Have you immortalized your beloved dog, Charlie, in all of your online passwords? While he may be tasked to protect your home (or at least his food bowl), your heartfelt dedication might actually be compromising your digital safety.
Many passwords believed to be deeply personal to you are, in fact, quite common – making them easier to crack – and they could be putting you at an increased risk of being targeted by cybercriminals.
With this in mind, we’ve looked at the world’s most popular passwords in the last decade and found that millions of people worldwide are choosing the same passwords year after year.
Not only that, but there are common trends cropping up time and time again that are influencing the passwords we’re selecting – from your favorite pets and sports teams, to celebrities and movie titles.
Ready to take a look at the world’s worst passwords? Let’s dive in and find out why ‘Charlie’ might not be such a good boy after all.
Passwords: The Statistics

Although many of us know the dangers of weak passwords, it doesn’t stop us from choosing them. We rely on passwords to protect some of our most sensitive information, from dates of birth and addresses, to security codes, and credit card data.
Yet, still, we often opt for the same easy-to-guess passwords that cybercriminals can hack in a matter of seconds. Criminals use a variety of methods to hack our accounts, with one of the most popular being credential stuffing. Attackers find lists of compromised credentials – usually available from data leaks or purchased from the dark web – and combine stolen usernames and passwords together across hundreds of websites until they get access to your account. But usually, it’s not just one account.
The majority of us use the exact same password across several accounts to avoid the frustration of being locked out of accounts and having to remember longer, complicated passwords. But the risks associated with weak passwords cannot be ignored.
Password hacks are responsible for 81% of all data security breaches, making them the leading cause of compromised personal data. Reusing weak passwords gives hackers access to all of our apps and site logins in no time at all, leaving you vulnerable to fraud, identity theft, and other harmful cyber attacks.
We’re certainly not short of options to secure our passwords, either. There are plenty of password generators, managers, and other tools available to create unhackable passwords. Password managers, such as the CyberGhost Password Manager, even remember them for you, so you don’t have to.
Many websites also make stronger passwords a requirement, specifying the number of characters you should use, or that they should include a mixture of numbers, letters, and symbols. Some won’t even let you create an account if they think you’re using a fragile password.
So, what’s our excuse for making weak passwords to protect all of our personal or confidential information? Nothing, really.
The World’s Most Common Passwords in the Last Decade
Millions of passwords are hacked every year. And if we’ve learned anything from the lists of leaked passwords, it’s that they’re anything but unique.
Here’s a roundup of the world’s most common passwords over the last decade. If your password falls into these categories, it’s time to change it – and fast.
Number Sequences & Variations

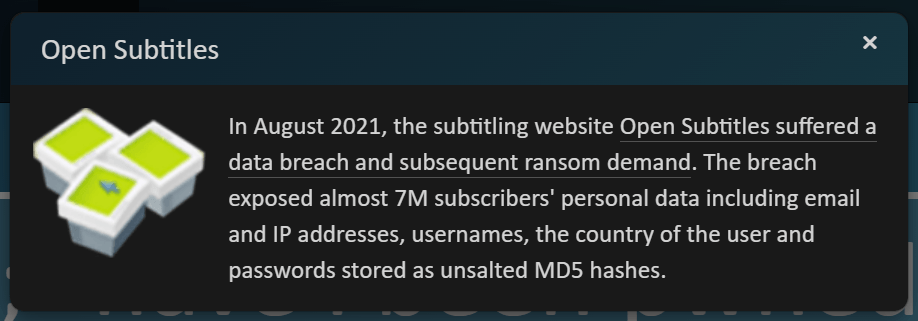
Passwords involving number sequences and variations have stayed high on the list of the most used passwords year after year. They’re also some of the most hacked passwords, because they’re incredibly easy to crack.
Rather than a completely random set of numbers, these passwords usually follow a sequence, either in numerical order, or a few numbers repeated several times. Some users add letters and other characters to try to make these passwords more complicated, but again, these follow an easy-to-guess sequence.
The most common password is ‘123456’. It is actually the most used and compromised password in the world, occurring in 23.2 million cyber breaches in 2019.
Many use their dates of birth, which, while more unique, are still very weak. It doesn’t take long for a cybercriminal to figure out your birthday – usually a quick scroll of your social media profile will give them all they need. Birthdays can also be easily sequenced and decoded, since databases holding this information are readily available to anyone.
Hackers also often use algorithms to crack passwords, whereby computers guess simple numerical sequences at rapid speed. In a mere few seconds, a cybercriminal has access to your account. Essentially, you’re fighting against computer processing powers – and you’ll never win.
The Password

