If developers do start leveraging the Windows Store, the Windows 10 S experiment could take off, as users won’t find a need to install legacy programs. This will largely depend on web browsers being available there, as many users dislike Edge. Thankfully, Microsoft is allowing third-party browser installs from the Windows Store. Unfortunately, there is a big catch — you cannot change the default. Buried in the Windows 10 S FAQ, the following question is presented — “Are there any defaults that I cannot change on my Windows 10 S PC?” Microsoft provides the answer: “Yes, Microsoft Edge is the default web browser on Microsoft 10 S. You are able to download another browser that might be available from the Windows Store, but Microsoft Edge will remain the default if, for example, you open an .htm file. Additionally, the default search provider in Microsoft Edge and Internet Explorer cannot be changed.”
NSA collected Americans’ phone records (151 million of them!) despite law change
The U.S. National Security Agency collected more than 151 million records of Americans’ phone calls last year, even after Congress limited its ability to collect bulk phone records, according to an annual report issued on Tuesday by the top U.S. intelligence officer.
The report from the office of Director of National Intelligence Dan Coats was the first measure of the effects of the 2015 USA Freedom Act, which limited the NSA to collecting phone records and contacts of people U.S. and allied intelligence agencies suspect may have ties to terrorism.
It found that the NSA collected the 151 million records even though it had warrants from the secret Foreign Intelligence Surveillance court to spy on only 42 terrorism suspects in 2016, in addition to a handful identified the previous year.
The NSA has been gathering a vast quantity of telephone “metadata,” records of callers’ and recipients’ phone numbers and the times and durations of the calls – but not their content – since the September 11, 2001, attacks.
Source: NSA collected Americans’ phone records despite law change: report
After years of warnings, mobile network hackers exploit SS7 flaws to drain bank accounts via MitM attacks
Experts have been warning for years about security blunders in the Signaling System 7 protocol – the magic glue used by cellphone networks to communicate with each other.
These shortcomings can be potentially abused to, for example, redirect people’s calls and text messages to miscreants’ devices. Now we’ve seen the first case of crooks exploiting the design flaws to line their pockets with victims’ cash.
O2-Telefonica in Germany has confirmed to Süddeutsche Zeitung that some of its customers have had their bank accounts drained using a two-stage attack that exploits SS7.
In other words, thieves exploited SS7 to intercept two-factor authentication codes sent to online banking customers, allowing them to empty their accounts. The thefts occurred over the past few months, according to multiple sources.
Source: After years of warnings, mobile network hackers exploit SS7 flaws to drain bank accounts
Endurance in a pill
“It’s well known that people can improve their aerobic endurance through training,” says senior author Ronald Evans, Howard Hughes Medical Institute investigator and holder of Salk’s March of Dimes Chair in Molecular and Developmental Biology. “The question for us was: how does endurance work? And if we really understand the science, can we replace training with a drug?”
Developing endurance means being able to sustain an aerobic activity for longer periods of time. As people become more fit, their muscles shift from burning carbohydrates (glucose) to burning fat. So researchers assumed that endurance is a function of the body’s increasing ability to burn fat, though details of the process have been murky. Previous work by the Evans lab into a gene called PPAR delta (PPARD) offered intriguing clues: mice genetically engineered to have permanently activated PPARD became long-distance runners who were resistant to weight gain and highly responsive to insulin — all qualities associated with physical fitness. The team found that a chemical compound called GW1516 (GW) similarly activated PPARD, replicating the weight control and insulin responsiveness in normal mice that had been seen in the engineered ones. However, GW did not affect endurance (how long the mice could run) unless coupled with daily exercise, which defeated the purpose of using it to replace exercise.
In the current study, the Salk team gave normal mice a higher dose of GW, for a longer period of time (8 weeks instead of 4). Both the mice that received the compound and mice that did not were typically sedentary, but all were subjected to treadmill tests to see how long they could run until exhausted.
