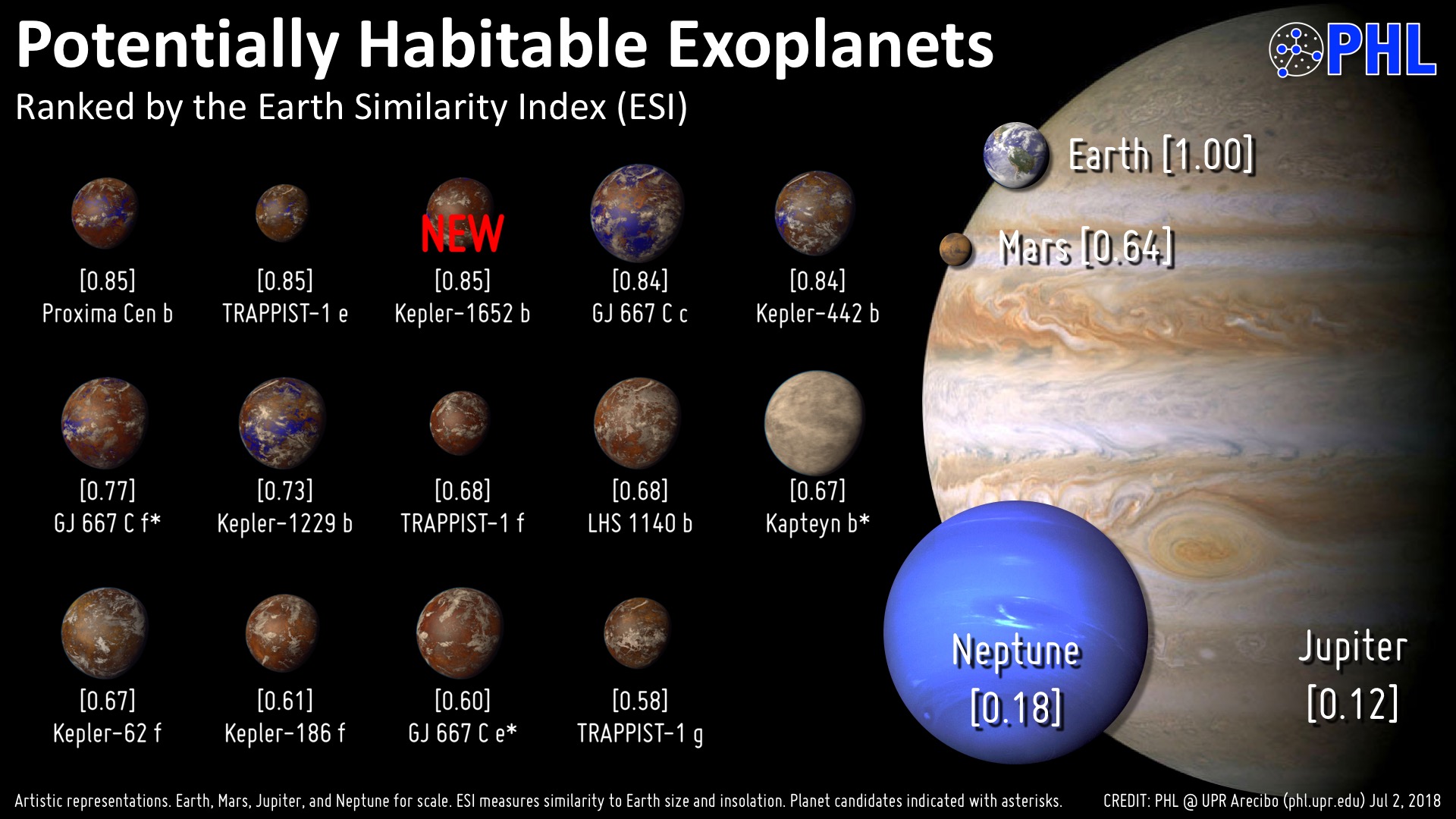
Planetary Habitability Laboratory

The European Union (EU) has voted on Tuesday, November 14, to pass the new Consumer Protection Cooperation regulation, a new EU-wide applicable law that gives extra power to national consumer protection agencies, but which also contains a vaguely worded clause that also grants them the power to block and take down websites without judicial oversight.