Ironically, millions of people worldwide choose the word ‘password’ as their password.
As it were, ‘password’ has actually remained in first or second place consistently for years, though recently more of us have been using variations that we think are more tricky to decode by adding numbers or switching out letters for numbers, including ‘password1’ or ‘passw0rd’.
We’ve even seen foreign variations of ‘password’ hitting the list, with ‘senha’ being a popular choice. For those of you wondering, ‘senha’ is Portuguese for ‘password’.
In 2019, ‘password’ was one of the most widely used passwords across breached accounts, occurring in 3.6 million breaches.
Other translations for password aren’t as popular though, especially those with special characters, perhaps because they’re harder to type in.
That said, if you’re tempted to use a foreign variation of ‘password’, it’s best not to. It doesn’t take long for a cybercriminal to work their way through the many different global languages before they get access to your account.
Keyboard Patterns

Keyboard patterns have long been popular passwords, with ‘qwerty’ ranking highly in all lists over the last 10 years. But many of us have tried to get more creative in recent years, adding in diagonal and backwards variations, numbers, and more characters.
Being creative with keyboard patterns doesn’t necessarily make them stronger, though. ‘qwerty’ is one of the most hacked passwords in the world, actually ranking higher than ‘password’ itself.
In 2019, ‘qwerty’ was involved in 4 million cybersecurity breaches.
Variations of ‘qwerty’ have gradually grown in popularity, probably as a result of many people realizing just how popular (and hackable) the word is on its own. Adding a few numbers onto the end or changing the pattern backwards is still a recipe for disaster.
Movies & TV Shows

Movies and TV shows are a very popular category when it comes to passwords. We’ve seen movie titles and series names pop up regularly over the last decade, with some of them shared by millions of us around the world.
While it can be tempting to set your all-time favorite movie and TV series as your password, doing so makes you vulnerable to hackers – especially if it’s very well-known or it’s premiered recently.
In 2014, ‘starwars’ made the list of popular passwords, coinciding with the long-anticipated release of Star Wars: The Force Awakens. Since then, it’s stayed high in the list, making us question how often people are actually changing their passwords once they’ve chosen them. Even the password ‘yoda’ has been hacked over 37,000 times.
The password ‘ninja’ also ranked highly back in 2012. That same year, the reboot of the highly popular kids TV show, Teenage Ninja Turtles, hit our screens. It seems there’s a pattern developing here, doesn’t it?
If you’re a lover of Pokémon and James Bond, think again before you set either of these as your password. Both ‘pokemon’ and ‘bond007’ are widely used. Hackers will try alphanumeric variations, too, including ‘p0kemon’, so even switching out a couple of characters doesn’t mean you’re safe.
Names