Mice in the control group could run about 160 minutes before exhaustion. Mice on the drug, however, could run about 270 minutes — about 70 percent longer. For both groups, exhaustion set in when blood sugar (glucose) dropped to around 70 mg/dl, suggesting that low glucose levels (hypoglycemia) are responsible for fatigue.
rpcbomb: remote rpcbind denial-of-service + patches
This vulnerability allows an attacker to allocate any amount of bytes (up to 4 gigabytes per attack) on a remote rpcbind host, and the memory is never freed unless the process crashes or the administrator halts or restarts the rpcbind service.
Attacking a system is trivial; a single attack consists of sending a specially crafted payload of around 60 bytes through a UDP socket.
This can slow down the system’s operations significantly or prevent other services (such as a web server) from spawning processes entirely.
Source: rpcbomb: remote rpcbind denial-of-service + patches
Mozilla Fathom – framework for classifying the web semantically
Fathom is a JavaScript framework for extracting meaning from web pages, identifying parts like Previous/Next buttons, address forms, and the main textual content—or classifying a page as a whole. Essentially, it scores DOM nodes and extracts them based on conditions you specify. A Prolog-inspired system of types and annotations expresses dependencies between scoring steps and keeps state under control. It also provides the freedom to extend existing sets of scoring rules without editing them directly, so multiple third-party refinements can be mixed together.
I like the semantic web idea, but it never really picked up. Maybe this will work.
FuturePets.com database of thousands of credit cards was left exposed for months
A US online pet store has exposed the details of more than 110,400 credit cards used to make purchases through its website, researchers have found.
In a stunning show of poor security, the Austin, Texas-based company FuturePets.com exposed its entire customer database, including names, postal and email addresses, phone numbers, credit card information, and plain-text passwords
[…]
The database was exposed because of the company’s own insecure server and use of “rsync,” a common protocol used for synchronizing copies of files between two different computers, which wasn’t protected with a password.
Source: A database of thousands of credit cards was left exposed for months
Oh dear, clear text passwords and non-protected rsync transfers 🙁
Yes, your whatsapp messages can be read by the London police
Bruce66423 brings word that a terrorist’s WhatsApp message has been decrypted “using techniques that ‘cannot be disclosed for security reasons’, though ‘sources said they now have the technical expertise to repeat the process in future.'” The Economic Times reports:
U.K. security services have managed to decode the last message sent out by Khalid Masood before he rammed his high-speed car into pedestrians on Westminster Bridge and stabbed to death a police officer at the gates of Parliament on March 22. The access to Masood’s message was achieved by what has been described by security sources as a use of “human and technical intelligence”…
Russian-controlled telecom hijacks financial services’ Internet traffic
On Wednesday, large chunks of network traffic belonging to MasterCard, Visa, and more than two dozen other financial services companies were briefly routed through a Russian government-controlled telecom under unexplained circumstances that renew lingering questions about the trust and reliability of some of the most sensitive Internet communications.
Anomalies in the border gateway protocol—which routes large-scale amounts of traffic among Internet backbones, ISPs, and other large networks—are common and usually the result of human error. While it’s possible Wednesday’s five- to seven-minute hijack of 36 large network blocks may also have been inadvertent, the high concentration of technology and financial services companies affected made the incident “curious” to engineers at network monitoring service BGPmon. What’s more, the way some of the affected networks were redirected indicated their underlying prefixes had been manually inserted into BGP tables, most likely by someone at Rostelecom, the Russian government-controlled telecom that improperly announced ownership of the blocks.
“Quite suspicious”“I would classify this as quite suspicious,” Doug Madory, director of Internet analysis at network management firm Dyn, told Ars. “Typically accidental leaks appear more voluminous and indiscriminate. This would appear to be targeted to financial institutions. A typical cause of these errors [is] in some sort of internal traffic engineering, but it would seem strange that someone would limit their traffic engineering to mostly financial networks.”
