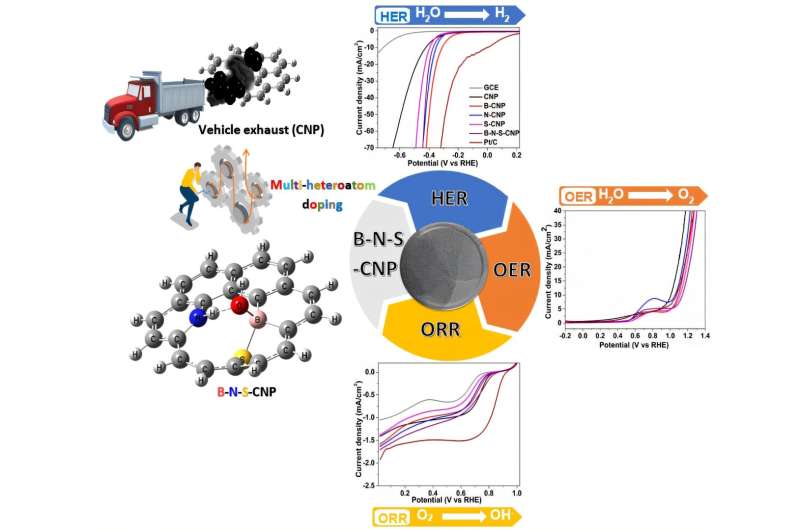
Research from a leading academic shows Android users have advertising cookies and other gizmos working to build profiles on them even before they open their first app.
Doug Leith, professor and chair of computer systems at Trinity College Dublin, who carried out the research, claims in his write up that no consent is sought for the various identifiers and there is no way of opting out from having them run.
He found various mechanisms operating on the Android system which were then relaying the data back to Google via pre-installed apps such as Google Play Services and the Google Play store, all without users ever opening a Google app.
One of these is the “DSID” cookie, which Google explains in its documentation is used to identify a “signed in user on non-Google websites so that the user’s preference for personalized advertising is respected accordingly.” The “DSID” cookie lasts for two weeks.
Speaking about Google’s description in its documentation, Leith’s research states the explanation was still “rather vague and not as helpful as it might be,” and the main issue is that there’s no consent sought from Google before dropping the cookie and there’s no opt-out feature either.
Leith says the DSID advertising cookie is created shortly after the user logs into their Google account – part of the Android startup process – with a tracking file linked to that account placed into the Google Play Service’s app data folder.
This DSID cookie is “almost certainly” the primary method Google uses to link analytics and advertising events, such as ad clicks, to individual users, Leith writes in his paper [PDF].
Another tracker which cannot be removed once created is the Google Android ID, a device identifier that’s linked to a user’s Google account and created after the first connection made to the device by Google Play Services.
It continues to send data about the device back to Google even after the user logs out of their Google account and the only way to remove it, and its data, is to factory-reset the device.
Leith said he wasn’t able to ascertain the purpose of the identifier but his paper notes a code comment, presumably made by a Google dev, acknowledging that this identifier is considered personally identifiable information (PII), likely bringing it into the scope of European privacy law GDPR – still mostly intact in British law as UK GDPR.
The paper details the various other trackers and identifiers dropped by Google onto Android devices, all without user consent and according to Leith, in many cases it presents possible violations of data protection law.
Leith approached Google for a response before publishing his findings, which he delayed allowing time for a dialogue.
[…]
The findings come amid something of a recent uproar about another process called Android System SafetyCore – which arrived in a recent update for devices running Android 9 and later. It scans a user’s photo library for explicit images and displays content warnings before viewing them. Google says “the classification of content runs exclusively on your device and the results aren’t shared with Google.”
Naturally, it will also bring similar tech to Google Messages down the line to prevent certain unsolicited images from affecting a receiver.
Google started installing SafetyCore on user devices in November 2024, and there’s no way of opting out or managing the installation. One day, it’s just there.
Users have vented their frustrations about SafetyCore ever since and despite being able to uninstall and opt out of image scanning, the consent-less approach that runs throughout Android nevertheless left some users upset. It can be uninstalled on Android forks like Xiaomi’s MIUI using Settings>Apps>Android System SafetyCore>Uninstall or on Android using Apps/Apps & Notifications>Show System Apps>Show system apps>Locate SafetyCore>Uninstall or Disable. Reviewers report that in some cases the uninstall option is grayed out, and it can only be disabled, while others complain that it reinstalls on the next update.
The app’s Google Play page is littered with negative reviews, many of which cite its installation without consent.
“In short, it is spyware. We were not informed. It feels like the right to privacy is secondary to Google’s corporate interests,” one reviewer wrote.