Purdue University researchers reckon they’ve cracked how to protect data against “disk-wipe” malware.
Led by Christopher Gutierrez, the team has created a shim of software that analyses write buffers before they reach storage, and if the write is destructive, it steps in to preserve the data targeted for destruction.
Dubbed R2D2 – “Reactive Redundancy for Data Destruction Protection” – their work will be published in the May issue of the journal Computers & Security.
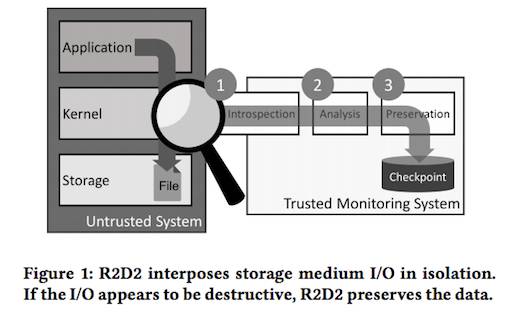
In this [PDF] pre-press version of the paper, the researchers explained their technique. The inspection is implemented in the virtual machine monitor (VMM) using virtual machine introspection (VMI).
“This has the benefit that it does not rely on the entire OS as a root of trust”, they wrote, and they claimed a latency penalty of between 1 and 4 per cent for batch tasks, and 9 to 20 per cent for interactive tasks.
The system has been tested against various secure delete tools and malware like Shamoon and Stonedrill, and they claim complete success against “all the wiper malware samples in the wild that we experimented with”.
R2D2 intercepts the open file and write file system calls on a guest VM. When it detects an open file request, it checks “all open system calls” to see if the file is already open for writing.
“If the system call requests a write permission, a policy determines if the file should be protected based on a blacklist or whitelist,” they wrote.
Whitelisted files are those not protected; if a blacklisted file is requested, “If the file is on the blacklist, we take a snapshot of the file system because the file is considered critical to system stability.”
If the attacker tries to open a file on neither list, “R2D2 takes a temporary checkpoint of the file system, and subsequent write system calls are analysed, according to analysis policy, to determine if the write is suspect”.
Source: ‘R2D2’ stops disk-wipe malware before it executes evil commands • The Register

Robin Edgar
Organisational Structures | Technology and Science | Military, IT and Lifestyle consultancy | Social, Broadcast & Cross Media | Flying aircraft