Amazon.com: FoodSaver V2244 Vacuum Sealing System with Starter Kit: Food Saver: Kitchen & Dining
Source: Amazon.com: FoodSaver V2244 Vacuum Sealing System with Starter Kit: Food Saver: Kitchen & Dining

You need one for sous vide cooking.

Amazon.com: FoodSaver V2244 Vacuum Sealing System with Starter Kit: Food Saver: Kitchen & Dining
Source: Amazon.com: FoodSaver V2244 Vacuum Sealing System with Starter Kit: Food Saver: Kitchen & Dining

You need one for sous vide cooking.
Windows may remove programs during an update for compatibility reasons. If a program is known to cause crashes, bugs, or otherwise conflict with Windows, Windows may remove it to keep your system stable. If this happens, the “All of your files are exactly where you left them” screen will appear like normal–this screen always appears during major updates–but Windows will actually have removed some of your program files.
It looks like this feature is designed to help protect the average Windows user, who might have outdated programs installed. Windows can clean them up and make sure they don’t cause problems. However, Windows doesn’t provide any notice that it’s removed a program–the program will just appear to vanish from your system.
When Windows 10’s first big update arrived, many people on Reddit noticed a variety of programs were being silently removed–most of which were hardware-related utilities. People have reported that it removed the popular Speccy, CPU-Z, HWMonitor, and CCleaner programs from many people’s systems. Many people claim it removed hardware drivers like Intel Rapid Storage Technology and AMD Catalyst Control Center, too. In some cases, people even reported that it removed PDF viewers and antivirus programs (perhaps outdated ones). Confusingly, it seems like the Windows update removed these programs from some computers but not others. Reports are not completely consistent.
Source: Windows 10 May Delete Your Programs Without Asking
You an get them back, apparently, but wow! Balls! I don’t want my OS deleting stuff from my PC!
But in the case of the biocomputer, the city is a chip measuring about 1.5 cm square in which channels have been etched. Instead of the electrons that are propelled by an electrical charge and move around within a traditional microchip, short strings of proteins (which the researchers call biological agents) travel around the circuit in a controlled way, their movements powered by ATP, the chemical that is, in some ways, the juice of life for everything from plants to politicians.Because it is run by biological agents, and as a result hardly heats up at all, the model bio-supercomputer that the researchers have developed uses far less energy than standard electronic supercomputers do, making it more sustainable. Traditional supercomputers use so much electricity that they heat up a lot and then need to be cooled down, often requiring their own power plant to function.
Source: Building living, breathing supercomputers | Newsroom – McGill University
The team, led by Mohammad Al Faruque, director of UCI’s Advanced Integrated Cyber-Physical Systems Lab, showed that a device as ordinary and ubiquitous as a smartphone can be placed next to a machine and capture acoustic signals that carry information about the precise movements of the printer’s nozzle. The recording can then be used to reverse engineer the object being printed and re-create it elsewhere. Detailed processes may be deciphered through this new kind of cyberattack, presenting significant security risks.
Source: Bad vibrations: UCI researchers find security breach in 3-D printing process
BorgBackup (short: Borg) is a deduplicating backup program. Optionally, it supports compression and authenticated encryption.The main goal of Borg is to provide an efficient and secure way to backup data. The data deduplication technique used makes Borg suitable for daily backups since only changes are stored. The authenticated encryption technique makes it suitable for backups to not fully trusted targets.
Source: Borg Documentation — Borg – Deduplicating Archiver 1.0.0 documentation
“These (mechanics) tool have the codes to read and write firmware and if it is compromised by a malicious car it can modify the firmware of other cars that come in afterwards,” Smith told Vulture South at the Nullcon security conference in Goa, India.
Smith’s mechanic malware compromises of learning, simulation, and attack modes. Learning mode monitors network communications between the mechanic’s computer and a car, and identifies potential modules. Those modules that diagnosis tools successfully contact are lit up in blue, and the findings are saved to an .ini configuration file along with captured packets.
Source: Mechanic computers used to pwn cars in new model-agnostic attack
Nearly two-and-a-half months ago, I started a daily examination of the Trans Pacific Partnership focused on the intellectual property and digital policy issues raised by the agreement. My initial plan for the Trouble with the TPP series was to write for one month leading up to the planned signing in New Zealand on February 4th. However, the more I dug into the TPP, the more trouble I found. With this final post in the series, I wrap up the key IP and digital policy concerns with links to all the original posts. Canadians interested in the TPP now have an opportunity to have their voices heard. The Standing Committee on International Trade has been conducting hearings on the agreement for several weeks and has announced plans for cross-country consultations. Canadians can provide written submissions by April 30th. Alternatively, they can ask the committee to appear as a witness. Details on the committee opportunities can be found here. In addition, Canadians can send their comments directly to Global Affairs Canada, which is managing the government’s consultation. The email address is TPP-PTP.Consultations@international.gc.ca. Why should Canadians speak out on the TPP? The former co-CEO of Research in Motion Jim Balsillie, Shopify CEO Tobi Lutke, Ford Canada CEO Dianne Craig, the Sierra Club, Doctors Without Borders, Canadian library groups, innovation expert Dan Breznitz, former deputy chief economist at Global Affairs Canada Dan Ciuriak, Canadian publisher Don LePan of Broadview Press, political science professor Blayne Haggart, investment dispute settlement expert professor Gus Van Harten, my colleague Professor Jeremy de Beer, and the Canadian Labour Congress are among those that have voiced concern with the agreement. My assessment of the IP and digital issues in the Trouble with the TPP series identified at least 49 reasons:
So just what has got mathematicians spooked? Apart from 2 and 5, all prime numbers end in 1, 3, 7 or 9 – they have to, else they would be divisible by 2 or 5 – and each of the four endings is equally likely. But while searching through the primes, the pair noticed that primes ending in 1 were less likely to be followed by another prime ending in 1. That shouldn’t happen if the primes were truly random – consecutive primes shouldn’t care about their neighbour’s digits.
