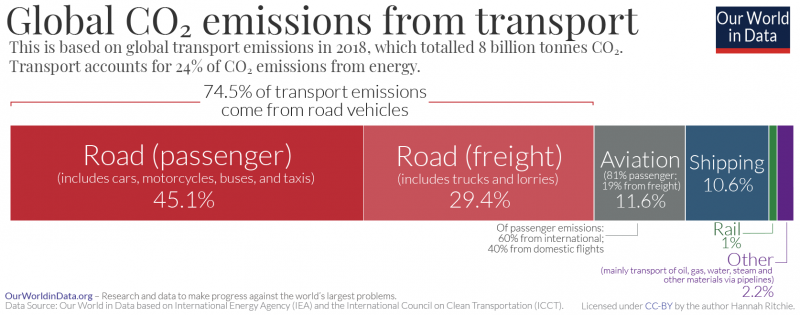
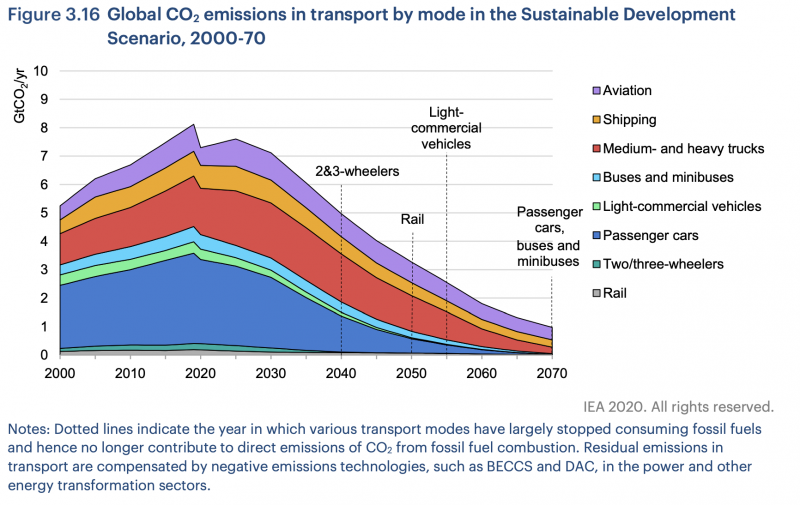
However, the UK’s privacy watchdog acts in the interests of the UK and so it may be in their best interest to say: nothing to see here, carry on please…
In a letter [PDF] this month to Julian Knight – chairman of Parliament’s Digital, Culture and Media and Sport Select Committee – the Information Commissioner’s Office detailed the findings of its investigation, having gone through 700TB and more than 300,000 documents seized from the now-defunct company.
Crucially, the watchdog said Cambridge Analytica pretty much dealt with information and tools that anyone could have purchased or used if they had the right budget and know-how: there were no special techniques nor hacking. Its raison d’etre – profiling voters to target them with influential ads – was achieved by tapping into Facebook’s highly problematic Graph API at the time, via a third-party quiz app people were encouraged to use, and downloading data from their profile pages and their friends’ pages.
Facebook subsequently dynamited its overly leaky API – the real scandal here – to end any further such slurpage, was fined half a million quid by the ICO, and ordered to cough up $5bn by America’s consumer protection regulator, the FTC. If Cambridge Analytica achieved anything at all, it was blowing the lid off Facebook’s slipshod and cavalier approach to safeguarding netizens’ privacy.
Information Commissioner Elizabeth Denham’s team characterized Cambridge Analytica, and its related outfit SCL Elections, as a bit of a smoke-and-mirrors operation that lacked the sort of game-changing insight it sold to clients, who were told they could use the database of Facebook addicts to micro-target particular key voters with specific advertising to swing their political opinion in one direction or another.
“In summary, we concluded that SCL/CA were purchasing significant volumes of commercially available personal data (at one estimate over 130 billion data points), in the main about millions of US voters, to combine it with the Facebook derived insight information they had obtained from an academic at Cambridge University, Dr Aleksandr Kogan, and elsewhere,” the ICO wrote. Kogan and his company Global Science Research (GSR) was tasked with harvesting 87 million Facebook users’ personal data from the aforementioned quiz app.
“In the main their models were also built from ‘off the shelf’ analytical tools and there was evidence that their own staff were concerned about some of the public statements the leadership of the company were making about their impact and influence.”
El Reg has heard on good authority from sources in British political circles that Cambridge Analytica’s advertised powers of online suggestion were rather overblown and in fact mostly useless. In the end, it was skewered by its own hype, accused of tangibly influencing the Brexit and presidential votes on behalf of political parties and campaigners using Facebook data. Yet, no evidence could be found supporting those claims.