Source: Russian-controlled telecom hijacks financial services’ Internet traffic
Jenkins admin? Get buzzy patching, says Cloudbees
The bug, CVE-2017-1000353, exists in how Jenkins implements HTTP upload/download requests.
The bug lets an attacker exploit a serialised object in the preamble of commands sent to the CLI. As described by Securiteam, “since Jenkins does not validate the serialised object, any serialise[d] object can be sent.”
The attacker can use the channel to send SignedObject to the CLI. Jenkins deserialises it using a new ObjectInputStream, which the company says bypasses its blacklist-based protection mechanism.
To block it, Cloudbees has added SignedObject to its blacklist.
To test the vulnerability for yourself, the bug report suggests the following:
Create a serialised object whose payload is a command executed by running the payload.jar script;
Change the Python script jenkins_poc1.py to adjust the target target URL, and open your payload file.
Source: Jenkins admin? Get buzzy patching, says Cloudbees
Remote security exploit in all 2008+ Intel platforms – SemiAccurate
The short version is that every Intel platform with AMT, ISM, and SBT from Nehalem in 2008 to Kaby Lake in 2017 has a remotely exploitable security hole in the ME (Management Engine) not CPU firmware. If this isn’t scary enough news, even if your machine doesn’t have SMT, ISM, or SBT provisioned, it is still vulnerable, just not over the network. For the moment. From what SemiAccurate gathers, there is literally no Intel box made in the last 9+ years that isn’t at risk. This is somewhere between nightmarish and apocalyptic.
First a little bit of background. SemiAccurate has known about this vulnerability for literally years now, it came up in research we were doing on hardware backdoors over five years ago. What we found was scary on a level that literally kept us up at night. For obvious reasons we couldn’t publish what we found out but we took every opportunity to beg anyone who could even tangentially influence the right people to do something about this security problem. SemiAccurate explained the problem to literally dozens of “right people” to seemingly no avail. We also strongly hinted that it existed at every chance we had.
Various Intel representatives over the years took my words seriously, told me I was crazy, denied that the problem could exist, and even gave SemiAccurate rather farcical technical reasons why their position wasn’t wrong. Or dangerous. In return we smiled politely, argued technically, and sometimes, usually actually, were not so polite about our viewpoint. Unfortunately it all seems to have been for naught.
The problem is quite simple, the ME controls the network ports and has DMA access to the system. It can arbitrarily read and write to any memory or storage on the system, can bypass disk encryption once it is unlocked (and possibly if it has not, SemiAccurate hasn’t been able to 100% verify this capability yet), read and write to the screen, and do all of this completely unlogged. Due to the network access abilities, it can also send whatever it finds out to wherever it wants, encrypted or not.
Source: Remote security exploit in all 2008+ Intel platforms – SemiAccurate
Oh shit.
You can download a detector here from Intel
This Artificially Intelligent Speech Generator Can Fake Anyone’s Voice
“We train our models on a huge dataset with thousands of speakers,” Jose Sotelo, a team member at Lyrebird and a speech synthesis expert, told Gizmodo. “Then, for a new speaker we compress their information in a small key that contains their voice DNA. We use this key to say new sentences.”
The end result is far from perfect—the samples still exhibit digital artifacts, clarity problems, and other weirdness—but there’s little doubt who is being imitated by the speech generator. Changes in intonation are also discernible. Unlike other systems, Lyrebird’s solution requires less data per speaker to produce a new voice, and it works in real time. The company plans to offer its tool to companies in need of speech synthesis solutions.
[…]
“We take seriously the potential malicious applications of our technology,” Sotelo told Gizmodo. “We want this technology to be used for good purposes: giving back the voice to people who lost it to sickness, being able to record yourself at different stages in your life and hearing your voice later on, etc. Since this technology could be developed by other groups with malicious purposes, we believe that the right thing to do is to make it public and well-known so we stop relying on audio recordings [as evidence].”
