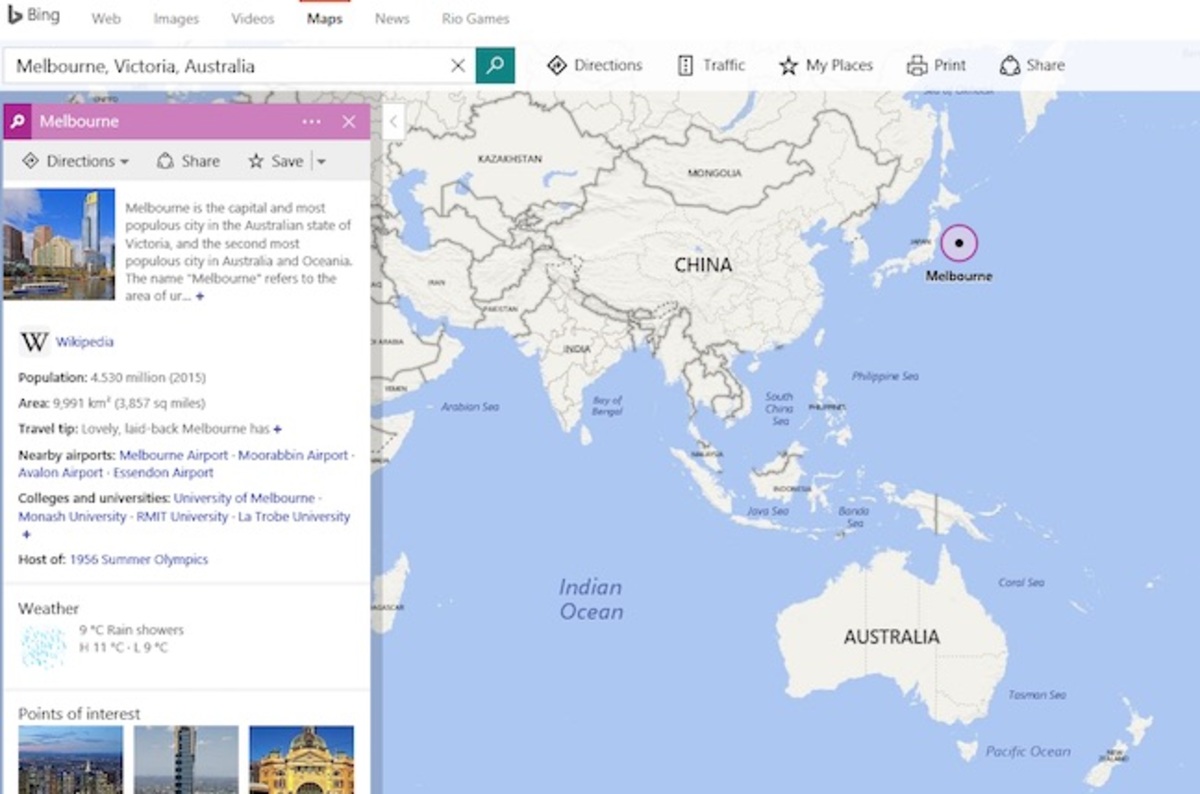
Microsolderer Jessa Jones can fix practically anything. But these days, she spends most of her time fixing just one thing. Because every single month, more and more iPhone 6 and (especially) 6 Plus devices show up at her shop with the same problem: a gray, flickering bar at the top of the display and an unresponsive touchscreen. And she’s not the only one. Repair pros all over the country are noticing the same trend.
[…]
Replacing the touchscreen doesn’t fix the problem. The gray bar eventually shows up on the new screen, too. Because, according to repair pros, the problem isn’t the screen at all. It’s the two touchscreen controller chips, or Touch IC chips, on the logic board inside the phone.
[…]
Apple’s repair Geniuses aren’t equipped to make specialized repairs to the logic board in-house, so they can’t actually fix Touch Disease. But skilled, third-party microsoldering specialists (most “unauthorized” to do Apple repairs, according to official company policy) can fix phones with symptoms of Touch Disease. And they can do it a whole lot cheaper than the cost of a new logic board or an out-of-warranty phone replacement.
[…]
the most popular theory I heard is that Touch Disease is the unanticipated, long-term consequence of a structural design flaw: Bendgate.
Source: A Design Defect Is Breaking a Ton of iPhone 6 Pluses