On Brexit, the ICO reckoned Cambridge Analytica just had information on Americans from the social network:
For what it’s worth, the ICO observed that a Canadian outfit called AggregateIQ, which was closely linked to Cambridge Analytica, was recruited by pro-Brexit campaigners to target adverts at British Facebook users.
And on the US elections, we’re told a database of voters was assembled from Facebook records, and that “targeted advertising was ultimately likely the final purpose of the data gathering but whether or which specific data from GSR was then used in any specific part of campaign has not been possible to determine from the digital evidence reviewed.”
And as for Russia: “We did not find any additional evidence of Russian involvement in our analysis of material contained in the SCL / CA servers we obtained,” the ICO stated, adding that this is kinda outside its remit and something for the UK’s National Crime Agency to probe.
Were Cambridge Analytica still around, we imagine some details of the report would be a little embarrassing. Alas, it shut down all operations (sort of) back in 2018.
Their models were also built from ‘off the shelf’ analytical tools and there was evidence that their own staff were concerned about some of the public statements the leadership of the company were making about their impact and influence
The ICO report noted how Cambridge Analytica was probably also less than honest with the sales pitches it made to both the Trump and Leave EU campaigns, overstating the amount of data it had collected.
“SCL’s own marketing material claimed they had ‘Over 5,000 data points per individual on 230 million adult Americans’,” the ICO noted. “However, based on what we found it appears that this may have been an exaggeration.”
The company was also taken to task for poor data practices that, even had the political marketing stuff not blown up in public, likely would have landed it in hot water with the ICO.
While Cambridge Analytica may be gone and the ICO investigation concluded, Denham also warned that the tools and techniques it claimed could tip elections are not going away, and are likely to be used in the very near future… and may even work this time.
“What is clear is that the use of digital campaign techniques are a permanent fixture of our elections and the wider democratic process and will only continue to grow in the future,” the commissioner wrote. “The COVID-19 pandemic is only likely to accelerate this process as political parties and campaigns seek to engage with voters in a safe and socially distanced way.”

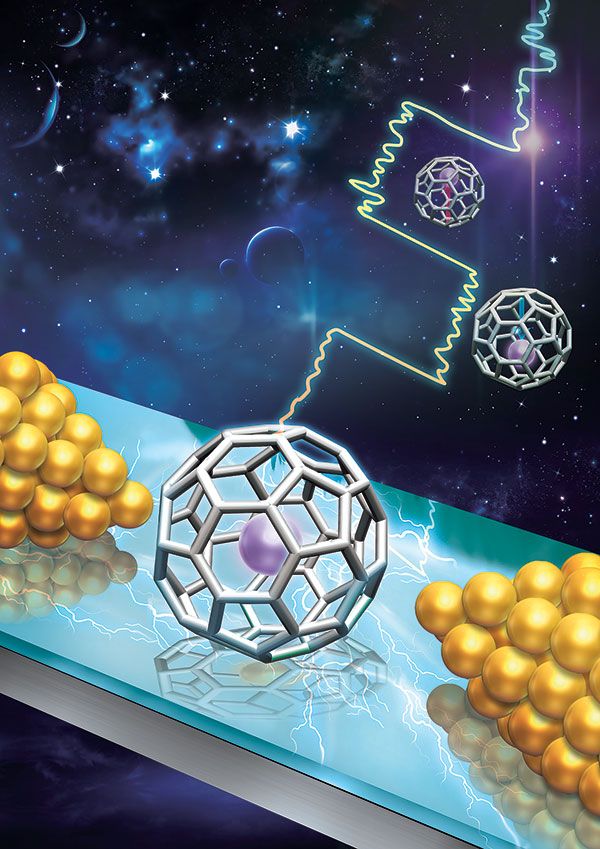 Along with colleagues at Nanjing University, Renmin University, Xiamen University, and Rensselaer Polytechnic Institute, Mark Reed, the Harold Hodgkinson Professor of Electrical Engineering & Applied Physics demonstrated a single-molecule electret with a functional memory. The results were published Oct. 12 in Nature Nanotechnology.
Along with colleagues at Nanjing University, Renmin University, Xiamen University, and Rensselaer Polytechnic Institute, Mark Reed, the Harold Hodgkinson Professor of Electrical Engineering & Applied Physics demonstrated a single-molecule electret with a functional memory. The results were published Oct. 12 in Nature Nanotechnology.