A compendium of practical facts rendered useless.
Source: Stupid Calculations

Many smart home device makers rely on subscriptions to keep a steady stream of money coming in, but Wink is learning how that strategy can easily go wrong. The company has announced plans to move to a $5 per month subscription on May 13th (yes, just one week from now), and it’s mandatory. Decline to sign up and you’ll lose access to devices in the app as well as all automations. “Long term costs and recent economic events” (read: COVID-19) prompted the move, according to Wink, and the company didn’t want to sell user data to offset the costs of running services for free.
If you think that both the short notice and the threat of a hard cutoff will anger customers… well, you’re correct. Reddit users and others are incensed. They’re being asked to pay $5 per month to keep using the devices they already have in their homes, and one week gives them very little time to either weigh the merits of a subscription or find alternatives. “Pay the ransom or they kill our smart homes,” one user said.
We’ve asked Wink for comment. However it responds, the decision highlights the risks of basing your smart home system around free services without some kind of core offline functionality. While that kind of system can be very alluring so long as it lasts, you’re also trusting that the company can keep those free services running indefinitely. If it can’t, your connected household might be rendered useless with little warning.
Source: Wink smart home users have one week to subscribe or be shut off | Engadget
This new work represents a seamless, globally consistent, 1:5,000,000-scale geologic map derived from the six digitally renovated geologic maps (see Source Online Linkage below). The goal of this project was to create a digital resource for science research and analysis, future geologic mapping efforts, be it local-, regional-, or global-scale products, and as a resource for the educators and the public interested in lunar geology. Here we present the completed mapping project as unit contacts, geologic unit polygons, linear features, and unit and feature nomenclature annotation. The product overlies shaded-relief products derived from SELENE Kaguya terrain camera stereo (equatorial, ~60 m/pix) and LOLA altimetry (north and south polar, 100 m/pix). These data are not included with this download due to size considerations, but a readme in the “Lunar_Raster” folder provides the download links. This download page includes a PDF of the geologic map (right-side) with a brief Description of Map Units and Explanation of Map Symbols, as well as a JPG of the map for quick access viewing. This release is subject to update based on community feedback and peer-review.
Version 2 updates: Two errors were addressed in this update: (1) Large area polygons were offset from their contacts, likely due to user error. Polygons were rebuilt to fix the issue and post processing (dissolving, reattributing, etc.) to rectify the aesthetic of the map. (2) Contacts were not visible but should have been due to incorrect labeling as DND (do not draw). Those that needed to be drawn have been reattributed as “certain” those that are not drawn are labeled as “internal”. Additionally, in version 1 of this data, crater polygons with similar attributes had been dissolved and lumped into contiguous units. This has been changed so that all craters are now discrete units. This adds ~1000 units to the GeoUnits featureclass. There contacts are now visible and labeled as “certain”.
References:
Fortezzo, C.M., Spudis, P. D. and Harrel, S. L. (2020). Release of the Digital Unified Global Geologic Map of the Moon At 1:5,000,000- Scale. Paper presented at the 51st Lunar and Planetary Science Conference, Lunar and Planetary Institute, Houston, TX. https://www.hou.usra.edu/meetings/lpsc2020/pdf/2760.pdf
- Mimetype
- application/zip
- Filename
- Unified_Geologic_Map_of_the_Moon_GIS_v2.zip
- Publisher
- Astrogeology
- Publication Date
- 3 March 2020
- Author
- Corey M. Fortezzo (USGS), Paul D. Spudis (LPI), Shannon L. Harrel (SD Mines)
- Originator
- USGS Astrogeology Science Center
- Group
- PGM, MRCTR
- Added to Astropedia
- 19 December 2019
- Modified
- 24 April 2020
General
- Purpose
- The chief purpose of the 5M scale map is to summarize the current state of lunar geologic knowledge. Like terrestrial synoptic maps it provides a stratigraphic framework to be used for developing new theory and for determining the regional significance of surface exploration results. In addition to serving as a framework for interpreting surface exploration results, the effort to classify units into type and age by photogeology narrows the range of possible origins for many features.
