Since Apple implemented a browser choice screen for iPhones earlier this month to comply with Europe’s Digital Markets Act (DMA), Brave Software, Mozilla, and Vivaldi have seen a surge in the number of people installing their web browsers.
It’s an early sign the Europe Union’s competition rules may actually … get this … enhance competition – an outcome that skeptics deemed unlikely.
The DMA applies to a set of six technology giants that have been designated as “gatekeepers” in order to limit their tendency to boost the usage of their own offerings – such as their own browsers, webmail, and marketplaces – to the detriment of rivals, which are pushed out of the way.
This walloping of competitors, which slashes choice and innovation, is usually achieved through default settings, contractual requirements, and other mechanisms that favor the big players over smaller upstarts. Apple and Google, as two of those gatekeeper firms, must now under Euro law make concessions to competitors to avoid further harm.
As a direct result of Europe’s DMA, Apple announced plans to implement a browser choice screen on iOS devices in January.
For Google, the DMA compliance means a browser choice screen and search choice screen on Android smartphones and tablets during device setup, as well as a search choice screen for its Chrome browser on non-Android platforms.
Choice screens can be an effective way to reduce market dominance. For example: in 2010, when Microsoft was required to provide a browser choice screen in Windows in Europe, Opera reported that its download numbers had doubled.
[…]
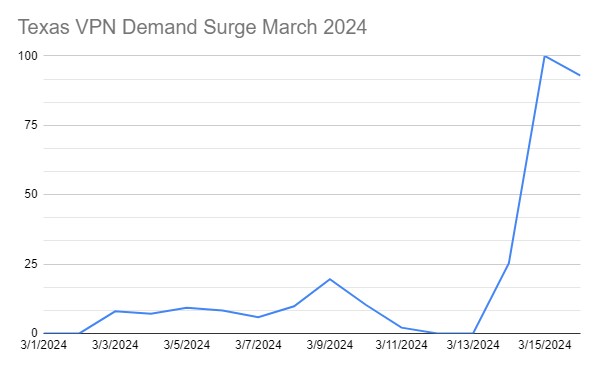
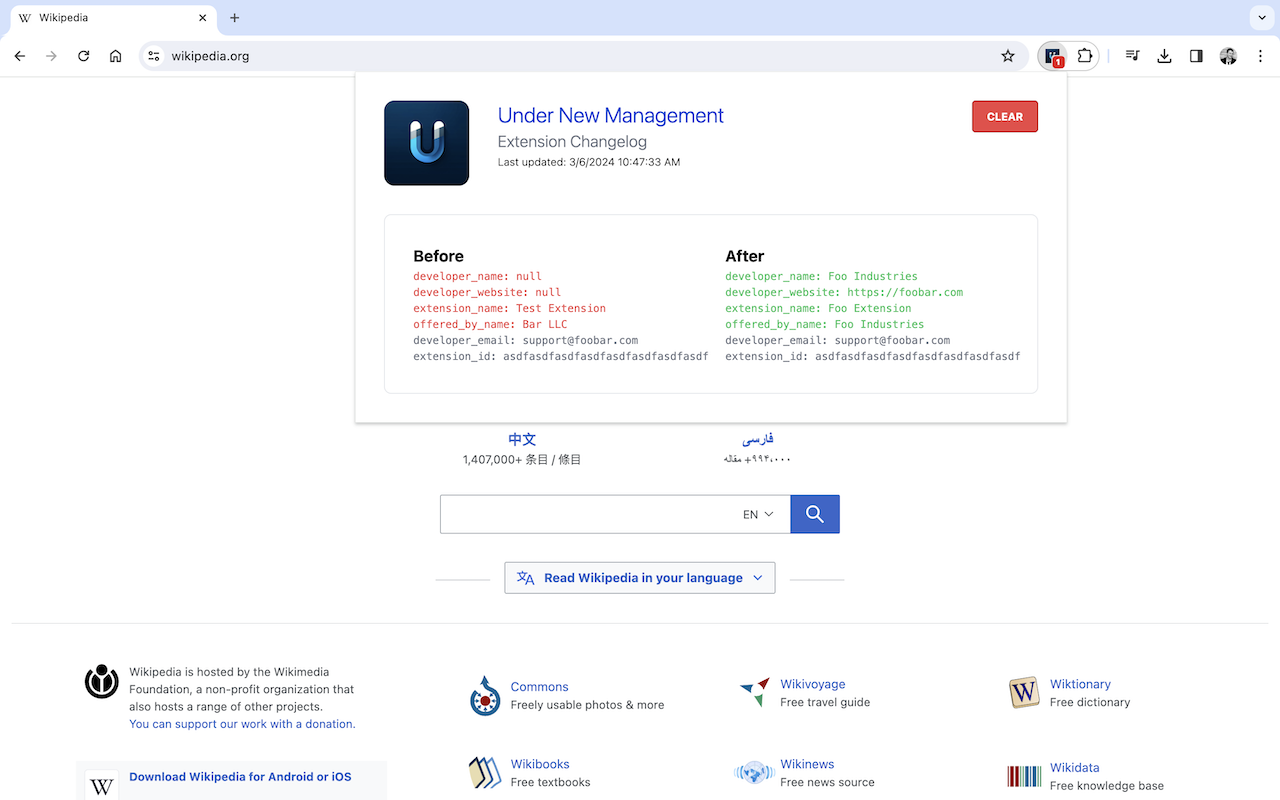
Brave’s figures suggest the number of daily browser installs jumped from around 8,000 on March 6, 2024 to around 11,000 a week later. And in a social media post, the developer cited those results as evidence that Apple and Google have made it hard to switch default browsers specifically to block competition.
“Monopoly defenders argue that the monopolies simply offer better products,” Brave declared. “But as you can see, when consumers get a clear choice of iOS browsers, they’re choosing alternatives to Safari. Maybe that’s why Google still hasn’t implemented a browser choice screen on Android.”
[…]
For most of us, Apple requires browsers on iOS to use Cupertino’s WebKit engine – Europe has strong-armed the iGiant into ditching that stipulation in its region.
[…]
The monopolistic practices employed by Big Tech have often hindered Firefox’s ability to innovate and offer users competitive alternatives,” a Moz spokesperson told The Register. “It is no small feat for us to cut through their tricky tactics to keep consumers locked within their own ecosystems.
