)
TIF
Constellation boundary
TXT (2 KB) |
| Hydrus
HIGH-drus |
Hyi |
the Male Water Snake |
Hydri
HIGH-dry |
 Constellation charts Constellation charts
GIF (143 KB)
PDF (821 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Indus
IN-dus |
Ind |
the Indian |
Indi
IN-dye |
 Constellation charts Constellation charts
GIF (131 KB)
PDF (834 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Lacerta
luh-SER-tuh |
Lac |
the Lizard |
Lacertae
luh-SER-tee |
 Constellation charts Constellation charts
GIF (124 KB)
PDF (812 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Leo
LEE-oh |
Leo |
the Lion |
Leonis
lee-OH-niss |
 Constellation charts Constellation charts
GIF (142 KB)
PDF (820 KB)
TIF
Constellation boundary
TXT (1 KB) |
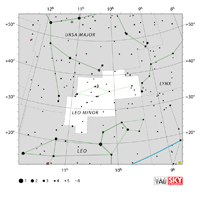
| Leo Minor
LEE-oh MY-ner |
LMi |
the Lesser Lion |
Leonis Minoris
lee-OH-niss mih-NOR-iss |
 Constellation charts Constellation charts
GIF (103 KB)
PDF (799 KB)
TIF
Constellation boundary
TXT (1 KB) |
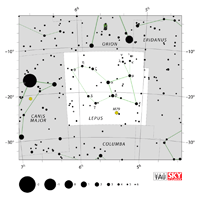
| Lepus
LEEP-us, LEP-us |
Lep |
the Hare |
Leporis
LEP-or-iss |
 Constellation charts Constellation charts
GIF (94 KB)
PDF (787 KB)
TIF
Constellation boundary
TXT (1 KB) |
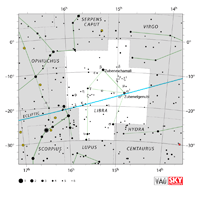
| Libra
LEE-bruh, LYE-bruh |
Lib |
the Scales |
Librae
LEE-bree, LYE-bree |
 Constellation charts Constellation charts
GIF (111 KB)
PDF (819 KB)
TIF
Constellation boundary
TXT (1 KB) |
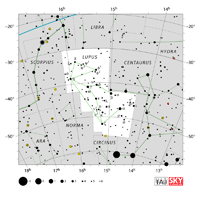
| Lupus
LOOP-us |
Lup |
the Wolf |
Lupi
LOOP-eye |
 Constellation charts Constellation charts
GIF (137 KB)
PDF (857 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Lynx
LINKS |
Lyn |
the Lynx |
Lyncis
LIN-siss |
 Constellation charts Constellation charts
GIF (111 KB)
PDF (796 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Lyra
LYE-ruh |
Lyr |
the Lyre |
Lyrae
LYE-ree |
 Constellation charts Constellation charts
GIF (91 KB)
PDF (776 KB)
TIF
Constellation boundary
TXT (1 KB) |
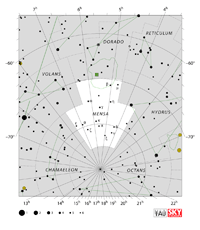
| Mensa
MEN-suh |
Men |
the Table Mountain |
Mensae
MEN-see |
 Constellation charts Constellation charts
GIF (161 KB)
PDF (827 KB)
TIF
Constellation boundary
TXT (1 KB) |
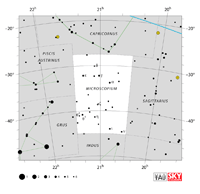
| Microscopium
my-cruh-SCOPE-ee-um |
Mic |
the Microscope |
Microscopii
my-cruh-SCOPE-ee-eye |
 Constellation charts Constellation charts
GIF (87 KB)
PDF (776 KB)
TIF
Constellation boundary
TXT (1 KB) |
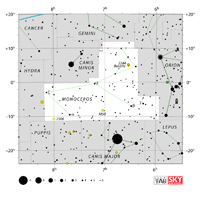
| Monoceros
muh-NAH-ser-us |
Mon |
the Unicorn |
Monocerotis
muh-NAH-ser-OH-tiss |
 Constellation charts Constellation charts
GIF (110 KB)
PDF (821 KB)
TIF
Constellation boundary
