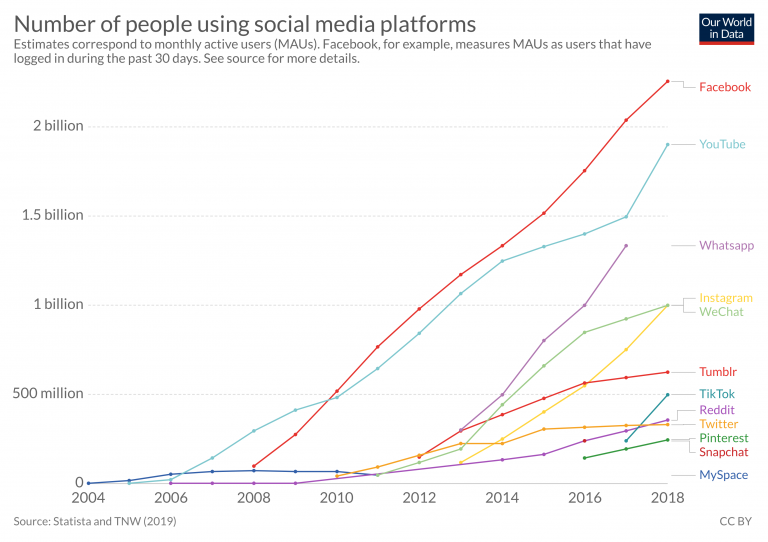
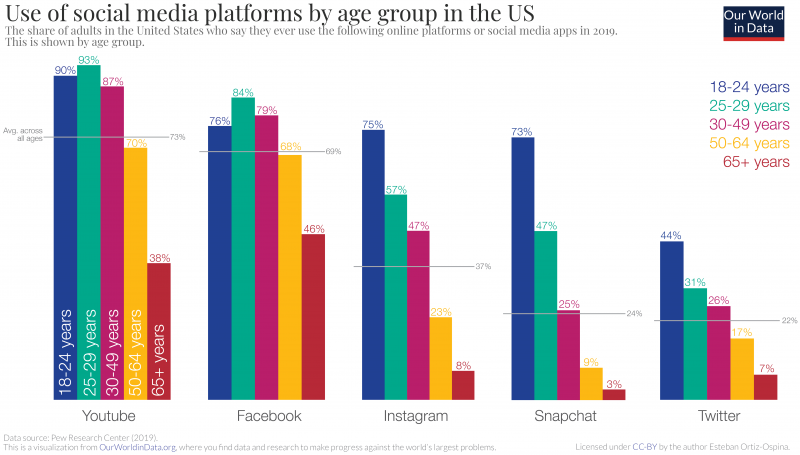
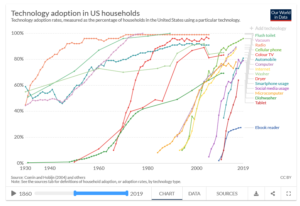
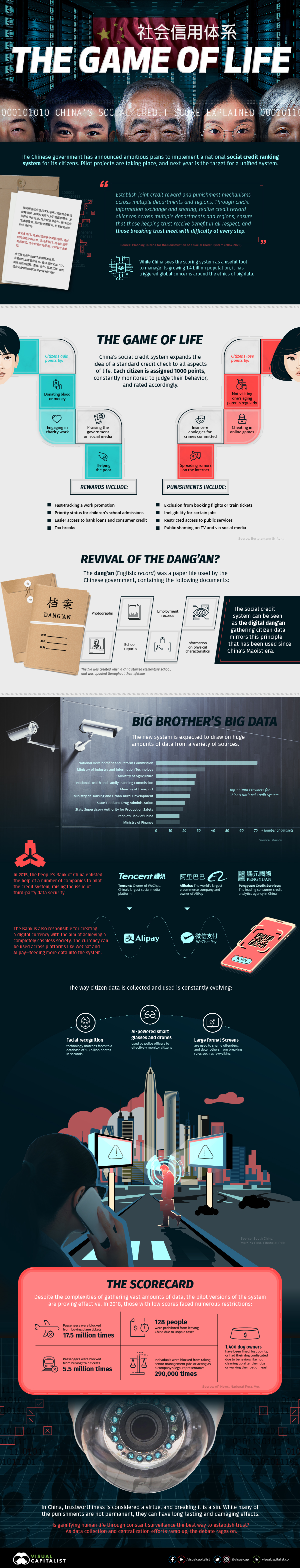
Yesterday afternoon, the Pentagon notified Congress of its purchase of a microwave weapon system designed to knock down swarms of enemy drones with pulses of energy. The purchase comes with an intent to deploy the PHASER system overseas for a year-long assessment, making it the first directed energy defense weapon to ever be fielded.