“Despite less than ideal compliance, the recent implementation of the DMA choice screen is a promising step toward true competition online in the EU, which is why we’re not surprised to have seen a more than 50 percent increase in Firefox user growth in Germany and close to 30 percent increase in France just since its implementation. Still, there is a lot of room for improvement, and we’ll continue to fight for a web that puts people over profits, prioritizes privacy and is open and accessible to all.”
[…]
“We are still reviewing the technical details but are extremely disappointed with Apple’s proposed plan to restrict the newly-announced BrowserEngineKit to EU-specific apps,” Mozilla’s spokesperson lamented. “The effect of this would be to force an independent browser like Firefox to build and maintain two separate browser implementations – a burden Apple itself will not have to bear.
“Apple’s proposals fail to give consumers viable choices by making it as painful as possible for others to provide competitive alternatives to Safari. This is another example of Apple creating barriers to prevent true browser competition on iOS.”
[…]
Von Tetzchner criticized the way the browser choice screen has been implemented, noting that the user has to first click on Safari before being presented with the choice screen that provides non-Safari options. He also observed that if a user has gone ahead and chosen a default browser that’s not listed on Apple’s choice screen, when iOS next presents the choice screen, it won’t include the user’s already designated browser.
He expects Apple will be asked to make further accommodations, based on the fact that it has already had to backtrack several times.
“The point of all of this is to create competition,” noted von Tetzchner. “The point of this is there are certain companies that are gatekeepers that cannot control access to other applications with which they compete. And the point is to create a level playing ground. I think it’s very clear that there isn’t a level playing ground with this.”
Von Tetzchner told us he hasn’t seen Google’s choice screen, because it hasn’t debuted yet.
“I’ve been told by Google that it’s something that they came to an agreement about with the European Commission and the fact that I got that from Google is one of the differences that we see with different organizations here. We actually have a contact at Google. They have a contact with Microsoft and we’ve still not managed to get any contact at Apple, which is rather special.”