TXT (1 KB) |
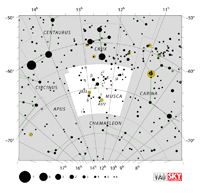
| Musca
MUSS-cuh |
Mus |
the Fly |
Muscae
MUSS-see, MUSS-kee |
 Constellation charts Constellation charts
GIF (134 KB)
PDF (828 KB)
TIF
Constellation boundary
TXT (1 KB) |
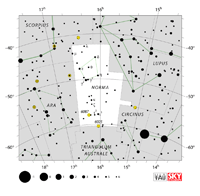
| Norma
NOR-muh |
Nor |
the Carpenter’s Square |
Normae
NOR-mee |
 Constellation charts Constellation charts
GIF (118 KB)
PDF (803 KB)
TIF
Constellation boundary
TXT (1 KB) |
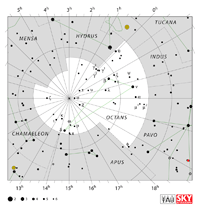
| Octans
OCK-tanz |
Oct |
the Octant |
Octantis
ock-TAN-tiss |
 Constellation charts Constellation charts
GIF (140 KB)
PDF (821 KB)
TIF
Constellation boundary
TXT (1 KB) |
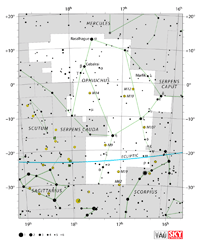
| Ophiuchus
OFF-ee-YOO-kus, OAF-ee-YOO-kus |
Oph |
the Serpent Bearer |
Ophiuchi
OFF-ee-YOO-kye, OAF-ee-YOO-kye |
 Constellation charts Constellation charts
GIF (175 KB)
PDF (854 KB)
TIF
Constellation boundary
TXT (2 KB) |
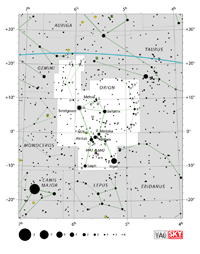
| Orion
oh-RYE-un, uh-RYE-un |
Ori |
the Hunter |
Orionis
or-eye-OH-niss |
 Constellation charts Constellation charts
GIF (181 KB)
PDF (873 KB)
TIF
Constellation boundary
TXT (1 KB) |
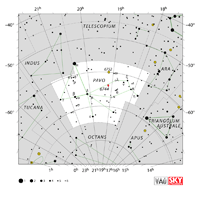
| Pavo
PAY-vo |
Pav |
the Peacock |
Pavonis
puh-VOE-niss |
 Constellation charts Constellation charts
GIF (143 KB)
PDF (859 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Pegasus
PEG-us-us |
Peg |
the Winged Horse |
Pegasi
PEG-us-eye |
 Constellation charts Constellation charts
GIF (136 KB)
PDF (868 KB)
TIF
Constellation boundary
TXT (2 KB) |
| Perseus
PER-see-us, PER-syoos |
Per |
the Hero |
Persei
PER-see-eye |
 Constellation charts Constellation charts
GIF (127 KB)
PDF (836 KB)
TIF
Constellation boundary
TXT (1 KB) |
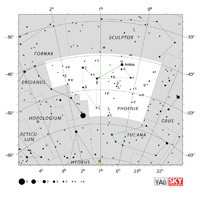
| Phoenix
FEE-nix |
Phe |
the Phoenix
|
Phoenicis
fuh-NICE-iss |
 Constellation charts Constellation charts
GIF (119 KB)
PDF (828 KB)
TIF
Constellation boundary
TXT (1 KB) |
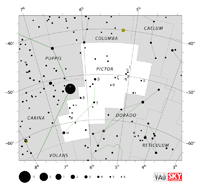
| Pictor
PICK-ter |
Pic |
the Painter’s Easel |
Pictoris
pick-TOR-iss |
 Constellation charts Constellation charts
GIF (108 KB)
PDF (794 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Pisces
PICE-eez, PISS-eez |
Psc |
the Fishes |
Piscium
PICE-ee-um, PISH-ee-um |
 Constellation charts Constellation charts
GIF (87 KB)
PDF (859 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Piscis Austrinus
PICE-iss (PISS-iss) aw-STRY-nus |
PsA |
the Southern Fish |
Piscis Austrini
PICE-iss (PISS-iss) aw-STRY-nye |
 Constellation charts Constellation charts
GIF (87 KB)
PDF (778 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Puppis
PUP-iss |