Source: This Artificially Intelligent Speech Generator Can Fake Anyone’s Voice
How to Easily Unsubscribe from Bulk Emails in Gmail – Unroll.me Alternative
How to easily unsubscribe your Gmail email address from mailing lists, newsletters, junk and other unsolicited bulk mail that is clogging up your Gmail inbox.
Source: How to Easily Unsubscribe from Bulk Emails in Gmail – Unroll.me Alternative
Netgear says sorry four weeks after losing customer backups on cloud and locally(!!!!) – yes the cloud can hurt you!
Neatgear has cocked up its cloud management service, losing data stored locally on ReadyNAS devices’ shared folders worldwide – and customers have complained to The Register about only being informed four weeks later.
This week, the San Jose-based networking business sent an email to customers, seen by The Register, confirming that an “outage” affecting ReadyCLOUD, the free service for its network attached storage offering, caused the storage systems to disconnect from the cloud service and be marked as deleted at the end of March.
Compounding the issue, as part of a clean-up process, Netgear decided that when a ReadyCloud account is marked as closed, the NAS holding that account’s home folder should be deleted along with all of the data it was holding.
As one user complained to The Register: “In practice, accounts are generally deleted from the NAS admin screen by the user and a big warning flashes up to tell you that all data will be deleted. In this case, as the glitch was server side, no warning was presented and loads of people found that their home folders and data had mysteriously been deleted, by the looks of it, at the command of Netgear.”
Source: Netgear says sorry four weeks after losing customer backups
Windows is Bloated, Thanks to Adobe’s Extensible Metadata Platform – Thurrott.com
I put together a tool that scans files for PNG images containing Adobe metadata and was surprised that Windows is host to a lot of this gunk.
[…]
Windows Explorer, for example, is a critical Shell component in the startup hot path. But despite its importance, it’s comprised of ~20% pure garbage. ApplicationFrame.dll, responsible for Windows app title bars and frame gizmos, is ~41% garbage. Twinui, imageres, and other related components scored with much lower numbers but couldn’t fully escape Adobe XMP.
Source: Windows is Bloated, Thanks to Adobe’s Extensible Metadata Platform – Thurrott.com
Ouch!
Popular belief that saturated fat clogs up arteries is a myth, experts say – let the wars begin: others disagree!
Heart experts have been criticised for claiming it is “plain wrong” to believe that saturated fat clogs up arteries.
Three specialists argued that eating “real food”, taking exercise and reducing stress are better ways to stave off heart disease than cutting out dietary saturated fat.
Writing in a respected journal, they maintained that inflammation is the chief threat to arteries and there is little evidence linking saturated fat consumption with heart disease, diabetes and premature death.
But the editorial, published in the British Journal of Sports Medicine, attracted scathing criticism for being “simplistic”, “muddled” and “misleading”.
The authors, led by Dr Aseem Malhotra, from Lister Hospital, Stevenage, wrote: “Despite popular belief among doctors and the public, the conceptual model of dietary saturated fat clogging a pipe is just plain wrong.”
Dr Malhotra and colleagues Professor Rita Redberg, from the University of California at San Francisco, and Pascal Meier from University Hospital Geneva in Switzerland and University College London, cited a “landmark” review of evidence that appeared to exonerate saturated fat.
Source: Popular belief that saturated fat clogs up arteries is a myth, experts say
iPhone lawyers literally compare Apples with Pears in trademark war – and win!
Pear Technology, which produces digital mapping software and services, applied for the pear logo in 2014 and was almost immediately challenged by Apple, which claimed it was confusingly similar to its own apple-with-a-bite-out-of-it silhouette logo.
The Cupertino intellectual property lawyers claimed that despite one being a picture of a pear and one being a picture of an apple they were, legally, the same. How? Here are the words that make this leap of logic possible: “abstract stylization” and “sleek, rounded silhouettes of the fruits.”
As opposed to the jagged, spiky pears that you see in the supermarket all the time.