The new law “establishes overreaching Internet blocking measures that are neither proportionate nor suitable for the goal of protecting consumers and come without mandatory judicial oversight,” Member of the European Parliament Julia Reda said in a speech in the European Parliament Plenary during a last ditch effort to amend the law.
“According to the new rules, national consumer protection authorities can order any unspecified third party to block access to websites without requiring judicial authorization,” Reda added later in the day on her blog.
This new law is an EU regulation and not a directive, meaning its obligatory for all EU states, which do not have to individually adopt it.
Last month, the European Consumer Organization (BEUC) warned that smartwatches marketed to kids were a serious threat to children’s privacy. A report published by the Norwegian Consumer Council in mid-October revealed serious flaws in several of the devices that could easily allow hackers to seize control.
Doing so could grant attackers access to both real-time and historical locational data, as well as a wealth of personal information.
You have to wonder who thought attaching a low-cost, internet-enabled microphone and a GPS tracker to a kid would be a good idea in the first place. Almost none of the companies offering these “toys” implement reasonable security standards, nor do they typically promise that the data they collect—from your children—won’t be used be used for marketing purposes.
Confido is a startup that pitched itself as a blockchain-based app for making payments and tracking shipments. It sold digital tokens to investors over the Ethereum blockchain in an ICO that ran from November 6 to 8. During the token sale, Confido sold people bespoke digital tokens that represent their investment in exchange for ether, Ethereum’s digital currency.
But on Sunday, the company unceremoniously deleted its Twitter account and took down its website. A company representative posted a brief comment to the company’s now-private subforum on Reddit, citing legal problems that prevent the Confido team from continuing their work. The same message was also posted to Medium but quickly deleted.
“Right now, we are in a tight spot, as we are having legal trouble caused by a contract we signed,” the message stated (a cached version of the Medium post is viewable). “It is likely that we will be able to find a solution to rectify the situation. However, we cannot assure you with 100% certainty that we will get through this.” The message was apparently written by Confido’s founder, one Joost van Doorn, who seems to have no internet presence besides a now-removed LinkedIn profile.
Even the Confido representative on Reddit doesn’t seem to know what’s going on, though, posting hours after the initial message, “Look I have absolutely no idea what has happened here. The removal of all of our social media platforms and website has come as a complete surprise to me.” Motherboard reached out to this representative over Reddit, but hasn’t received a response.
Confido tokens had a market cap of $10 million last week, before the company disappeared, but now the tokens are worthless. And investors are crying foul.
Yup, the wild wild west!
An apparent factory cockup has left OnePlus Android smartphones with an exposed diagnostics tool that can be potentially exploited to root the handsets.
Security researcher Robert Baptiste suggested the EngineerMode APK was made by Qualcomm, and was intended to be used by factory staff to test phones for basic functionality before they are shipped out to the public.
Unfortunately, it seems someone at OnePlus forgot to remove or disable the package before kicking the handsets out to the general public, and as a result folks now have access to what is effectively a backdoor in their Android phones.
In addition to basic diagnostic tasks like checking the functionality of the phone’s hardware components – such as the GPS and wireless electronics – the tool can also allow people, using the password ‘angela’, to obtain root access and gain full control over a device:
Being able to root your phone gives you access to the full functionality of the OS, however. This is something I think is a good idea – there are plenty of apps (eg battery monitors) that require root access to function.
Scientists for the first time have tried editing a gene inside the body in a bold attempt to permanently change a person’s DNA to cure a disease.
The experiment was done Monday in California on 44-year-old Brian Madeux. Through an IV, he received billions of copies of a corrective gene and a genetic tool to cut his DNA in a precise spot.
“It’s kind of humbling” to be the first to test this, said Madeux, who has a metabolic disease called Hunter syndrome. “I’m willing to take that risk. Hopefully it will help me and other people.”
Signs of whether it’s working may come in a month; tests will show for sure in three months.
[…]
“We cut your DNA, open it up, insert a gene, stitch it back up. Invisible mending,” said Dr. Sandy Macrae, president of Sangamo Therapeutics, the California company testing this for two metabolic diseases and hemophilia. “It becomes part of your DNA and is there for the rest of your life.”
Pawnbroking and secondhand goods outlet Cash Converters has suffered a data breach.
