“Switch to solar panels to help save the planet,” they say.
And they’re (mostly) right. Solar panels are a great source of clean energy because, unlike fossil fuels, solar energy doesn’t produce harmful carbon emissions while creating electricity. But how “clean” is the process of creating solar panels?
Ironically enough, solar panel production is reliant on fossil fuels. It also involves mining for precious metals, which contributes to greenhouse gasses and pollution.
Before we explore the extent of it, we want to be clear that we’re not here to tear down the use of solar panels. EcoWatch is a huge fan of solar energy and has helped hundreds of homeowners reduce their carbon emissions by going solar. But we want to be transparent about the impact that solar panels have on the environment — both good and bad.
The Carbon Footprint of a Solar Panel
While solar panels are an environmentally friendly energy solution, the materials and manufacturing process used to create them do have a decent-sized carbon footprint, as they involve mining, melting and cooling to be used.
Environmental Impact of Mining for Solar Panel Materials
Most solar cells are made up of silicon semiconductors and glass, as well as metals like silver, copper, indium and tellurium. And if we’re including solar batteries, add lithium to the list.
When it comes to environmental impact, gathering silicon and glass are both non-issues, as they’re abundant and non-toxic. However, the process of mining for those metals creates greenhouse gas emissions and can lead to soil, water and air pollution.1
Environmental Impact of Solar Panel Facilities
First thing to consider: Solar facilities are massive. It’s safe to assume that, in most cases, some wildlife and recreation land has been cleared to create solar panel production facilities.
Solar panel facilities also require a lot of energy to keep up and running, and unfortunately, a lot of the energy used for melting down silicon comes from coal burning, especially in China where pollution emissions are already high.2
There’s also a great need for water for the cooling process, which can be an environmental strain in more arid areas where water isn’t as available. And like any big production facility, solar panel production facilities cause air pollution.
Environmental Impact of Solar Panel Manufacturing
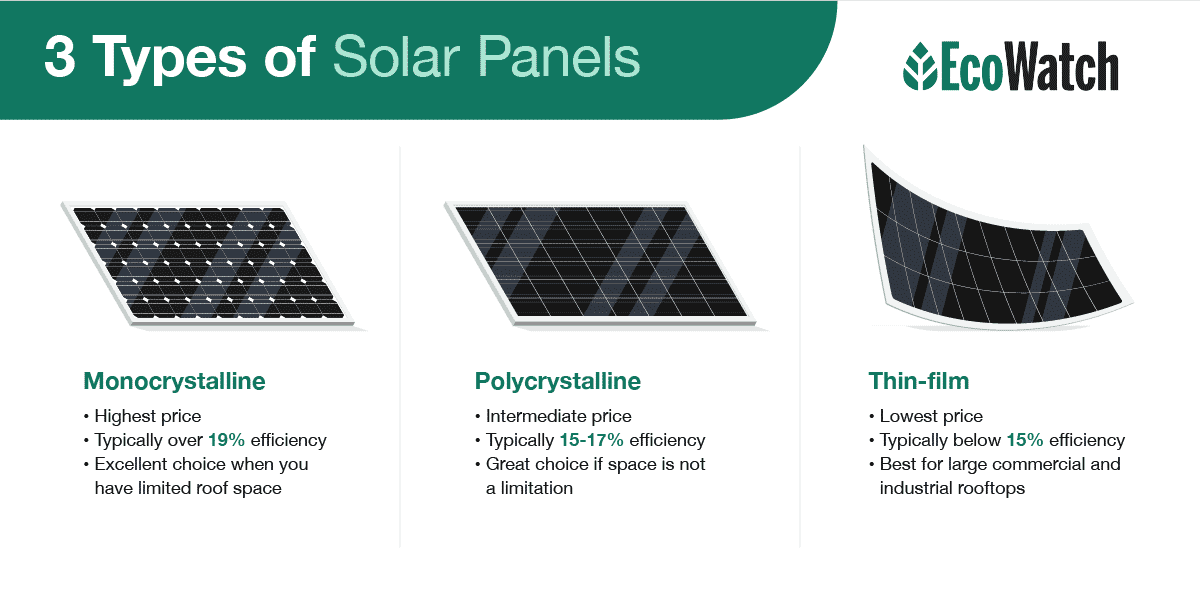
There are three different types of solar panels — monocrystalline, polycrystalline and thin-film — and each are manufactured differently, meaning they each leave a different sized carbon footprint.