Even though the Pear Technologies trademark application had the word “Pear Technologies” written underneath as part of the mark, this mere detail was not enough to prevent consumers from being confused as to the difference between a pear and an apple, it seems.
Source: iPhone lawyers literally compare Apples with Pears in trademark war
Absolutely incredible that Apple(tm) have managed to trademark any and all fruits! How ridiculous is this world getting?
FYI: You can blow Intel-powered broadband modems off the ‘net with a ‘trivial’ packet stream
This week, inquisitive netizens discovered that, when presented with even modest amounts of network packets – as little as 1.5Mbps spread across various TCP or UDP ports – modems equipped with a Puma 6 slow to an unusable crawl.
According to one engineer who spoke to El Reg on the issue, the flaw would be “trivial” to exploit in the wild, and would effectively render a targeted box useless for the duration of the attack.
“You send a stream of 200Kbps of TCP, UDP or maybe even ICMP to different port numbers, and it has a tiny table to keep track of these that fills up. The device becomes immediately unresponsive. It comes back after you stop,” our tipster explained.
“It can be exploited remotely, and there is no way to mitigate the issue.”
Source: FYI: You can blow Intel-powered broadband modems off the ‘net with a ‘trivial’ packet stream
UK gov forces porn sites to gather personal info and allows gov depts to share citizens data despite being hugely unsafe
ISPs may be forced to block sites which fail to do so, and the fact that many such sites are not based in the UK nor subject to British law shall pose plenty of difficulties for the law’s implementation, as will its provisions forcing ISPs to prohibit access to “non-conventional sex acts”, which has provoked plenty of criticism from the less vanilla members of society.
The legislation, which requires websites serving up adult content to verify users’ ages or be blocked by ISPs, was criticised as an “unworkable proposal” by Open Rights Group, among others, including feminist pornographer Pandora Blake:
On the passing of the bill, Open Rights Group’s executive director Jim Killock said: “Age verification is an accident waiting to happen. Despite repeated warnings, parliament has failed to listen to concerns about the privacy and security of people who want to watch legal adult content.
“As we saw with the Ashley Madison leaks, the hacking of private information about people’s sex lives, has huge repercussions for those involved. The UK government has failed to take responsibility for its proposals and placed the responsibility for people’s privacy into the hands of porn companies.”
[…]
Last year, the National Audit Office warned of government’s data-handling capabilities, noting that there were 9,000 data breaches over the reporting period and warning that “cuts to departmental budgets and staff numbers, and increasing demands form citizens for online public services, have changed the way government collects, stores and manages information.”Samson said that large parts of the Digital Economy Bill regarding data sharing remained unclear, and noted that it received Royal Assent with a lot of information left to follow.
“We’ve been told throughout the process that everything will adhere to the Data Protection Act, but that will be redundant from May of next year when the EU’s General Data Protection Regulation comes in,” said Samson. “Whatever is drafted to comply with the DPA will have to change for the GDPR, which means ensuring the individual’s consent and knowledge regarding how their data is being used.”
Source: Just delete the internet – pr0n-blocking legislation receives Royal Assent
How Did Unroll.me Get Users to Allow It to Sell Their Inbox Data?
But a New York Times profile of Uber this weekend revealed, in passing, that Unroll.me, which is owned by a company called Slice Intelligence, isn’t just in the business of tidying up customers’ inboxes. Slice makes money by scanning its users’ email for receipts, then packaging that information into intel reports on consumer habits. Uber, for example, was paying Slice to find users’ Lyft receipts, so it could see how much they were spending each month, “as a proxy for the health of Lyft’s business.”
On its website, Slice brags that it has access to 4.2 million people’s inboxes, where it quietly sits looking at receipts from “hundreds of thousands of retailers.” Many Unroll.me users have been quite upset to learn about the extent of the data collection, which the service’s CEO, Jojo Hedaya, wrote in a blog post yesterday is “heartbreaking.”
