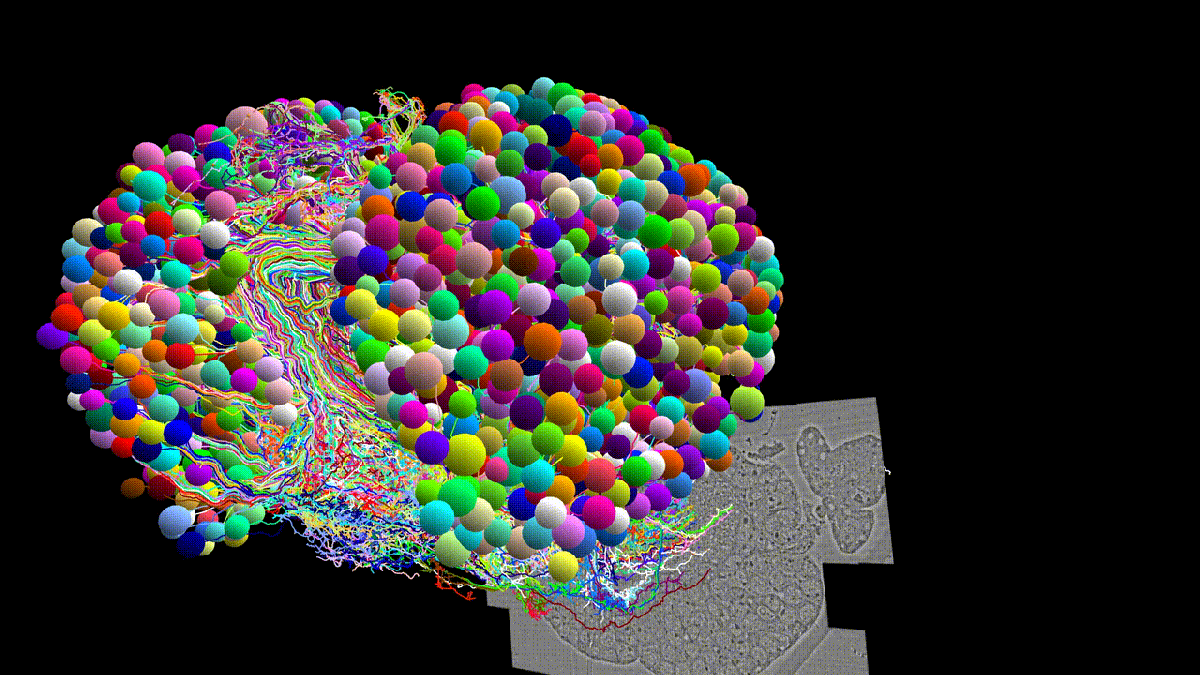
[…] An interdisciplinary team of scientists have released a complete reconstruction and analysis of a larval fruit fly’s brain, published Thursday in the journal Science. The resulting map, or connectome, as its called in neuroscience, includes each one of the 3,016 neurons and 548,000 of the synapses running between neurons that make up the baby fly’s entire central nervous system. The connectome includes both of the larva’s brain lobes, as well as the nerve cord.
[…]
It is the most complete insect brain map ever constructed and the most intricate entire connectome of any animal ever published. In short: it’s a game changer.
For some, it represents a paradigm shift in the field of neuroscience. Fruit flies are model organisms, and many neural structures and pathways are thought to be conserved across evolution. What’s true for maggots might well be true for other insects, mice, or even humans.
[…]
this new connectome is like going from a blurry satellite view to a crisp city street map. On the block-by-block array of an insect’s cortex, “now we know where every 7-11 and every, you know, Target [store] is,” Mosca said.
To complete the connectome, a group of Cambridge University scientists spent 12 years focusing in on the brain of a single, 6-hour-old female fruit fly larva. The organ, approximately 170 by 160 by 70 micrometers in size, is truly teeny—within an order of magnitude of things too small to see with a naked eye. Yet, the researchers were able to use electron microscopy to visually cut it into thousands of slices, only nanometers thick. Imaging just one of the neurons took a day, on average. From there, once the physical map of the neurons, or “brain volume,” was complete, the analysis began.
Along with computer scientists at Johns Hopkins University, the Cambridge neuroscientists assessed and categorized the neurons and synapses they’d found. The JHU researchers fine-tuned a computer program for this exact application in order to determine cell and synapse types, patterns within the brain connections, and to chart some function onto the larva connectome—based on previous neuroscience studies of behavior and sensory systems.
They found many surprises. For one, the larval fly connectome showed numerous neural pathways that zigzagged between hemispheres, demonstrating just how integrated both sides of the brain are and how nuanced signal processing can be, said Michael Winding, one of the study’s lead researchers and a Cambridge University neuroscientist, in a video call. “I never thought anything would look like that,” Winding said.
[…]
Fascinatingly, these recurrent structures mapped from an actual brain appear to closely match the architecture of some artificial intelligence models (called residual neural networks), with nested pathways allowing for different levels of complexity, Zlatic noted.
[…]
Not only was the revealed neural structure layered, but the neurons themselves appear to be multi-faceted. Sensory cells connected across modalities—visual, smell, and other inputs crossed and interacted en route to output cells, explained Zlatic. “This brain does a huge amount of multi-sensory integration…which is computationally a very powerful thing,” she added.
Then there were the types and relative quantities of cell-to-cell connections. In neuroscience, the classic “canonical” type of synapse runs from an axon to a dendrite. Yet, within the mapped larval fly brain, that only accounted for about two-thirds of the connections, Winding and Zlatic said. Axons linked to axons, dendrites to dendrites, and dendrites to axons. Scientists have known these sorts of connections exist in animal nervous systems, but the scope went far beyond what they expected. “Given the breadth of these connections, they must be important for brain computation,” Winding noted. We just don’t know exactly how.
[…]
Source: First Complete Map of a Fly Brain Has Uncanny Similarities to AI Neural Networks