Pup |
the Stern |
Puppis
PUP-iss |
 Constellation charts Constellation charts
GIF (185 KB)
PDF (868 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Pyxis
PIX-iss |
Pyx |
the Compass |
Pyxidis
PIX-ih-diss |
 Constellation charts Constellation charts
GIF (84 KB)
PDF (775 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Reticulum
rih-TICK-yuh-lum |
Ret |
the Reticle |
Reticuli
rih-TICK-yuh-lye |
 Constellation charts Constellation charts
GIF (107 KB)
PDF (786 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Sagitta
suh-JIT-uh |
Sge |
the Arrow |
Sagittae
suh-JIT-ee |
 Constellation charts Constellation charts
GIF (90 KB)
PDF (773 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Sagittarius
SAJ-ih-TARE-ee-us |
Sgr |
the Archer |
Sagittarii
SAJ-ih-TARE-ee-eye |
 Constellation charts Constellation charts
GIF (163 KB)
PDF (878 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Scorpius
SCOR-pee-us |
Sco |
the Scorpion |
Scorpii
SCOR-pee-eye |
 Constellation charts Constellation charts
GIF (194 KB)
PDF (874 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Sculptor
SCULP-ter |
Scl |
the Sculptor |
Sculptoris
sculp-TOR-iss |
 Constellation charts Constellation charts
GIF (119 KB)
PDF (810 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Scutum
SCOOT-um, SCYOOT-um |
Sct |
the Shield |
Scuti
SCOOT-eye, SCYOOT-eye |
 Constellation charts Constellation charts
GIF (120 KB)
PDF (784 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Serpens
SER-punz |
Ser |
the Serpent |
Serpentis
ser-PEN-tiss |
 Constellation charts (Serpens Caput) Constellation charts (Serpens Caput)
GIF (112 KB)
PDF (780 KB)
TIF
Constellation boundary (Serpens Caput)
TXT (1 KB)
 Constellation charts (Serpens Cauda) Constellation charts (Serpens Cauda)
GIF (126 KB)
PDF (791 KB)
TIF
Constellation boundary (Serpens Cauda)
TXT (1 KB) |
| Sextans
SEX-tunz |
Sex |
the Sextant |
Sextantis
sex-TAN-tiss |
 Constellation charts Constellation charts
GIF (83 KB)
PDF (782 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Taurus
TOR-us |
Tau |
the Bull |
Tauri
TOR-eye |
 Constellation charts Constellation charts
GIF (115 KB)
PDF (832 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Telescopium |
Tel |
the Telescope |
Telescopii |
 Constellation charts Constellation charts
GIF (148 KB)
PDF (834 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Triangulum
try-ANG-gyuh-lum |
Tri |
the Triangle |
Trianguli
try-ANG-gyuh-lye |
 Constellation charts Constellation charts
GIF (89 KB)
PDF (764 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Triangulum Australe
try-ANG-gyuh-lum aw-STRAL-ee |
TrA |