“[W]hile we try our best to be open about our business model, recent customer feedback tells me we weren’t explicit enough,” Hedaya wrote.
Source: How Did Unroll.me Get Users to Allow It to Sell Their Inbox Data?
Hint – they used some nice tricks including the “for any purpose” line…
Nuh-uh, Google, you WILL hand over emails stored on foreign servers, says US judge
Google has been ordered by a US court to cough up people’s private Gmail messages stored overseas – because if that information can be viewed stateside, it is subject to American search warrants, apparently.
During a hearing on Wednesday in California, magistrate judge Laurel Beeler rejected [PDF] the advertising giant’s objections to a US government search warrant seeking data stored on its foreign servers. The Mountain View goliath had filed a motion to quash the warrant, and was denied.
The warrant, issued on June 30, 2016, ordered Google to hand over information on a number of specific Gmail accounts, including message content, attachments, metadata, and locational data.
While Google complied with the warrants and handed all of the requested records for several accounts over to Uncle Sam’s agents, it refused to cough up information on two accounts and declined to access attachments on two others, arguing that because the data was held outside the US it was not covered by the warrant, as was decided in the Microsoft email brouhaha.
Judge Beeler, however, disagreed with the Chocolate Factory’s assessment, reasoning that if Google was able to pull up the data on its own machines in the US, then it should fall under a US court’s jurisdiction and, because it would be pulled from Google’s HQ in Mountain View, it was not considered overseas content the way Microsoft’s Ireland-based info was.
Source: Nuh-uh, Google, you WILL hand over emails stored on foreign servers, says US judge
Because in the US, are your base are belong to US
NL Court rules fan subtitles on TV and movies are illegal
Subtitle lovers, beware: a court just ruled that making fan subtitles or translations is not protected by the law. A Dutch group called (translated) the Free Subtitles Foundation took anti-piracy group BREIN to court over “fansubbing.” BREIN has previously been active in taking fan subtitles and translations offline, and the Foundation was hoping a Dutch court would come down on the side of fair use.
The court didn’t quite see it that way. It ruled that making subtitles without permission from the property owners amounted to copyright infringement. BREIN wasn’t unsympathetic, but said it couldn’t allow fansubbers to continue doing what they’re doing (using the word “illegal” so many times I’ve almost forgotten what it means):
With this decision in hand it will be easier for BREIN to maintain its work against illegal subtitlers and against sites and services that collect illegal subtitles and add movies and TV shows from an illegal source.
While this only effects the Free Subtitles Foundation and BREIN at the moment, it could set legal precedent for subtitle-makers all over the world.
Source: Court rules fan subtitles on TV and movies are illegal
FFS so translated versions of texts that don’t exist yet fall under copyright?!
Script kiddies pwn 1000s of Windows boxes using leaked NSA hack tools
The NSA’s Equation Group hacking tools, leaked last Friday by the Shadow Brokers, have now been used to infect thousands of Windows machines worldwide, we’re told.
On Thursday, Dan Tentler, founder of security shop Phobos Group, told The Register he’s seen rising numbers of boxes on the public internet showing signs they have DOUBLEPULSAR installed on them. These hijacked machines can be used to sling malware, spam netizens, launch further attacks on other victims, and so on.
DOUBLEPULSAR is a backdoor used to inject and run malicious code on an infected system, and is installed using the ETERNALBLUE exploit that attacks SMB file-sharing services on Windows XP to Server 2008 R2. That means to compromise a computer, it must be running a vulnerable version of Windows and expose an SMB service to the attacker. Both DOUBLEPULSAR and ETERNALBLUE are leaked Equation Group tools, now available for any script kiddie or hardened crim to download and wield against vulnerable systems.
[…]
entler said that a preliminary scan of the public internet on Thursday using Shodan.io revealed 15,196 infections, with four-fifths of those coming from IP ranges in the US. These numbers increase with each followup scan. A DOUBLEPULSAR-riddled system can be identified by the way it responds to a special ping to port 445.
