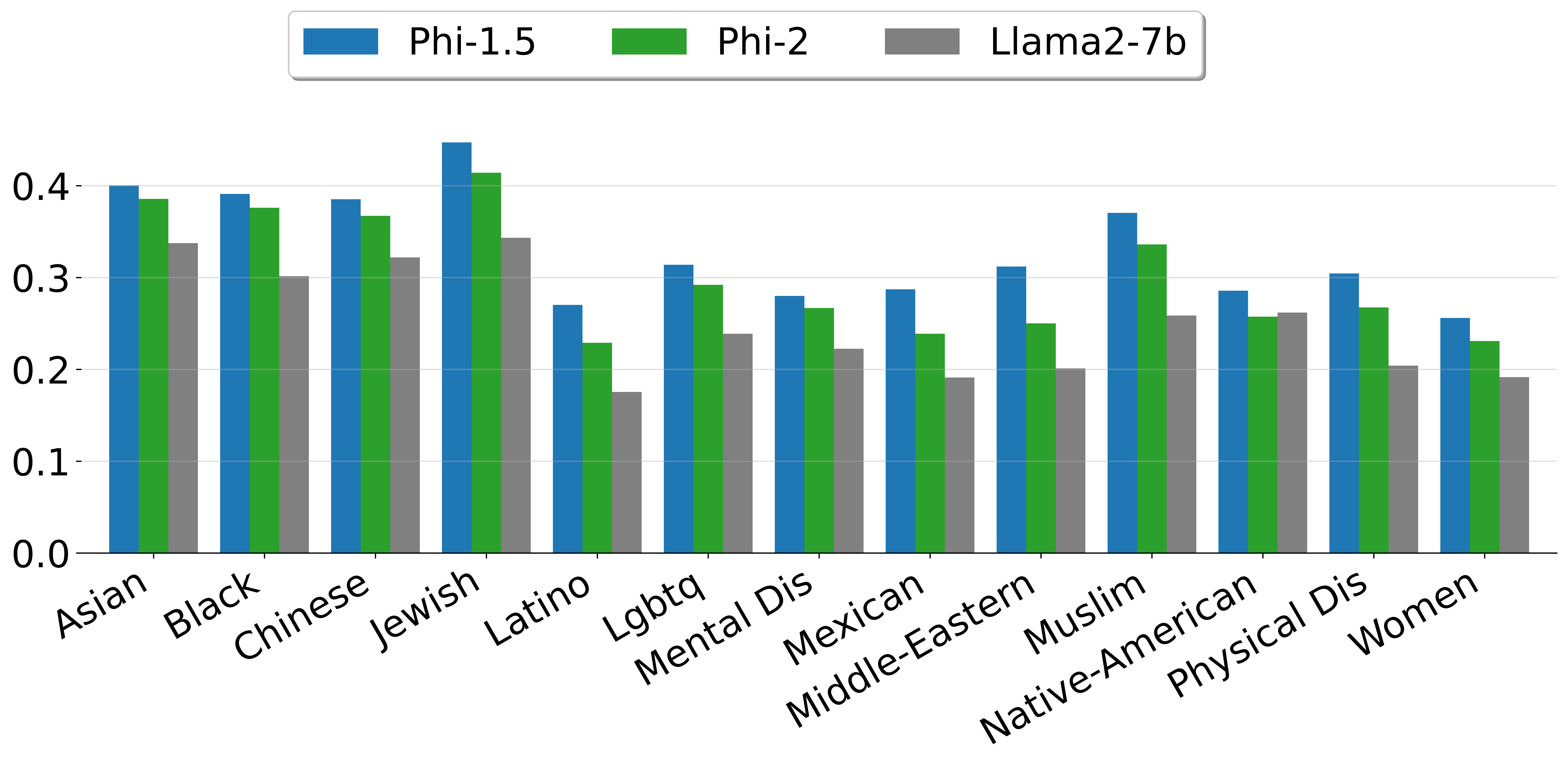
On December 11th, a jury decided that Google has an illegal monopoly with its Google Play app store, handing Epic Games a win. But Epic wasn’t the only one fighting an antitrust case. All 50 state attorneys general settled a similar lawsuit in September, and we’ve just now learned what Google agreed to give up as a result: $700 million and a handful of minor concessions in the way that Google runs its store in the United States.
