You can buy the IP box on ebay for around $200. It takes 4 – 5 days to unlock any IOS device, even if it has the “Erase data after 10 attempts” configuration setting enabled.
MDSec Blog: Apple iOS Hardware Assisted Screenlock Bruteforce.

You can buy the IP box on ebay for around $200. It takes 4 – 5 days to unlock any IOS device, even if it has the “Erase data after 10 attempts” configuration setting enabled.
MDSec Blog: Apple iOS Hardware Assisted Screenlock Bruteforce.
After a years-long review of hundreds of studies, Australia’s top medical research agency has concluded that homeopathy is essentially useless for treating any medical condition.
Researchers with the National Health and Medical Research Council conducted a review of published studies on homeopathy and report that they could not find any good quality evidence to support the claim that homeopathy works any better than a placebo or sugar pill.
Homeopathy is a centuries-old form of alternative medicine that has been dismissed as pseudoscience by many skeptics. It’s based on a premise that "like cures like." Practitioners believe that herbs and extracts that cause symptoms such as headaches in healthy people will also cure headaches if they are given in highly diluted forms.
via Homeopathy not effective for any medical condition: review | CTV News.
The technique required the men to have their lower arms amputated and fitted with a robotic replacement which responds to electrical impulses when the muscles contract in the same way as a real hand.
“In effect, brachial plexus avulsion injuries represent an inner amputation, irreversibly separating the hand from neural control,” said Professor Oskar Aszmann, Director of the Christian Doppler Laboratory for Restoration of Extremity Function at the Medical University of Vienna, who pioneered the technique.
via Watch: Star Wars-style ‘bionic hand’ fitted to first patients – Telegraph.
Xiaomi Mi Note: This Chinese Phone Is Great. Too Bad You Can't Use It..

Around USD 300,- much cheaper than any equivalents. They also sell better cheaper GoPro cameras!
No removable battery!?!?!
So sad, goodbye Samsung :'(
Your New Galaxy S6 Will Have a Built-In Expiration Date.
From the guys who built LOMAC
Digital Combat Simulator.
Graham told a confused Bloomberg News: "I’ve tried not to have a system where I can just say the first dumb thing that comes to my mind. I’ve always been concerned. I can get texts, and I call you back, if I want."
McCain meanwhile said this: "I’m afraid that if I was emailing, given my solid, always calm temperament that I might email something that I might regret. You could send out an email that you would regret later on and would be maybe taken out of context."
This makes perfect sense to me – people are people, not reasoning machines. People make mistakes and they don’t want their mistakes to be replayable through never deletable digital media. The article slams them for this, but basically the writers are saying there should be no expectation of people in power actually being humans. Because people can be called out for any infestimally stupid thing they ever do over email, far after the fact and without any context attached these people have been pushed out of using modern communications because the risks far outweigh the usefulness.
"rowhammer", rapidly writes and rewrites memory to force capacitor errors in DRAM, which can be exploited to gain control of the system. By repeatedly recharging one line of RAM cells, bits in an adjacent line can be altered, thus corrupting the data stored.
This corruption can lead to the wrong instructions being executed, or control structures that govern how memory is assigned to programs being altered – the latter case can be used by a normal program to gain kernel-level privileges.
via Ouch! Google crocks capacitors and deviates DRAM to root Linux • The Register.
Dutch courts have decided that the ubiquitous tracking of every person in the nation is at variance with the right to having a private life and has to be stopped immediately.
Hopefully the NL Gov (of which the Justice department is very disappointed with the verdict, the house of commons less so) will not appeal this decision but instead make a different law that mandates the collection of this kind of data only after a judge has deemed it necessary on a case by case basis.
ECLI:NL:RBDHA:2015:2498, Rechtbank Den Haag, C/09/480009 / KG ZA 14/1575.
Once Apple saw it they went for the patent and yesterday got it. Prior art? Never heard of it. Well done Apple for copying someone else – yet again. And well done the patent system for giving up patents to people who have not rights to them. Yet again.
Apple patenteert Samsungs Edge-scherm – Webwereld.
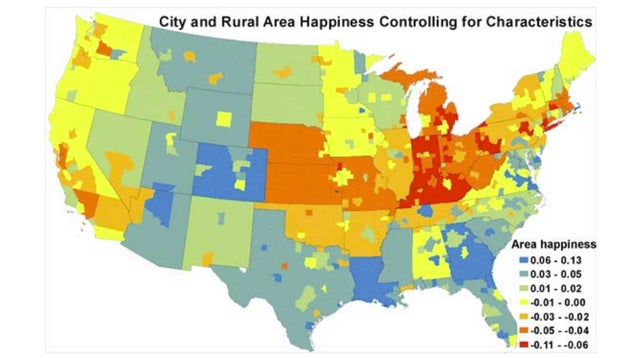
All other things being equal, the south, parts of the west, and upper midwest are the happiest places in the United States according to a recent study.