- Geospatial Data Presentation Form
- Geologic Map
- Edition
- 2.0, March 3, 2020
- Native Data Set Environment
- ESRI Arcinfo
- Color
- Color
- Supplemental Information
- https://www.hou.usra.edu/meetings/lpsc2020/pdf/2760.pdf
Source: Unified Geologic Map of the Moon, 1:5M, 2020 | USGS Astrogeology Science Center
I was reticent to write this blog post because it leaves a lot of questions unanswered, questions that we should be able to answer. It’s about a data breach with almost 90GB of personal information in it across tens of millions of records – including mine. Here’s what I know:
Back in Feb, Dehashed reached out to me with a massive trove of data that had been left exposed on a major cloud provider via a publicly accessible Elasticsearch instance. It contained 103,150,616 rows in total, the first 30 of which look like this:
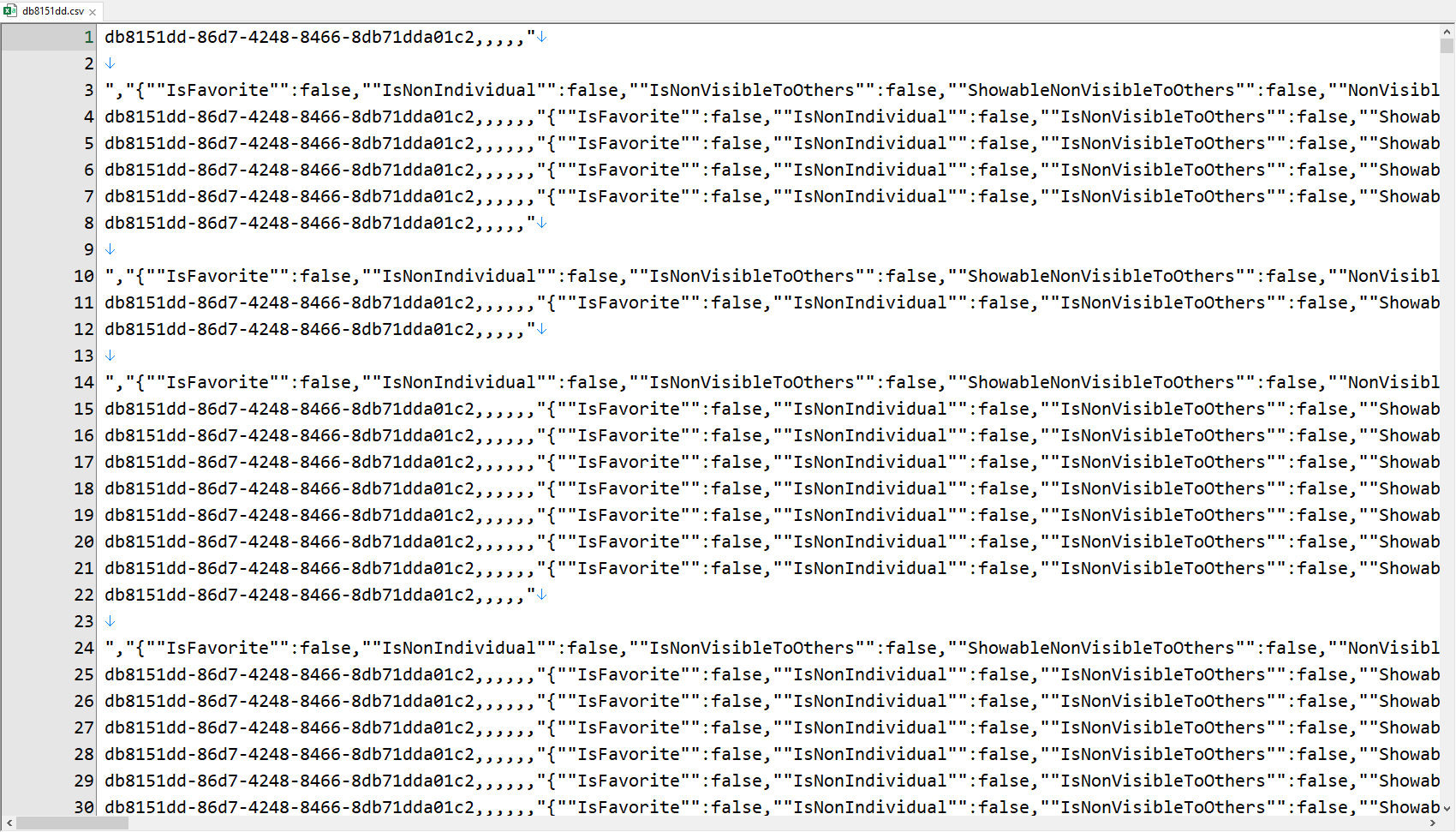
The global unique identifier beginning with “db8151dd” features heavily on these first lines hence the name I’ve given the breach. I’ve had to give it this name because frankly, I’ve absolutely no idea where it came from, nor does anyone else I’ve worked on with this.