The biggest change: Google will need to let developers steer consumers away from the Google Play Store for several years, if this settlement is approved.
You can read the full 68-page settlement for yourself at the bottom of this story, but here’s the TL;DR about what it includes:
- $700,000,000 from Google in total (roughly 21 days of Google’s operating profit from the app store alone)
- $629,000,000 of which will go to consumers who may have overpaid for apps or in-app purchases via Google Play after taxes, lawyers’ fees, and so on
- $70,000,000 of which will go to states to be used as the state AGs see fit
- $1,000,000 of which is for settlement administration
- For 7 years, Google will “continue to technically enable Android to allow the installation of third-party apps on Mobile Devices through means other than Google Play”
- For 5 years, Google will let developers offer an alternative in-app billing system next to Google Play (aka “User Choice Billing”)
- For 5 years, Google won’t make developers offer their best prices to customers who pick Google Play and Google Play Billing
- For 4 years, Google won’t make developers ship titles on Google Play at the same time as other stores and with feature parity
- For 5 years, Google won’t make companies exclusively put Google Play on a phone or its homescreen
- For 4 years, Google won’t stop OEMs from granting installer rights to preloaded apps
- For 5 years, Google won’t require its “consent” before an OEM preloads a third-party app store
- For 4 years, Google will let third-party app stores update apps without requiring user approval
- For 4 years, Google will let sideloaded app stores use its APIs and “feature splits” to help install apps
- For 5 years, Google will turn its two sideloading “scare screens” into a single user prompt which will read the equivalent of this agreed-upon language: “Your phone currently isn’t configured to install apps from this source. Granting this source permission to install apps could place your phone and data at risk.”
- For 5 years, Google will let User Choice Billing participating developers let their users know about better pricing elsewhere and “complete transactions using the developer’s existing web-based billing solution in an embedded webview within its app.”
- For 6 years, Google will “continue to allow developers to use contact information obtained outside the app or in-app (with User consent) to communicate with Users out-of-app”
- For 6 years, Google will let consumption only apps (e.g. Netflix, which doesn’t let you pay on device) tell users about better prices elsewhere, without linking to an outside website — example: “Available on our website for $9.99”
- For 6 years, Google “shall not prohibit developers from disclosing to Users any service or other fees associated with the Google Play or Google Play’s billing system.”
Does that sound like a lot? If you add it all up, it does make for a slightly different Google app store landscape than we’ve experienced over the past decade and change. But not only does every one of these concessions have an expiration date, many of them are arguably not real concessions.
Google argued during the Epic v. Google trial that users were already perfectly able to install third-party apps on their devices through any number of means, and it claimed many of its agreements with developers, OEMs, and carriers did not require them to, for instance, exclusively put Google Play on a phone or its homescreen.
More importantly, several of the most significant sounding changes here are tied to Google’s User Choice Billing program — which is mostly a fake choice, the Epic v. Google trial proved.
We confirmed with Google spokesperson Dan Jackson this evening that User Choice Billing participants are given a discounted rate of just 4 percent off of Google’s fee when users choose their own payment system, and that it won’t change as a result of the settlement. Not only did Google internally find that developers would lose money when users choose the 4 percent rate, but Google also gives companies like Spotify a free ride while apparently charging everyone else.
Perhaps most importantly, Google is reserving the right not to let developers like Netflix link to their own websites to give their users a discounted rate. “Google is not required to allow developers to include links that take a User outside an app distributed through Google Play to make a purchase,” the settlement agreement reads. We are still waiting to find out whether Apple will allow links and/or buttons to alternative payment systems, based on the ruling in Epic v. Apple. But the Google / state AGs settlement suggests that regardless, Google will not be required to allow links.
[…]
Source: Google to pay $700 million and make tiny app store changes to settle with 50 states – The Verge
It’s still baffling that Google lost this case and Apple won it on almost exactly the same grounds, where in Google’s case you can actually sideload apps “legally” (if in an obtuse manner which makes you think you are doing something wrong) and in Apple’s you can’t.