the Southern Triangle |
Trianguli Australis
try-ANG-gyuh-lye aw-STRAL-iss |
 Constellation charts Constellation charts
GIF (124 KB)
PDF (815 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Tucana
too-KAY-nuh, too-KAH-nuh |
Tuc |
the Toucan |
Tucanae
too-KAY-nee, too-KAH-nee |
 Constellation charts Constellation charts
GIF (127 KB)
PDF (806 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Ursa Major
ER-suh MAY-jur |
UMa |
the Great Bear |
Ursae Majoris
ER-suh muh-JOR-iss |
 Constellation charts Constellation charts
GIF (174 KB)
PDF (885 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Ursa Minor
ER-suh MY-ner |
UMi |
the Little Bear |
Ursae Minoris
ER-suh mih-NOR-iss |
 Constellation charts Constellation charts
GIF (135 KB)
PDF (800 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Vela
VEE-luh, VAY-luh |
Vel |
the Sails |
Velorum
vee-LOR-um, vuh-LOR-um |
 Constellation charts Constellation charts
GIF (131 KB)
PDF (850 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Virgo
VER-go |
Vir |
the Maiden |
Virginis
VER-jin-iss |
 Constellation charts Constellation charts
GIF (98 KB)
PDF (831 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Volans
VOH-lanz |
Vol |
the Flying Fish |
Volantis
vo-LAN-tiss |
 Constellation charts Constellation charts
GIF (123 KB)
PDF (812 KB)
TIF
Constellation boundary
TXT (1 KB) |
| Vulpecula
vul-PECK-yuh-luh |
Vul |
the Fox |
Vulpeculae
vul-PECK-yuh-lee |
 Constellation charts Constellation charts
GIF (124 KB)
PDF (805 KB)
TIF
Constellation boundary
TXT (1 KB) |


 Constellation Names
Constellation Names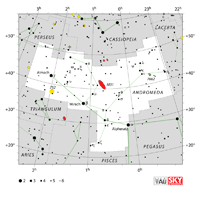
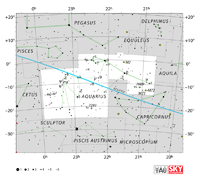
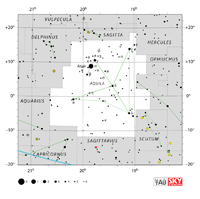
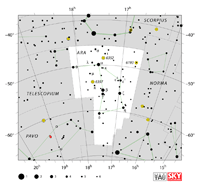
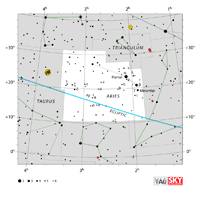

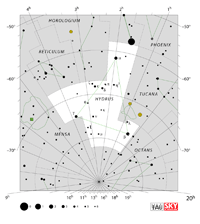
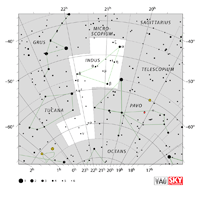
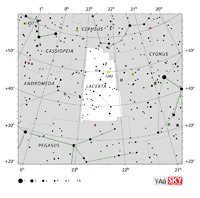
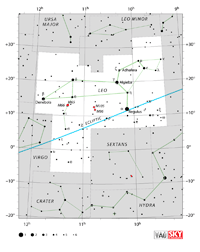
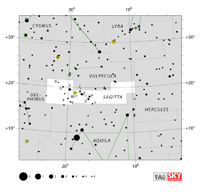
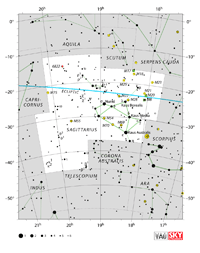
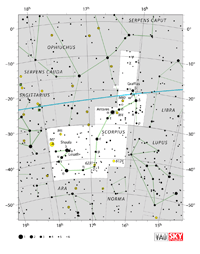
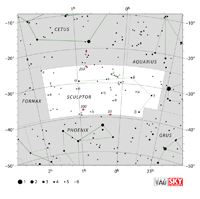
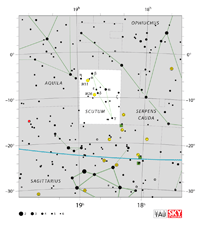
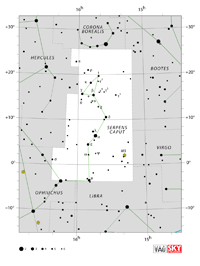
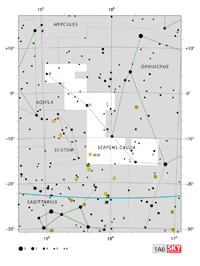
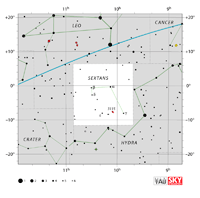
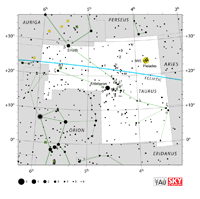
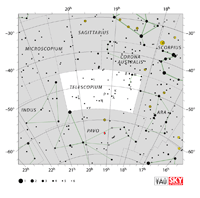
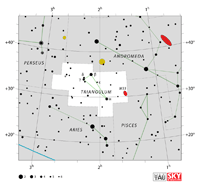
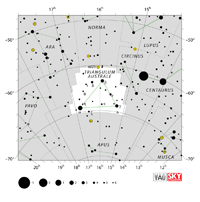
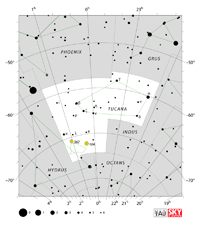
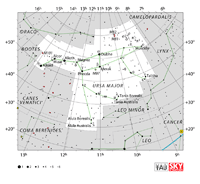
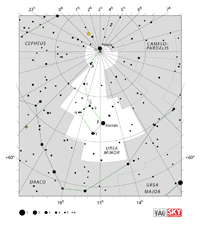
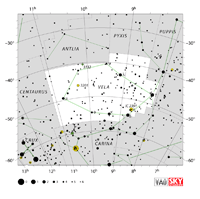
 Aquarius
Aquarius Aries
Aries