It’s mostly scrapable data from public sources, albeit with some key differences. Firstly, my phone number is not usually exposed and that was in there in full. Yes, there are many places that (obviously) have it, but this isn’t a scrape from, say, a public LinkedIn page. Next, my record was immediately next to someone else I’ve interacted with in the past as though the data source understood the association. I found that highly unusual as it wasn’t someone I’d expect to see a strong association with and I couldn’t see any other similar folks. But it’s the next class of data in there which makes this particularly interesting and I’m just going to quote a few snippets here:
Recommended by Andie [redacted last name]. Arranged for carpenter apprentice Devon [redacted last name] to replace bathroom vanity top at [redacted street address], Vancouver, on 02 October 2007.
Met at the 6th National Pro Bono Conference in Ottawa in September 2016
Met on 15-17 October 2001 in Vancouver for the Luscar/Obed/Coal Valley arbitration.
It feels like a CRM. These are records of engagement the likes you’d capture in order to later call back to who had been met where and what they’d done. It wasn’t just simple day to day business interaction stuff either, there was also this:
But then there’s also a bunch of legal summaries, for example “CASE CLOSING SUMMARY ON USA V. [redacted]” and “10/3/11 detention hrg in court 20 min plus travel split with [redacted]”— Troy Hunt (@troyhunt) February 23, 2020
But nowhere – absolutely nowhere – was there any indication of where the data had originated from. The closest I could get to that at all was the occurrence of the following comments which appeared over and over again:
This contact information was synchronized from Exchange. If you want to change the contact information, please open OWA and make your changes there.
Exported from Microsoft Outlook (Do not delete)
Contact Created By Evercontact
Evercontact did actually reach out and we discussed the breach privately but it got us no closer to a source. I communicated with multiple infosec journalists (one of whose own personal data was also in the breach) and still, we got no closer. Over the last 3 months I kept coming back to this incident time and time again, looking at the data with fresh eyes and each time, coming up empty. And just before you ask, no, cloud providers won’t disclose which customer owns an asset but they will reach out to those with unsecured assets.
Today is the end of the road for this breach investigation and I’ve just loaded all 22,802,117 email addresses into Have I Been Pwned. Why load it at all? Because every single time I ask about whether I should add data from an unattributable source, the answer is an overwhelming “yes”:
If I have a MASSIVE spam list full of personal data being sold to spammers, should I load it into @haveibeenpwned?— Troy Hunt (@troyhunt) November 15, 2016
So, mark me down for another data breach of my own personal info. There’s nothing you nor I can do about it beyond being more conscious than ever about just how far our personal information spreads without our consent and indeed, without our knowledge. And, perhaps most alarmingly, this is far from the last time I’ll be writing a blog post like this.
Edit 1: No, I don’t load complete and individual records into HIBP, only email addresses. As such, only the presence of an address is searchable, the data associated with the address is not stored nor retrievable.
Edit 2: No, I can’t manually trawl through 100M+ records and extract yours out.
Edit 3: Thanks to some community sleuthing, the origin of this breach has now been identified as the Covve contacts app. Their public disclosure is in that link and they’ve also been in contact with regulators and had a couple of phone calls with myself.
