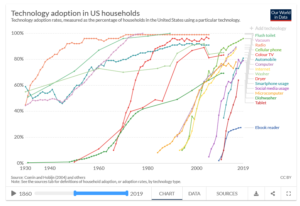
Facebook this week finally put into writing what users—especially
politically powerful users—have known for years: its community
“standards” do not, in fact, apply across the whole community. Speech
from politicians is officially exempt from the platform’s fact checking
and decency standards, the company has clarified, with a few exceptions.
Facebook communications VP Nick Clegg, himself a former member of the UK Parliament, outlined the policy in a speech and company blog post Tuesday.
Facebook has had a “newsworthiness exemption” to its content guidelines since 2016.
That policy was formalized in late October of that year amid a
contentious and chaotic US political season and three weeks before the
presidential election that would land Donald Trump the White House.
Facebook at the time was uncertain how to handle posts from the Trump campaign, The Wall Street Journal reported.
Sources told the paper that Facebook employees were sharply divided
over the candidate’s rhetoric about Muslim immigrants and his stated
desire for a Muslim travel ban,
which several felt were in violation of the service’s hate speech
standards. Eventually, the sources said, CEO Mark Zuckerberg weighed in
directly and said it would be inappropriate to intervene. Months later,
Facebook finally issued its policy.
“We’re going to begin allowing more items that people find
newsworthy, significant, or important to the public interest—even if
they might otherwise violate our standards,” Facebook wrote at the time.
Clegg’s update says that Facebook by default “will treat speech from politicians as newsworthy content that should, as a general rule, be seen and heard.” Nor will it be subject to fact-checking, as the company does not believe that it is appropriate for it to “referee political debates” or prevent a polician’s speech from both reaching its intended audience and “being subject to public debate and scrutiny.”
https://arstechnica.com/tech-policy/2019/09/facebook-confirms-its-standards-dont-apply-to-politicians/
YouTube CEO Susan Wojcicki said today that content by politicians
would stay up on the video-sharing website even if it violates the
company’s standards, echoing a position staked out by Facebook this
week.
“When you have a political officer that is making information that is
really important for their constituents to see, or for other global
leaders to see, that is content that we would leave up because we think
it’s important for other people to see,” Wojcicki told an audience at
The Atlantic Festival this morning.
Wojcicki said the news media is likely to cover controversial
content regardless of whether it’s taken down, giving context to
understand it. YouTube is owned by Google.
A YouTube spokesperson later told POLITICO that politicians are not
treated differently than other users and must abide by its community
guidelines. The company grants exemptions to some political speech if
the company considers it to be educational, documentary, scientific, or
artistic in nature.Morning Tech
Social media firms have seen their policies for reviewing and removing content come under fire in recent years, particularly when such content endorses hate-filled views or incites real-world violence. The issue is even more prickly when it involves world leaders like President Donald Trump, who has used bullying or violent language in social media posts.
But what constitutes a politician? Anyone in or running for office? What about public servants? County sherrifs? And who decides which of these groups are exempt? That’s the problem with exceptions, you get to make more and more exceptions until almost everyone is an exception.