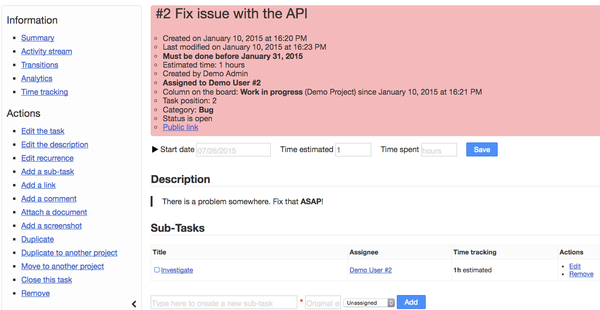
Enterprise tech distributor Arrow Inc will take a $13m charge on the chin after a fraudster posing as a company exec transferred money from the corporate bank account to an external one.
[…]
Deloitte has previously highlighted what it reckoned is the growing threat from ‘fake president frauds, “affecting many companies at the moment”.
It involves convincing an employee to make emergency bank transfers to a third party, “in order to obey an alleged order of a leader under the pretext of a debt to pay, a provision in contract or a deposit”.
Organised crims are suspected of perpetrating these scams, “with a complete knowledge regarding the market, structure and customers of the companies they are attacking”.
Source: Arrow: Fraudsters impersonated one of our execs to steal money • The Channel