Customers were notified of the leak on Thursday by email, samples of which have been posted on social media.
Cash Converters said it had discovered that a third party gained unauthorised access to customer data within the company’s UK webshop.
Credit card data was not stored. However, hackers may have accessed user records including personal details, passwords, and purchase history from a website that was run by a third party and decommissioned back in September. The current webshop site is not affected, the firm said.
Thanks to an investigation by third-party researchers into Intel’s hidden firmware in certain chips, Intel decided to audit its firmware and on Monday confirmed it had found 11 severe bugs that affect millions of computers and servers.
The flaws affect Management Engine (ME), Trusted Execution Engine (TXE), and Server Platform Services (SPS).
Intel discovered the bugs after Maxim Goryachy and Mark Ermolov from security firm Positive Technologies found a critical vulnerability in the ME firmware that Intel now says would allow an attacker with local access to execute arbitrary code.
The researchers in August published details about a secret avenue that the US government can use to disable ME, which is not available to the public.
Intel ME has been a source of concern for security-minded users, in part because only Intel can inspect the firmware, yet many researchers suspected the powerful subsystem had bugs that were ripe for abuse by attackers.
Goryachy and Ermolov will present their research on an ME flaw at Blackhat in December, detailing how an attacker can run unsigned code in the microprocessor and remain invisible to the main CPU and any anti-malware software.
ME runs on its own microprocessor and, as a Google engineer recently revealed, a modified version of the MINIX operating system.
Google was so afraid of UEFI and Intel ME that it created NERF, or the Non-Extensible Reduced Firmware, which it uses to manage Chromebooks. NERF runs on a Linux kernel rather than MINIX and removes ME’s web server and IP stack, key EUFI drivers, and neuters the ability for ME and EUFI to self-reflash the firmware.
The ME engine supports Intel’s Active Management Technology (AMT), which allows admins to remotely manage and fix devices.
A flaw discovered this May in AMT, which affected chips from 2008, highlighted another problem: patching it required an ME firmware update on machines that hardware vendors had stopped supporting. Only enterprise machines with vPro were affected, but the bug prompted EFF’s demands for Intel to provide a way to disable ME.
There’s a company out there selling laptops with the ME disabled.
Since the beginning of 2017, Android phones have been collecting the addresses of nearby cellular towers—even when location services are disabled—and sending that data back to Google. The result is that Google, the unit of Alphabet behind Android, has access to data about individuals’ locations and their movements that go far beyond a reasonable consumer expectation of privacy
The cell tower addresses have been included in information sent to the system Google uses to manage push notifications and messages on Android phones for the past 11 months, according to a Google spokesperson.
Even devices that had been reset to factory default settings and apps, with location services disabled, were observed by Quartz sending nearby cell-tower addresses to Google. Devices with a cellular data or WiFi connection appear to send the data to Google each time they come within range of a new cell tower. When Android devices are connected to a WiFi network, they will send the tower addresses to Google even if they don’t have SIM cards installed.
why this is a really bad thing(tm) and shouldn’t go unpunished by the Register
This is more than a little embarrassing for a business that supplies handmade leather goods to the British royal family. Founded in 1880 by brothers Thomas, John and William Loake, the firm has since sold more than 50 million pairs of Goodyear welted shoes in more than 50 countries.
[…]
Loake strangely described described the attack as “similar in nature to that which was suffered by the NHS a few months ago” – presumably the WannaCrypt ransomware worm that held systems across the world hostage through encryption.
[…]
“The fact that they have likened their data breach to the recent NHS ransomware attack – two completely different events – reduces my confidence in their ability to deal with the situation and it also makes me question their reassurance that my credit card details are safe,” the customer added.
Etienne Greef, managing director of integrator Secure Data, told The Register it was “unlikely” that the breach was similar to the NHS attack as WannaCry does not access email servers, but rather encrypts information.
He said drawing comparisons with the NHS attack implied that Loake was running old, vulnerable versions of an operating system.
Loake Shoes admits: We’ve fallen victim to cybercrims – the Register
the individuals were able to download files containing a significant amount of other information, including:
The names and driver’s license numbers of around 600,000 drivers in the United States. Drivers can learn more here.
Some personal information of 57 million Uber users around the world, including the drivers described above. This information included names, email addresses and mobile phone numbers. Riders can learn more here.