“In ignorance, we thought things would be roughly equal,” says Andrew Granville of the University of Montreal, Canada. “One certainly believed that in a question like this we had a very strong understanding of what was going on.”
The pair found that in the first hundred million primes, a prime ending in 1 is followed by another ending in 1 just 18.5 per cent of the time. If the primes were distributed randomly, you’d expect to see two 1s next to each other 25 per cent of the time. Primes ending in 3 and 7 take up the slack, each following a 1 in 30 per cent of primes, while a 9 follows a 1 in around 22 per cent of occurrences.
Similar patterns showed up for the other combinations of endings, all deviating from the expected random values. The pair also found them in other bases, where numbers are counted in units other than 10s. That means the patterns aren’t a result of our base-10 numbering system, but something inherent to the primes themselves. The patterns become more in line with randomness as you count higher – the pair have checked up to a few trillion – but still persists.
Source: Mathematicians shocked to find pattern in ‘random’ prime numbers | New Scientist
The company made profits (before certain items) of €848 million, or $964 million, on revenues of €2.109 billion, or $2.326 billion. That compares to earnings before income tax, depreciation, and amortization of €515 million, or $592 million, in 2014, on revenues of €1.545 billion, or $1.777 billion.
The company also paid a dividend of €14 ($15.50) per share, resulting in a total dividend payout of €603 million, or $669 million. Supercell also initiated a share buyback scheme from its employees amounting to €114 million, or $128 million, in the past year.
That’s an incredible financial result for a company with just 180 employees. And 2016 is off to a good start, as Supercell’s Clash Royale has take the No. 1 spots in top downloads and top-grossing games in the U.S. Apple app store. The game is No. 1 in 44 countries right now. Supercell just announced that it has more than 100 million daily active users in almost every country.
Source: With just 3 games, Supercell made $924M in profits on $2.3B in revenue in 2015
The hackers breached Bangladesh Bank’s systems and stole its credentials for payment transfers, two senior officials at the bank said. They then bombarded the Federal Reserve Bank of New York with nearly three dozen requests to move money from the Bangladesh Bank’s account there to entities in the Philippines and Sri Lanka, the officials said.
Four requests to transfer a total of about $81 million to the Philippines went through, but a fifth, for $20 million, to a Sri Lankan non-profit organization was held up because the hackers misspelled the name of the NGO, Shalika Foundation.
Hackers misspelled “foundation” in the NGO’s name as “fandation”, prompting a routing bank, Deutsche Bank, to seek clarification from the Bangladesh central bank, which stopped the transaction, one of the officials said.
[…]
The transactions that were stopped totaled $850-$870 million, one of the officials said.
Source: How a hacker’s typo helped stop a billion dollar bank heist
Harvard researchers have designed a new type of foldable material that is versatile, tunable and self actuated. It can change size, volume and shape; it can fold flat to withstand the weight of an elephant without breaking, and pop right back up to prepare for the next task.
Source: A foldable material that can change size, volume and shape
Many users have confirmed in the comment section of a popular reddit post that “Windows 7 computers are being reported as automatically starting the Windows 10 upgrade without permission.” It’s no secret that Microsoft wants users to upgrade to their new OS. Earlier in the year, Windows 10 was set as a ‘recommended update’ so when you install new security or bug patches, the new OS is selected by default as well.
Source: Windows 10 Upgrade Reportedly Starting Automatically On Windows 7 PCs – Slashdot
Bloody hell, Microsoft, how do you think it’s OK to do this to people’s computers?!
Put your mobile devices on a table and turn them into the windows of a huge display.
Source: HuddleLamp – Spatially-Aware Mobile Displays for Ad-hoc Around-the-Table Collaboration
The CRAYFIS project is a novel approach to observing cosmic ray particles at the highest energies.It uses the world-wide array of existing smartphones instead of building an expensive dedicated detector.
Modern smartphones contain high-resolution cameras with digital sensors which are sensitive to the particles in a cosmic ray shower. They know where they are (GPS) and can upload their data (wi-fi). Most importantly, there are 1.5 billion active smartphones spread across the planet. Essentially, this detector has already been deployed; all that is missing is the app to collect the data
The CRAYFIS app operates in a manner similar to a screensaver. When the phone is connected to a power source and the screen goes to sleep, the app begins data-taking. No active participation is required on the part of the user after the initial download and installation.