Unsurprisingly, names top the list of most popular passwords year after year.
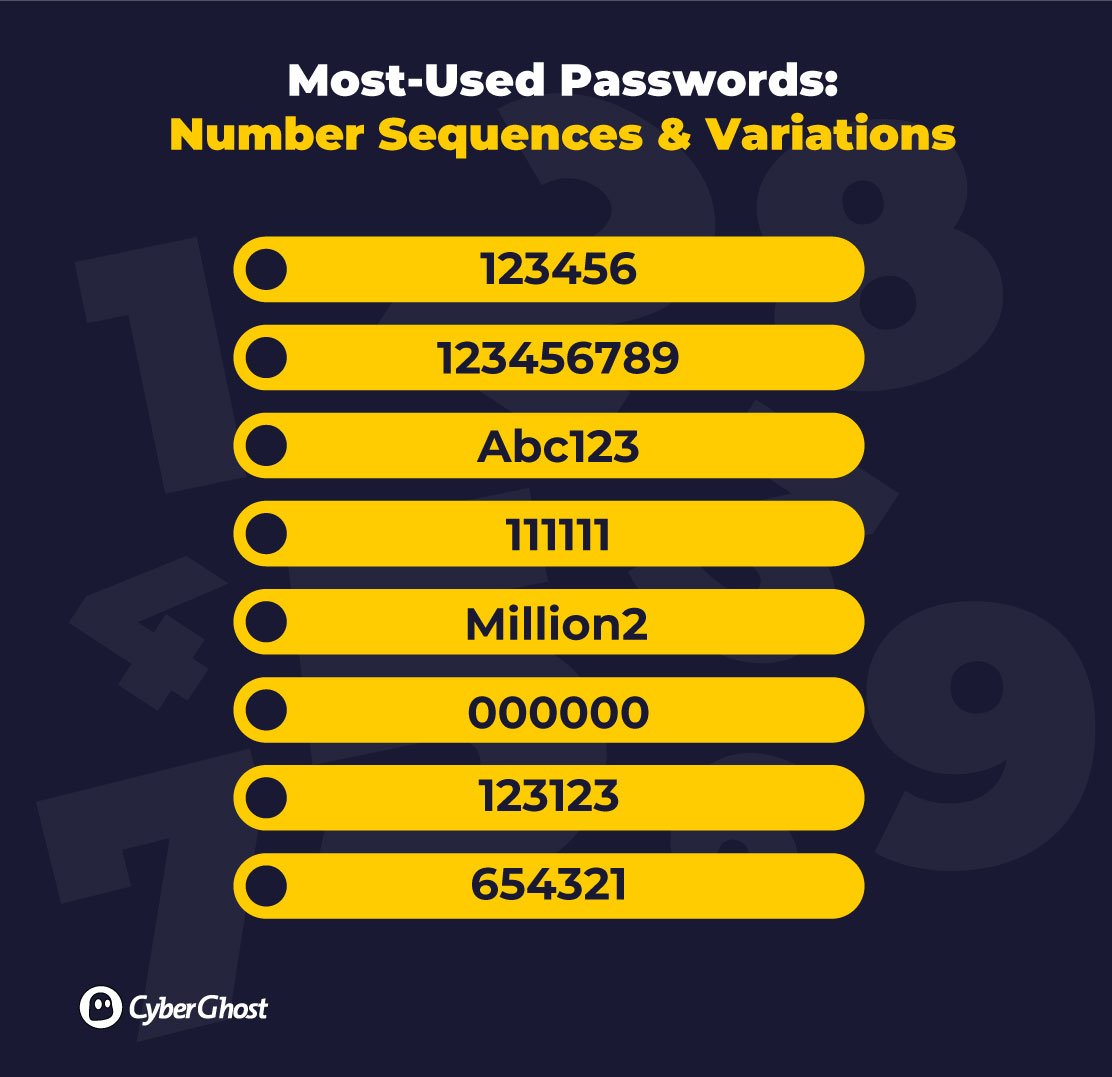
If your name features on the list of the world’s most popular names, avoid using it as your password at all costs. ‘Michael’ for example, ranks at spot 18 of the world’s most popular names, and has consistently made it to the top 20 most used passwords.
Other common names also follow the same pattern. Some to avoid include ‘Ashley’, ‘Jessica’, ‘Jennifer’, ‘Thomas’, and ‘Daniel’. But, honestly, even those with more obscure names aren’t safe. Remember, it only takes a cybercriminal a few minutes to find your details and enter your name with your email to log in to one of your accounts.
It’s not just your first names you need to worry about, either. You’ll definitely remember the name of your child as your password, but it leaves you and your information vulnerable.
Trends show that the most popular baby names each year coincide with common passwords. ‘Maverick’, for example, reached spot 39 of the world’s most popular baby names in 2021. And it’s since become an in-demand password choice.
Animals & Pets

Animals are a consistent hot topic for passwords, although not necessarily the popular, domestic animals you’d expect.
Likely, many of the domesticated animals including cats and dogs aren’t long enough to meet character requirements for passwords. But also, perhaps many of us are trying to think out of the box and choose animals that are tougher to guess. We aren’t succeeding, though.
Both ‘dragon’ and ‘monkey’ have ranked consistently high in the last decade. While we don’t know the real reasons people choose these words, we do know that people tend to create passwords based on things they like.
Dragons in particular have weaved their way into our culture many times, from Game of Thrones to Dungeons & Dragons, so is it any wonder millions of us are choosing this mythical creature to lock our accounts?
Another likely influence is astrology. Both ‘monkey’ and ‘dragon’ are animals in the Chinese or lunar zodiac, and could be representative of a large population in Asian countries (and elsewhere) choosing these animals for their passwords. ‘tiger’ and ‘rabbit’ also made the lists – another two of the twelve Chinese zodiacs.
Popular pet names are also a common theme. We compared names we found with the world’s most popular pet names list, and found a direct link. If your favorite childhood pet was named ‘Bailey’, ‘Buster, or the beloved ‘Charlie’, it’s time to change your password. In fact, just steer clear of choosing a password that includes your pet’s name full stop.
Sports & Team Names

Choosing your favorite sport or team as your password makes it easy to remember, but also easily guessable.
Sports and team names have been consistently used as passwords for many years. In fact, sports is one of the most common themes for passwords, of all the categories we identified.
In particular, ‘football’, ‘soccer’, ‘golf’, ‘hockey’, ‘baseball’, and ‘basketball’ are some of the most frequently used passwords. ‘football’ has long been a top choice of password, ranking in the top 10 for the last decade. It’s only in more recent years that we’ve seen new sports contenders moving up the list.
We can also see trends in actual team names, especially across popular US sports, including American football and basketball. ‘Lakers’, ‘Eagles’, ‘Yankees’, and ‘Cowboys’ all made it into the list of the most popular passwords.
‘Liverpool’ topped the league of most guessable passwords, accounting for 280,723 cyber breaches.
In the UK, recent statistics show a similar trend with football (soccer) teams. Passwords using the words Liverpool, Chelsea, Arsenal, ManUtd, and Everton were all involved in a significant number of cyber breaches in 2019.
Cars & Vehicles

