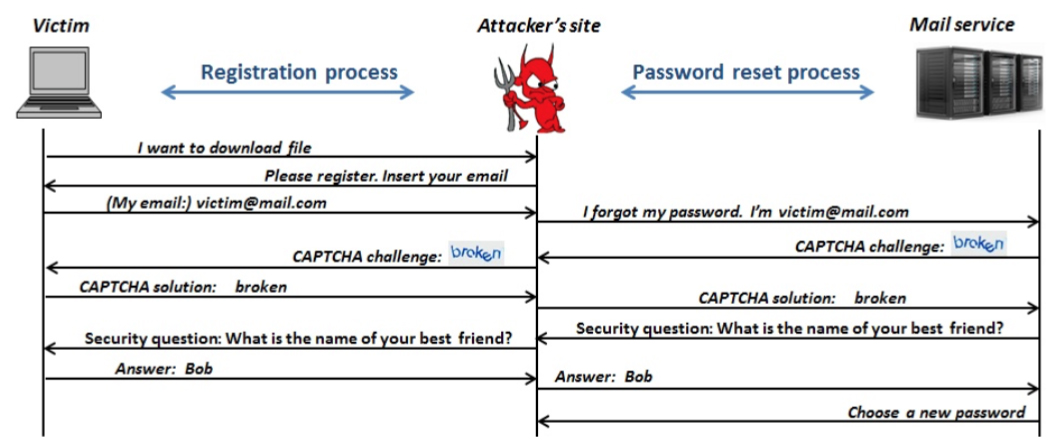
The Password Reset Man in the Middle (PRMITM) attack exploits the similarity of the registration and password reset processes.
To launch such an attack, the attacker only needs to control a website. To entice victims to make an account on the malicious website, the attacker can offer free access to a wanted resource (e.g. free software). Once the user initiates the account registration process by entering their email address, the attacker can use that information to initiate a password reset process on another website that uses that piece of information as the username (e.g. Google, YouTube, Amazon, Twitter, LinkedIn, PayPal, and so on).
Every request for input from that site is forwarded to the potential victim, and then his or her answers forwarded back to that particular site.
Source: Password Reset MITM: Exposing the need for better security choices – Help Net Security
That this works is down to some serious cognitive laziness during the registration process!

Robin Edgar
Organisational Structures | Technology and Science | Military, IT and Lifestyle consultancy | Social, Broadcast & Cross Media | Flying aircraft