Source: Crayfis: The app that turns your phone into a cosmic ray detector.
Wonder how much battery it eats?
The new FCC rules are meant to limit interference and target third-party firmware because it allows users to modify their radio frequency parameters. While the FCC requirements don’t actually block third-party firmware, it’s much easier for a router manufacturer to comply with the ruling by blocking out custom firmware like OpenWRT or Tomato altogether than it is to test that firmware for compliance.
http://lifehacker.com/tp-link-blocks-open-source-router-firmware-in-complianc-1764335555
This is one of the major learning points for OSS – compliance is incredibly important for widespread adoption, even if it is boring to implement, like documentation
LastPass is a popular password manager used by millions over years. E*Trade is… uhm… patent trolls, I guess? Some finance company with an * in the logo. LastPass uses the logo as a recognition point in the browser toolbar and input boxes, so you can easily choose which account to fill in. The LastPass * was red, E*Trade is purple and green. So LastPass now has 3 dots (…) as the logo. Much more hard to see and use. Goes to show how crazy trademark law is. Fuck you E*Trade shitheads, for making my daily life just a little bit more difficult.
Source: LastPass Forums • View topic – New Logo tomorrow – so what?
Windows 10’s new Spotlight feature usually shows you neat photographs and fun facts when you first start your computer. Now, it’s started showing ads. Here’s how to turn it off.
Source: Windows 10 Is Showing Ads On Your Lockscreen, Here’s How to Turn Them Off
So not only is Windows invading your privacy with windows 10, but is progressively flaunting your non-ownership of the platform.
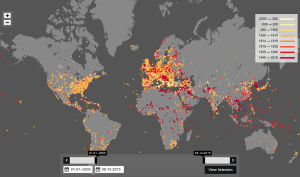
nodegoat is a web-based data management, analysis & visualisation environment.
Source: Battles | Public Interface | nodegoat
The minister states that he thinks (his vision is backed by a bunch of closed source software vendors [Microsoft, Oracle, SAP, KPN, CapGemini, Ordina, ATOS, CGI and IBM]) that not having to buy licenses is offset by the costs of having to manage and pay for the deployments of open source software (OSS). Which is free for closed source. Oh, no. It isn’t. He also states that customising the software costs money for development, whilst forgetting that at least OSS can be customised and closed source is vendor dependent – you try customising a Microsoft product!
Minister Blok (Wonen en Rijksdienst
It’s a simple bot that helps with court appeals — but could it replace the need for human lawyers?
Source: A 19-year-old made a free robot lawyer that has appealed $3 million in parking tickets
The issue lies in the wireless USB dongles that the keyboards and mice use to communicate over radio frequencies with the host computer. Bastille says that while communication from most keyboards to the dongle is encrypted, none of the mice it tested encrypt their wireless communication. The dongle, therefore, will accept commands from an attacker in close physical proximity the same way it would from the user.
The attacker can, therefore, transmit malicious packets that generate keystrokes rather than mouse clicks, so long as the victim’s computer is turned on, Bastille said.
“Depending on the speed of the attack and how closely the victim is paying attention, it can happen pretty quickly,” said researcher Marc Newlin, who said that an attack could simulate 1,000 words-per-minute typing and install a rootkit in 10 seconds, or eight milliseconds-per-keystroke.
Bastille founder Chris Rouland said that an attacker could exploit the vulnerability with a $15 USB dongle and 15 lines of Python code against any Windows, Mac or Linux machine and gain full control.
“At this point, they can inject malware, or compromise an air-gapped network by turning on Wi-Fi on the target,” Rouland said. “We have been working with the vendors for more than 90 days. More than half of the mice are not able to be updated and will not be patched. And likely won’t be replaced. There will be vulnerable devices everywhere.”
Do you work for a big company? Have you been having back pain? Your company probably knows about it already thanks to high-tech healthcare companies that it hired. Welcome to our brave new world of big data.
Source: Companies Are Using Big Data to Discourage Employees From Having Costly Surgery
They are using this to improve the health of their employess. Good. But also to track who is trying to get pregnant. Bad. Health information is very private for a reason. Having your employer look at it is very very bad and can lead to discrimination based on your medical history.
Here’s a clear, technical Q&A
Source: Confused as to WTF is happening with Apple, the FBI and a killer’s iPhone? Let’s fix that
It’s a good story by the reg.
The glibc DNS client side resolver is vulnerable to a stack-based buffer overflow when the getaddrinfo() library function is used. Software using this function may be exploited with attacker-controlled domain names, attacker-controlled DNS servers, or through a man-in-the-middle attack. Google has found some mitigations that may help prevent exploitation if you are not able to immediately patch your instance of glibc. The vulnerability relies on an oversized (2048+ bytes) UDP or TCP response, which is fo
Source: Google Online Security Blog: CVE-2015-7547: glibc getaddrinfo stack-based buffer overflow