Manufacturing Monocrystalline Panels
Monocrystalline panels are the most common and have the highest energy conversion efficiency, typically ranging between 19 and 22%. Monocrystalline solar panels are made of pure, single-cell silicon crystals wedged between thin glass.
To make a monocrystalline solar panel, a huge piece of silicon is molded into a block, then cut into small wafers to be affixed onto a solar panel. It’s a complex process and, therefore, produces the highest emissions compared to any other solar panel manufacturing method.3
Manufacturing Polycrystalline Panels
Polycrystalline solar panels are also made of silicon, but instead of coming from a block, the silicon crystals are melted together and then placed onto the panel. Because of the melting process, polycrystalline solar panels do require a bit of electricity to create, although not as much as monocrystalline.4
Manufacturing Thin-Film Panels
Lastly, you have thin-film solar panels, which can be made from several different types of materials, like amorphous silicon, cadmium telluride (a type of silicon) or copper indium gallium selenide. T
ypically, thin-film solar panels are going to leave a smaller carbon footprint compared to their more popular counterparts.5 But on the downside, they’re created from extremely toxic materials that can lead to both human and environmental harm if not handled properly.6
Environmental Impact of Transporting Solar Panels
Emissions from solar panel transportation present another challenge. Solar panels are produced all over the world, but primarily in China, followed by the U.S. and Europe. And solar panels that are produced in one country may require shipments of parts from another.
To be honest, it’s hard to say exactly how big the carbon footprint is for each stage of making a solar panel — no matter which type. There hasn’t been much research or data released on the environmental impact of solar panel production. However, the Coalition on Materials Research Transparency is reportedly working to measure and report the carbon impacts associated with mining, producing and transporting solar panels.
It’s important to note that the amount of carbon emissions produced to create solar panels is still nowhere near that of traditional energy facilities, and it is quite small when compared to oil drilling, fracking or coal mining.7
But production aside, another common challenge surrounding solar panels is what happens after their average 25-year lifespan.
A Larger Issue: Solar Panel Recycling
The Solar Energy Industries Association (SEIA) set a target for solar energy to account for 30% of energy generation in the U.S. by 2030.8 If that target is hit, more than 1 billion solar panels will be actively collecting solar energy throughout the U.S. alone over the next decade.
While this is great news for reducing carbon emissions, it brings up a larger issue the solar industry hasn’t quite nailed down yet: solar panel recycling.
Scientists have been working on a better solution, but as of now, there isn’t a flushed-out system to recycle old solar panels. And there certainly aren’t enough places to do it.
As mentioned earlier, solar panels are made up of a lot of precious metals, and the carbon footprint of producing solar panels could be reduced if these materials could be recycled and repurposed instead of having to mine for more. Instead, lack of solar panel recycling availability is only creating more e-waste, which could eventually lead to solar panel material scarcity.
How Much Better is Solar for the Environment?
We’ve discussed all the ways in which solar panels can be harmful to the environment, but let’s not forget that they’re still a far better option than non-renewable energy alternatives.
Taking the carbon footprint of solar panels into account, one study still found that coal generates a footprint 18 times the size, while natural gas creates an emissions footprint 13 times the size of solar.9 It’s also worth repeating that solar energy produces zero emissions after production. For that reason alone, studies have revealed solar to be an essential solution to slowing climate change.10
But if solar continues to grow as the SEIA predicts it will, technology will also need to improve to minimize the effects that solar panel production will have on the environment, and proper solar panel recycling methods must be created.