According to von Tetzchner, Cupertino has been telling the European Commission that no one will talk to Apple, when it’s the opposite situation.
“We’ve been trying really hard to get hold of anyone at Apple who will talk to us,” he said. “And that’s not happening. And again, I’m hearing the same from the other browser makers.”
[…]




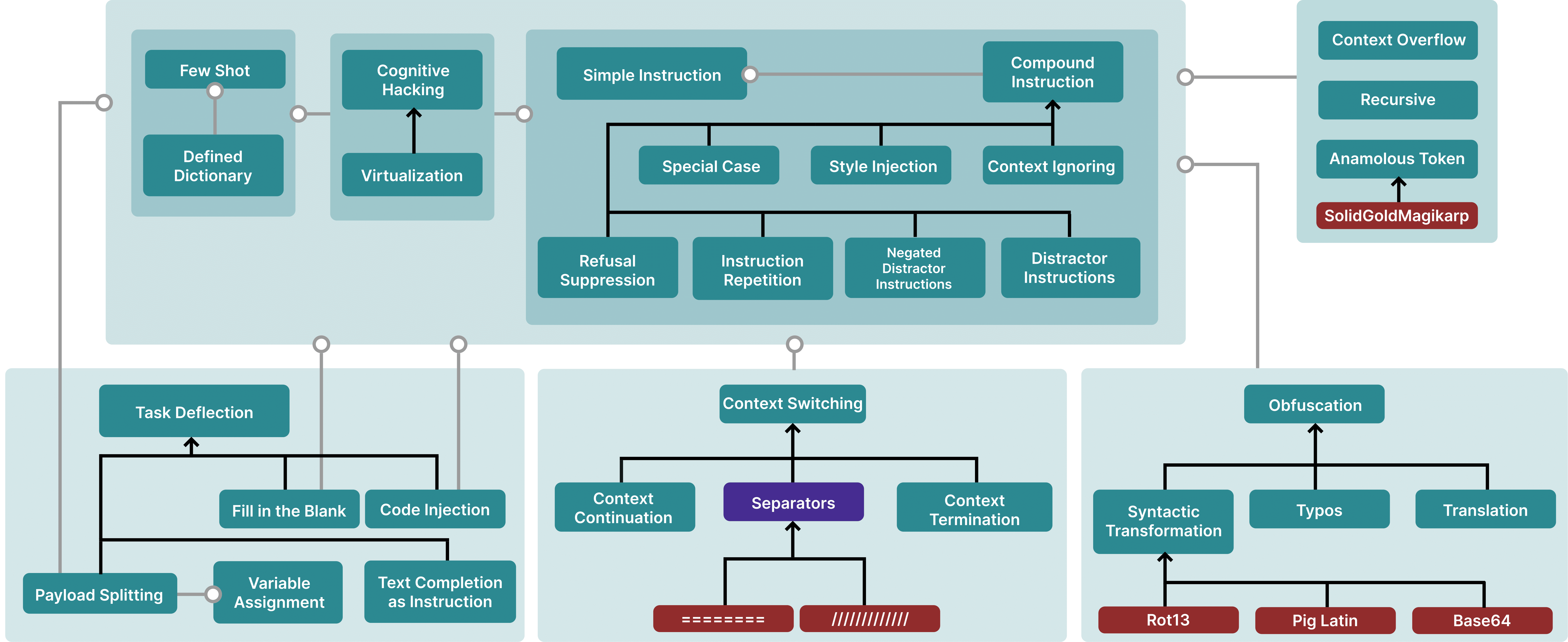 Figure 5: A Taxonomical Ontology of Prompt Hacking techniques. Blank lines are hypernyms (i.e., typos are an instance of obfuscation), while grey arrows are meronyms (i.e., Special Case attacks usually contain a Simple Instruction). Purple nodes are not attacks themselves but can be a part of attacks. Red nodes are specific examples.
Figure 5: A Taxonomical Ontology of Prompt Hacking techniques. Blank lines are hypernyms (i.e., typos are an instance of obfuscation), while grey arrows are meronyms (i.e., Special Case attacks usually contain a Simple Instruction). Purple nodes are not attacks themselves but can be a part of attacks. Red nodes are specific examples.