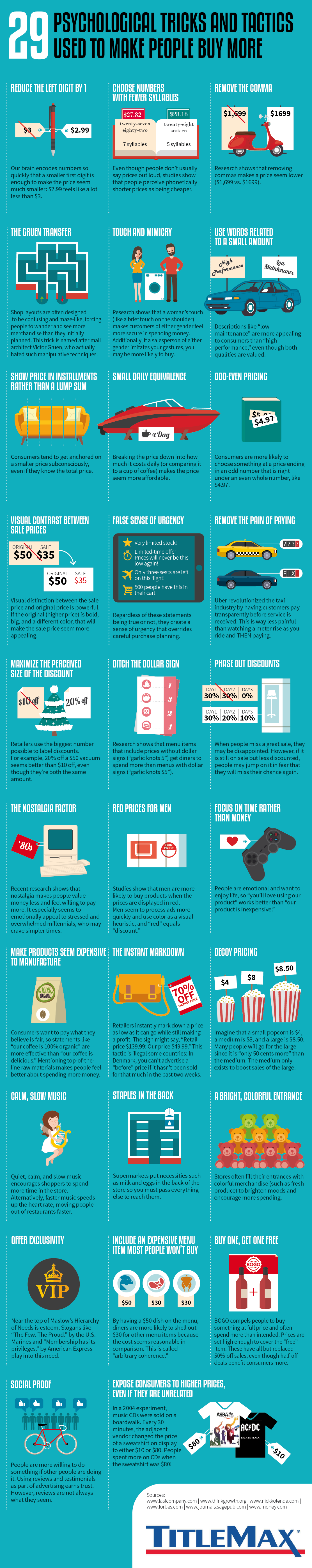
Microsoft has bagged exclusive rights to use OpenAI’s GPT-3 technology, allowing the Windows giant to embed the powerful text-generating machine-learning model into its own products.
“Today, I’m very excited to announce that Microsoft is teaming up with OpenAI to exclusively license GPT-3, allowing us to leverage its technical innovations to develop and deliver advanced AI solutions for our customers, as well as create new solutions that harness the amazing power of advanced natural language generation,” Microsoft CTO Kevin Scott said on Tuesday.
Right now, GPT-3 is only available to a few teams hand picked by OpenAI. The general-purpose text-in-text-out tool is accessible via an Azure-hosted API, and is being used by, for instance, Reddit to develop automated content moderation algorithms, and by academics investigating how the language model could be used to spread spam and misinformation at a scale so large it would be difficult to filter out.
GPT-3 won’t be available on Google Cloud, Amazon Web Services etc
Microsoft has been cosying up to OpenAI for a while; it last year pledged to invest $1bn in the San Francisco-based startup. As part of that deal, OpenAI got access to Microsoft’s cloud empire to run its experiments, and Microsoft was named its “preferred partner” for commercial products. Due to the exclusive license now brokered, GPT-3 won’t be available on rival cloud services, such as Google Cloud and Amazon Web Services.
[…]
GPT-3 is a massive model containing 175 billion parameters, and was trained on all manner of text scraped from the internet. It’s able to perform all sorts of tasks, including answering questions, translating languages, writing prose, performing simple arithmetic, and even attempting code generation. Although impressive, it remains to be seen if it can be utilized in products for the masses rather than being an object of curiosity.
Because everybody loves a monopolist