Researchers from Harvard University and the University of British Columbia took data from the Centers for Disease Control and Prevention which asked 300,000 individuals to report on their life satisfaction each year between 2005 and 2009. The analysts took this data and other demographic variables to compare differences in happiness across regions, while controlling for things like employment status and income.
via This Map Shows Where the Happiest and Unhappiest People Live in the US.
Pinterest promoters zonder werk na 'spamklem' – Emerce.
wow – killing your most active userbase is an awesome plan!
Epic’s software tries to do more than mine crypto-currencies, we’re told: like the distributed SETI@home and BOINC projects, it spreads workloads over a large number of home computers, and can use their spare processor cycles to analyze genomes, fold proteins, and so on. But it mostly mines Litecoin.
via Litecoin-mining code found in BitTorrent app, freeloaders hit the roof • The Register.
A Supreme Court decision handed down on Wednesday has given carte blanche to police forces to retain personal data they have collected for virtually any purpose and hold it as long as they like – even when the people targeted are not violent and have committed no crime.
via UK Supreme Court waves through indiscriminate police surveillance • The Register.
Tough Men for Hire: Ex-Special Forces in Demand for War on Terror | Military.com.
A good look at how mercenaries are now at the forefront of training armies, since the collapse of Blackwater.
a description of personal traits increased likeability when it: showed who the dater was and what they were looking for in a 70:30 ratio; stayed close to reality; and employed simple language with humour added. Invitations were most successful in obtaining a response from the potential date when they: were short personalised messages addressing a trait in their profile; rhymed with their screen name or headline message; and extended genuine compliments. Online communication was most effective in leading to an in-person meeting if there were: a genuine interest; a rapid turnaround; reciprocity in self-disclosure; mimicry of body movements on the webcam; avoidance of criticism; humour; uncertainty about whether there was likeability; and an early move from electronic chat to a date.
Conclusions Attraction and persuasion research provides an evidence-based approach to online dating.
The superfish software shipped with Lenovo laptops can intercept and redirect your secure browsing sessions (eg to your bank) so that third parties can hijack them.
You can test to see if your Lenovo product is infected, how to do so is included in the link below. It can also be removed, again instructions in the link.
Lenovo for years has been known as (one of) the best laptop makers out there. I use one and have recommended them to many of my friends. This brand is hugely popular with IT professionals. This changes everything. Any company that allows spyware to be shipped on their systems and then denies it goes onto my boycott list – just like Sony is. This is a real disaster.
So long, Lenovo, and no thanks for all the super-creepy Superfish • The Register.
Why revise HTTP?
HTTP/1.1 has served the Web well for more than fifteen years, but its age is starting to show.
Loading a Web page is more resource intensive than ever (see the HTTP Archive’s page size statistics), and loading all of those assets efficiently is difficult, because HTTP practically only allows one outstanding request per TCP connection.
In the past, browsers have used multiple TCP connections to issue parallel requests. However, there are limits to this; if too many connections are used, it’s both counter-productive (TCP congestion control is effectively negated, leading to congestion events that hurt performance and the network), and it’s fundamentally unfair (because browsers are taking more than their share of network resources).
At the same time, the large number of requests means a lot of duplicated data “on the wire”.
via HTTP/2 Frequently Asked Questions.
Despite privacy concerns and doubts over its usefulness, a plan to track passengers entering or leaving the European Union in a series of national databases is likely to become reality by the end of the year.
The call to build national databases of so-called passenger name records (PNRs) has become louder since the recent terror attacks in Paris in which 17 people were killed.
via EU air passenger surveillance system could be ready for take-off by year end | ITworld.
Because centralised databases are a really great idea, as we’ve seen from all the times they have been abused and lost on USB sticks.
Of course it’s hardly surprising that the Chalie Hebdo affair would be used to limit our freedom of movement.
The Wassenaar Arrangement, signed by 42 nations, can be implemented differently by each of these nations. Hackers are worried that exploits are controlled by these arms controls and will be punishable.
Leaving 0-day exploits in the wild or unpublished is not good for IT security, as only the people who have them can use them and there is no incentive to report them to the makers of the software, or for the makers to fix them (if they know about them)
Hackers fear arms control pact makes exporting flaws illegal • The Register.
By learning about the habits of co-workers in over 100 financial institutions, mainly in Russia, the hackers infected computers using spear fishing techniques. They upped the balance of accounts and transferred away the excess money. They also programmed PIN machines to spit out money at specified times.
Hackers stelen 1 miljard dollar bij 'grootste bankroof ooit' – UPDATE 2 – Webwereld.
As well as several other officers, they were bribed to the tune of hundreds of thousands of dollars, allowing the company doing the bribing to overcharge for around $20 million dollars.
3 Rear Admirals Forced Out Amid Massive Navy Bribery Scandal | Military.com.