A California state panel on Friday rejected a request from Elon Musk’s SpaceX for $655,500 in state job and training funds, citing the chief executive’s recent threats to move Tesla, the electric carmaker that he also runs, out of the state.
The snub comes as Musk has sparred with officials in Alameda County over his plans to resume production at the Tesla plant there, which was stopped because of the coronavirus.
Five members of California’s Employment Training Panel voted to reject the proposal and two voted for it, with one member absent, after discussing Musk’s tweets on Tesla’s reopening and media reports of layoffs at SpaceX’s Hawthorne, California headquarters in recent years.
“In my opinion, given the recent threats of the CEO to leave the state of California, and everything else we’ve discussed today, this proposal does not rise to the level for me to feel secure in supporting it,” said Gretchen Newsom, a panel member and the political director of an IBEW electrical workers union local.
“SpaceX is a different company, but they have the same CEO,” said Newsom, who is not related to California Governor Gavin Newsom.
Though a small amount of money, the funding was opposed by organized labor groups. Tesla and SpaceX are both nonunion shops.
Source: California officials reject subsidies for Musk’s SpaceX over Tesla spat – Reuters
A computer programmer applying for unemployment on Arkansas’s Pandemic Unemployment Assistance program discovered a vulnerability in the system that exposed the Social Security numbers, bank account and routing numbers and other sensitive information of some 30,000 applicants. Anyone with basic computer knowledge could have accessed personal information for malicious purposes.
Alarmed, the computer programmer called the Arkansas Division of Workforce Services Friday morning and was told by an operator that there was no one available who could talk to him. He then tried someone at the Arkansas State Police Criminal Investigation Division, who told the programmer he would find the person he needed to talk with to fix the situation. The programmer later called the Arkansas Times for advice on whom to call. The Times alerted the Division of Workforce Services to the issue at 4:30 p.m. Soon after a message appeared on the website that said, “The site is currently under maintenance.”
[…]
In exploring the website, the computer programmer determined that by simply removing part of the site’s URL, he could access the administrative portal of the site, where he had the option of editing the personal information of applicants, including bank account numbers. From the admin portal, he viewed the page’s source code and saw that the site was using an API (application programming interface) to connect with a database. That API was also left unencrypted, and he could access all of the applicants’ raw data, included Social Security numbers and banking information.
In about two minutes, the computer programmer described the vulnerability to another programmer the Arkansas Times engaged, who then used the information to easily enter the system. To access the sensitive information, the second programmer only needed to create an account, not actually apply for assistance.
Another person who applied for Pandemic Unemployment Assistance told the Times on Friday that when he applied for assistance, submitted his documentation and reached a “review” page, he saw the documentation for another applicant. He said it took three days for the state to remove the other applicant’s information. Then he said documentation for yet another applicant appeared. “It took two days and repeated phone calls to get the second name off,” he said. “Then the next day was when they erased it all and told us we had to reapply.”
Multiple supercomputers across Europe have been infected this week with cryptocurrency mining malware and have shut down to investigate the intrusions.
Security incidents have been reported in the UK, Germany, and Switzerland, while a similar intrusion is rumored to have also happened at a high-performance computing center located in Spain.
The first report of an attack came to light on Monday from the University of Edinburgh, which runs the ARCHER supercomputer. The organization reported “security exploitation on the ARCHER login nodes,” shut down the ARCHER system to investigate, and reset SSH passwords to prevent further intrusions.
The bwHPC, the organization that coordinates research projects across supercomputers in the state of Baden-Württemberg, Germany, also announced on Monday that five of its high-performance computing clusters had to be shut down due to similar “security incidents.” This included:
- The Hawk supercomputer at the High-Performance Computing Center Stuttgart (HLRS) at the University of Stuttgart
- The bwUniCluster 2.0 and ForHLR II clusters at the Karlsruhe Institute of Technology (KIT)
- The bwForCluster JUSTUS chemistry and quantum science supercomputer at the Ulm University
- The bwForCluster BinAC bioinformatics supercomputer at the Tübingen University
Reports continued on Wednesday when security researcher Felix von Leitner claimed in a blog post that a supercomputer housed in Barcelona, Spain, was also impacted by a security issue and had been shut down as a result.
