The trouble with DRM is that it’s sort of ineffective. It tends to make things inconvenient for people who legitimately bought a song or movie while failing to stop piracy. Some rights holders, like Ubisoft, have come around to the idea that DRM is counterproductive. Steve Jobs famously wrote about the inanity of DRM in 2007. But other rights holders, like Netflix, are doubling down. The prevailing winds at the consortium concluded that DRM is now a fact of life, and so it would be be better to at least make the experience a bit smoother for users. If the consortium didn’t work with companies like Netflix, Berners-Lee wrote in a blog post, those companies would just stop delivering video over the web and force people into their own proprietary apps. The idea that the best stuff on the internet will be hidden behind walls in apps rather than accessible through any browser is the mortal fear for open web lovers; it’s like replacing one library with many stores that each only carry books for one publisher. “It is important to support EME as providing a relatively safe online environment in which to watch a movie, as well as the most convenient,” Berners-Lee wrote, “and one which makes it a part of the interconnected discourse of humanity.” Mozilla, the nonprofit that makes the browser Firefox, similarly held its nose and cooperated on the EME standard. “It doesn’t strike the correct balance between protecting individual people and protecting digital content,” it said in a blog post. “The content providers require that a key part of the system be closed source, something that goes against Mozilla’s fundamental approach. We very much want to see a different system. Unfortunately, Mozilla alone cannot change the industry on DRM at this point.”
Source: Corporations Just Quietly Changed How the Web Works – Slashdot
And of course it just turns out that the EU knows that piracy doesn’t hurt sales, but decided to ignore that when designing policy.
It is a big dissappointment in Tim Berners-Lee, who has caved in to the money grabbers and has now set a precedence showing that the WWW Consortium is corruptible to anyone with enough money in their pockets.
Fortunately it won’t be long before this is hacked. And another new standard has to be introduced. Given the glacial speed at which the W3C works, this might give us a few years of freedom from DRM.

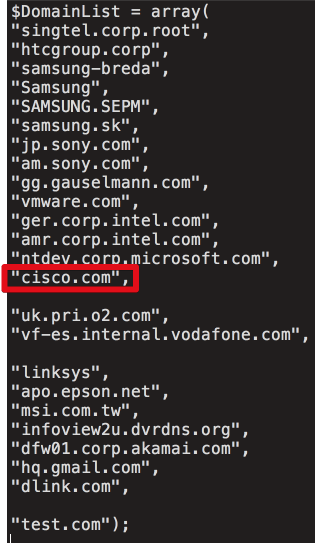 Talos Intelligence: CCleaner Command and Control Causes Concern – with more technical details on the source and methodology of the malware
Talos Intelligence: CCleaner Command and Control Causes Concern – with more technical details on the source and methodology of the malware