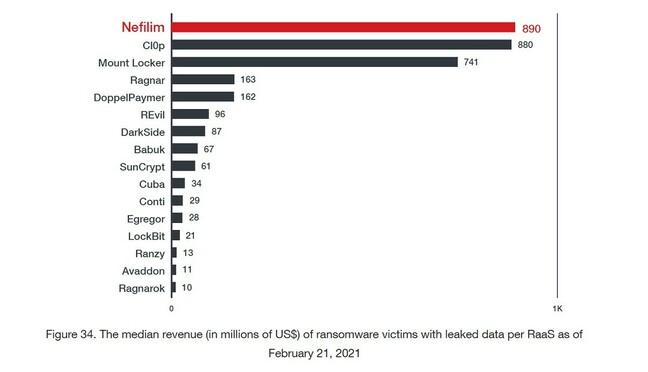
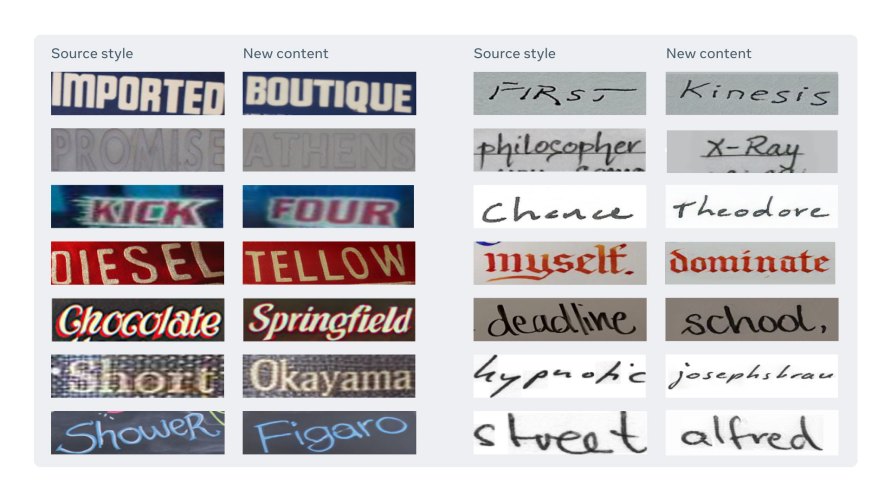
Lawmakers in the House have introduced five new bills that would place significant limits on major tech companies, including Apple, Google, Facebook and Amazon.The proposed legislation is part of a broader effort to step up antitrust enforcement against tech giants.The bills would place new limits on the companies’ ability to acquire new business and change how they treat their own services compared with competitors.
“From Amazon and Facebook to Google and Apple, it is clear that these unregulated tech giants have become too big to care and too powerful to ever put people over profit,” Rep. Pramila Jayapal said in a statement. “By reasserting the power of Congress, our landmark bipartisan bills rein in anti-competitive behavior, prevent monopolistic practices, and restore fairness and competition while finally leveling the playing field and allowing innovation to thrive.”
The bills include:
- The American Choice and Innovation Online Act: A measure that would prevent tech platforms from advantaging their own business over a competitor. Rep. David Cicilline, chair of the House Antitrust subcommittee, said the bill would prevent Amazon “from manipulating their marketplaces to promote their own products.” It could also address concerns that Apple preferences its own services in the App Store.
- The Ending Platform Monopolies Act: Co-authored by Rep. Jayapal, whose district includes Amazon, the bill targets the online retail giant. It would prevent big tech companies from “selling products in marketplaces they control.”
- The Platform Competition and Opportunity Act: The bill would prevent “dominant platforms” from acquiring companies that represent “competitive threats.” Members of Congress have previously questioned Mark Zuckerberg over Facebook’s aggressive pursuit of competitors.
- The Augmenting Compatibility and Competition by Enabling Service Switching Act of 2021 (ACCESS): The bill is meant to make it easier to “quit social media and take your data with you,” according to Cicilline.
- The ‘Merger Filing Fee Modernization Act of 2021: The bill would help the FTC and Department of Justice raise more money for antitrust enforcement by increasing the fees companies pay when requesting government approval for acquisitions.
Notably, the bills have bipartisan support, as limiting the power of big tech platforms has been a rare source of bipartisan agreement in Congress. Though the bills don’t name individual companies, the legislation could have a significant impact on Facebook, Google, Amazon and Apple, which have faced increasing scrutiny from Congress over their business practices and market dominance.
Source: House introduces five antitrust bills targeting Apple, Google, Facebook and Amazon | Engadget