More incidents surfaced the next day, on Thursday. The first one came from the Leibniz Computing Center (LRZ), an institute under the Bavarian Academy of Sciences, which said it was disconnected a computing cluster from the internet following a security breach.
The LRZ announcement was followed later in the day by another from the Julich Research Center in the town of Julich, Germany. Officials said they had to shut down the JURECA, JUDAC, and JUWELS supercomputers following an “IT security incident.” And so has the Technical University in Dresden, which announced they had to shut down their Taurus supercomputer as well.
New incidents also came to light today, on Saturday. German scientist Robert Helling published an analysis on the malware that infected a high-performance computing cluster at the Faculty of Physics at the Ludwig-Maximilians University in Munich, Germany.
The Swiss Center of Scientific Computations (CSCS) in Zurich, Switzerland also shut down external access to its supercomputer infrastructure following a “cyber-incident” and “until having restored a safe environment.”
Attackers gained access via compromise SSH logins
None of the organizations above published any details about the intrusions. However, earlier today, the Computer Security Incident Response Team (CSIRT) for the European Grid Infrastructure (EGI), a pan-European organization that coordinates research on supercomputers across Europe, has released malware samples and network compromise indicators from some of these incidents.
The malware samples were reviewed earlier today by Cado Security, a US-based cyber-security firm. The company said the attackers appear to have gained access to the supercomputer clusters via compromised SSH credentials.
The credentials appear to have been stolen from university members given access to the supercomputers to run computing jobs. The hijacked SSH logins belonged to universities in Canada, China, and Poland.
Chris Doman, Co-Founder of Cado Security, told ZDNet today that while there is no official evidence to confirm that all the intrusions have been carried out by the same group, evidence like similar malware file names and network indicators suggests this might be the same threat actor.
According to Doman’s analysis, once attackers gained access to a supercomputing node, they appear to have used an exploit for the CVE-2019-15666 vulnerability to gain root access and then deployed an application that mined the Monero (XMR) cryptocurrency.
[…]
Source: Supercomputers hacked across Europe to mine cryptocurrency | ZDNet
For those of us of a certain age, MTV defined culture. It was where we learned about not just music, but wider pop culture. Of course, MTV lost its cultural place atop the mountaintop with the rise of the internet, but that doesn’t mean that it wasn’t a key source of culture in the 1980s. Historically, the way that society preserves and remembers culture is to share it and spread it around. This is actually how culture is created. Yet copyright is the opposite of that. Copyright is about locking up content and denying the ability to create shared culture around it. And the best evidence of this is the fact that someone (it is not entirely clear who…) with the power to do so, demanded that the Internet Archive take down a bunch of old MTV videos that were uploaded.
So, The Internet Archive had someone upload a few hundred hours of MTV recordings. VJs, Commercials, and of course Music Videos, from the 1980s. Today, it was asked to be taken down by someone who could ask for that and it’s down. pic.twitter.com/tZ7Ka2sGMy
— Jason Scott (@textfiles) May 9, 2020
From a purely legal standpoint, it seems quite likely that whoever issued the takedown did have a legal leg to stand on. The real question, however, should be whether or not they have a moral or cultural leg to stand on. After all, if the entire point of copyright — as per the Constitution — is to encourage “the progress” then how does taking these old clips down do anything to support that goal?
There are a number of other points worth mentioning to demonstrate how crazy this whole thing is, starting with the fact that MTV itself knew how important it was to build on cultural touchstones in that its whole logo/image was built off a public domain image from just a few years earlier. The moon landing was in 1969, and MTV launched in 1981. Imagine if this image had been locked up under copyright?