DOUBLEPULSAR“The polite term for what’s happening is a bloodbath. The impolite version is dumpster fire clown shoes shit show,” Tentler said. “I’m hopeful this is the wakeup moment for people over patching Windows machines.”
The problem may be even more serious. A larger scan by infosec researcher Robert Graham showed around 41,000 infected hosts and more scans are going to be carried out, so expect that number to rise.
Source: Script kiddies pwn 1000s of Windows boxes using leaked NSA hack tools
Researchers capture first ‘image’ of a dark matter web that connects galaxies
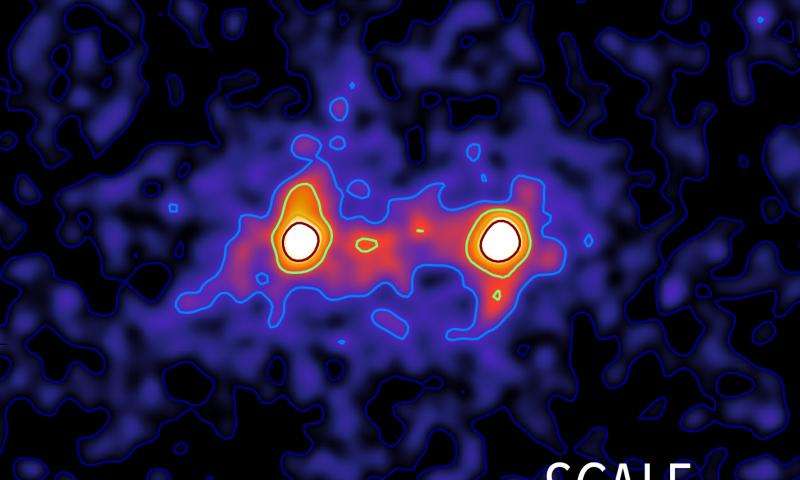
Researchers at the University of Waterloo have been able to capture the first composite image of a dark matter bridge that connects galaxies together. The scientists publish their work in a new paper in Monthly Notices of the Royal Astronomical Society.
The composite image, which combines a number of individual images, confirms predictions that galaxies across the universe are tied together through a cosmic web connected by dark matter that has until now remained unobservable.
[…]
They combined lensing images from more than 23,000 galaxy pairs located 4.5 billion light-years away to create a composite image or map that shows the presence of dark matter between the two galaxies. Results show the dark matter filament bridge is strongest between systems less than 40 million light years apart.
“By using this technique, we’re not only able to see that these dark matter filaments in the universe exist, we’re able to see the extent to which these filaments connect galaxies together,” said Epps.
Source: Researchers capture first ‘image’ of a dark matter web that connects galaxies
This new solar-powered device can pull water straight from the desert air
You can’t squeeze blood from a stone, but wringing water from the desert sky is now possible, thanks to a new spongelike device that uses sunlight to suck water vapor from air, even in low humidity. The device can produce nearly 3 liters of water per day for every kilogram of spongelike absorber it contains, and researchers say future versions will be even better. That means homes in the driest parts of the world could soon have a solar-powered appliance capable of delivering all the water they need, offering relief to billions of people.
[…]
“It has been a longstanding dream” to harvest water from desert air, says Mercouri Kanatzidis, a chemist at Northwestern University in Evanston, Illinois, who wasn’t involved with the work. “This demonstration … is a significant proof of concept.” It’s also one that Yaghi says has plenty of room for improvement. For starters, zirconium costs $150 a kilogram, making water-harvesting devices too expensive to be broadly useful. However, Yaghi says his group has already had early success in designing water-grabbing MOFs that replace zirconium with aluminum, a metal that is 100 times cheaper. That could make future water harvesters cheap enough not only to slake the thirst of people in arid regions, but perhaps even supply water to farmers in the desert
Source: This new solar-powered device can pull water straight from the desert air