[…]
The U.S. Air Force spent $16.28 million for one prototype PHASER high power microwave system for a “field assessment for purposes of experimentation” in an unspecified location outside the U.S. The test is “expected to be completed by Dec. 20, 2020,” making the overseas deployment “against real-world or simulated hostile vignettes” imminent.
A Growing Threat
There are several directed energy weapons that the Air Force is buying to test their effectiveness in the field, and officials say some will be on the frontlines in tense areas of the globe where enemy drones are becoming a threat, includes North Korea, Africa, the Ukraine and—most recently—the Middle East.
“At the moment we have awarded multiple DE systems for use in our field assessment overseas and are working to support multiple bases and areas of responsibility,” says Michael Jirjis, who is lead on the PHASER experiment, told Popular Mechanics. “We can’t say which specific locations at this time.”
[…]
The recent swarm attack on Saudi Arabian oil facilities has highlighted the risk and drawn a stern response from the Pentagon.
“This is not the reaction of just a few events but the realization of a growing need over the past few years,” says Jirjis.
Gen. Joseph Dunford, the chairman of the Joint Chiefs of Staff, said on Friday that the U.S. would be moving enhanced air defenses into the region. He didn’t offer any specifics, saying the Pentagon is working with the Saudis to come up with a support plan. The PHASER system, by virtue of timing, could now land at the forefront of an international crisis.
“It is a remarkable coincidence because this has been in the works between the Air Force and Raytheon essentially since an experiment at White Sands [Missile Range] late last year,” says Don Sullivan, Raytheon missile systems’ chief technologist for directed energy.
Those who sell drone-killing weapons keep a sharp eye on the warning signs, and there were many that preceded the attack in Saudi Arabia.
“There are fairly recent incidents, for example in Yemen where a very large drone with a high explosive payload killed about 40 people, at a prayer ground of all places. And that was on YouTube,” Sullivan says. “It was a real eye-opener. What happened in Saudi over the weekend was kind of that raised to the nth degree.”
[…]
The system uses microwaves to disable Class One and Class Two drones, ones that are less than 55 pounds and fly at altitudes of 1,200 to 3,500 feet at speeds between 100 and 200 knots. Think RQ-11 Raven at the low end and a ScanEagle as the maximum-sized target.
There were an estimated 20 drones and cruise missiles used to attack Saudi Arabia, and some of the drones may have been small enough for PHASER to have disabled them. The HPM system is not known to work against cruise missiles, according the Air Force and Raytheon.
[…]
PHASER is high-powered microwaves cannon that emits radio frequencies in a conical beam. It doesn’t cook a drone with heat. Instead, the weapon disrupts or destroys their circuits with a burst of overwhelming energy.
“It’s not a thermal effect, it’s an electric field effect that is basically imposed on the electronics to either upset or permanently damage them,” says Sullivan. “And the effect is essentially instantaneous.”
[…]
Microwave weapons have traditionally been hampered by the fact that they don’t discriminate targets—bathing an area with them could damage friendly hardware along with a foe’s. But with attacks involving swarms of small UAVs becoming popular, that vice has become a virtue since PHASER can attack multiple targets simultaneously and doesn’t run out of ammunition.
Source: PHASER Microwave Weapon – The Air Force Is Deploying PHASER