MTV knows that creativity comes from building on the past; it created its most iconic moon landing imagery on top of public domain government videos and photographs. Another big company pulling up the ladder behind it https://t.co/9pamGhNAbb
— Parker Higgins (@xor) May 10, 2020
This also demonstrates a separate point we’ve been making for years, which is that the actual commercial value of a piece of work locked up behind copyright, tends not to be that long, and yet we locked it up for basically a century for no good reason at all. In the earliest copyright times in the US, copyright initially was for 14 years, which could be renewed for another 14 if the copyright holder felt it was worth it. A maximum of 28 years would mean that most of the uploaded clips would now be in the public domain if we had kept those terms. And, as we’ve pointed out repeatedly, back when copyright was 28 years, renewable for another 28 years, very few works were renewed, suggesting that the vast majority of copyright holders did not see any reason to retain their copyright beyond 28 years (indeed, the numbers suggest many would have been fine with significantly shorter copyright terms):
Yet, today copyright automatically lasts beyond most of our lifetimes. And, for what purpose? Right now, MTV is not particularly culturally relevant. You’d think that someone might jump at the chance to get renewed interest in MTV’s past cultural relevance, but the belief that copyright means we must lock up culture seems to prevail over common sense.
Taking down these cultural touchstones may have been perfectly legal, but all it’s really done is help demonstrate the many, many problems of today’s copyright law and how it destroys, rather than enhances, culture.
Source: Copyright Making Sure That MTV Remains An Irrelevant Relic, Rather Than A Cultural Icon | Techdirt
After it launched on Tuesday and nailed a series of maneuvers, China’s future crewed spacecraft has made a successful desert touchdown. Built by China’s main space contractor, the China Aerospace Science and Technology Corp. (CASC), the uncrewed prototype will ferry astronauts to China’s future space station and, eventually, the moon.
The crewed capsule (which doesn’t have a name yet), was lofted into an 5,000-mile-high orbit by China’s Long March 5B carrier rocket. During the mission, it underwent deep space trials similar to Orion’s 2014 mission, completing seven orbital adjustment maneuvers. Early this morning, the craft completed a deorbit burn, followed by separation of the crew and service modules. The three chutes deployed shortly after re-entry and it touched down in the Dongfeng desert area at 1:49 AM ET.
Designed to carry crews of up to six astronauts, the craft tested weighed 14 tons and is designed to be the primary transport to China’s future space station. CASC and the CNSA, China’s space agency, are also working on a 21.6-ton variant for deep space, designed to be used in future manned lunar missions. However, the CNSA has yet to nail down details for the larger craft and its moon missions are at least a decade away.
On top of doing orbital maneuvers, the prototype craft (with no life-support systems) conducted experiments on 3D printing of composite materials, high-definition image transmission and more. The mission was largely a success, apart from the malfunction of a cargo return capsule equipped with an inflatable heat shield.
Source: China’s next-generation crew spacecraft nails its test mission landing | Engadget
In designing electronic devices, scientists look for ways to manipulate and control three basic properties of electrons: their charge; their spin states, which give rise to magnetism; and the shapes of the fuzzy clouds they form around the nuclei of atoms, which are known as orbitals.
Until now, electron spins and orbitals were thought to go hand in hand in a class of materials that’s the cornerstone of modern information technology; you couldn’t quickly change one without changing the other. But a study at the Department of Energy’s SLAC National Accelerator Laboratory shows that a pulse of laser light can dramatically change the spin state of one important class of materials while leaving its orbital state intact.
The results suggest a new path for making a future generation of logic and memory devices based on “orbitronics,” said Lingjia Shen, a SLAC research associate and one of the lead researchers for the study.
“What we’re seeing in this system is the complete opposite of what people have seen in the past,” Shen said. “It raises the possibility that we could control a material’s spin and orbital states separately, and use variations in the shapes of orbitals as the 0s and 1s needed to make computations and store information in computer memories.”
The international research team, led by Joshua Turner, a SLAC staff scientist and investigator with the Stanford Institute for Materials and Energy Science (SIMES), reported their results this week in Physical Review B Rapid Communications.
[…]
Much as electron spin states are switched in spintronics, electron orbital states could be switched to provide a similar function. These orbitronic devices could, in theory, operate 10,000 faster than spintronic devices, Shen said.
Switching between two orbital states could be made possible by using short bursts of terahertz radiation, rather than the magnetic fields used today, he said: “Combining the two could achieve much better device performance for future applications.” The team is working on ways to do that.
Source: Scientists break the link between a quantum material’s spin and orbital states