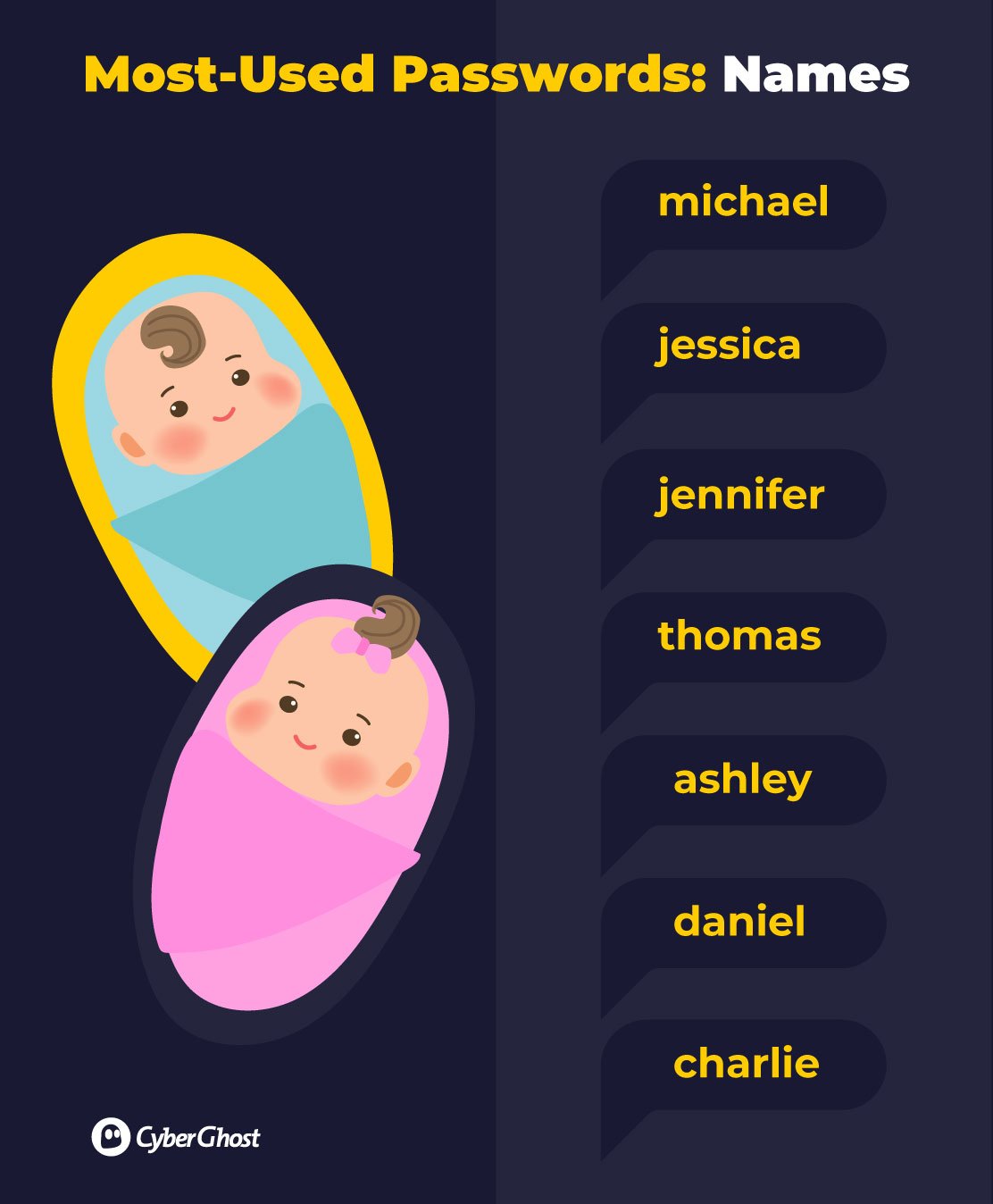
In the last decade, car models in particular have ranked highly in the world’s most used passwords.
Some of the most frequently used include ‘mercedes’, ‘ferrari’, ‘corvette’, ‘porsche’, and ‘mustang’.
‘Mustang’ moved up the list in 2014 coinciding with the release of the 50th year limited edition model. Interestingly, the Ford Mustang was also featured in Fast & Furious 6, which was released the year prior in 2013, likely influencing people’s preference for this password.
Similarly, the Corvette was used in the Transformers: Age of Extinction (2014) movie, as well as Gran Turismo 6, a popular video game released in December 2013. While both cars are popular regardless, clearly car-driven movies are a driving force for password decisions.
It’s not just cars to watch out for, either. ‘harley’ features as a widely used password, probably after the famous Harley Davidson motorcycles.
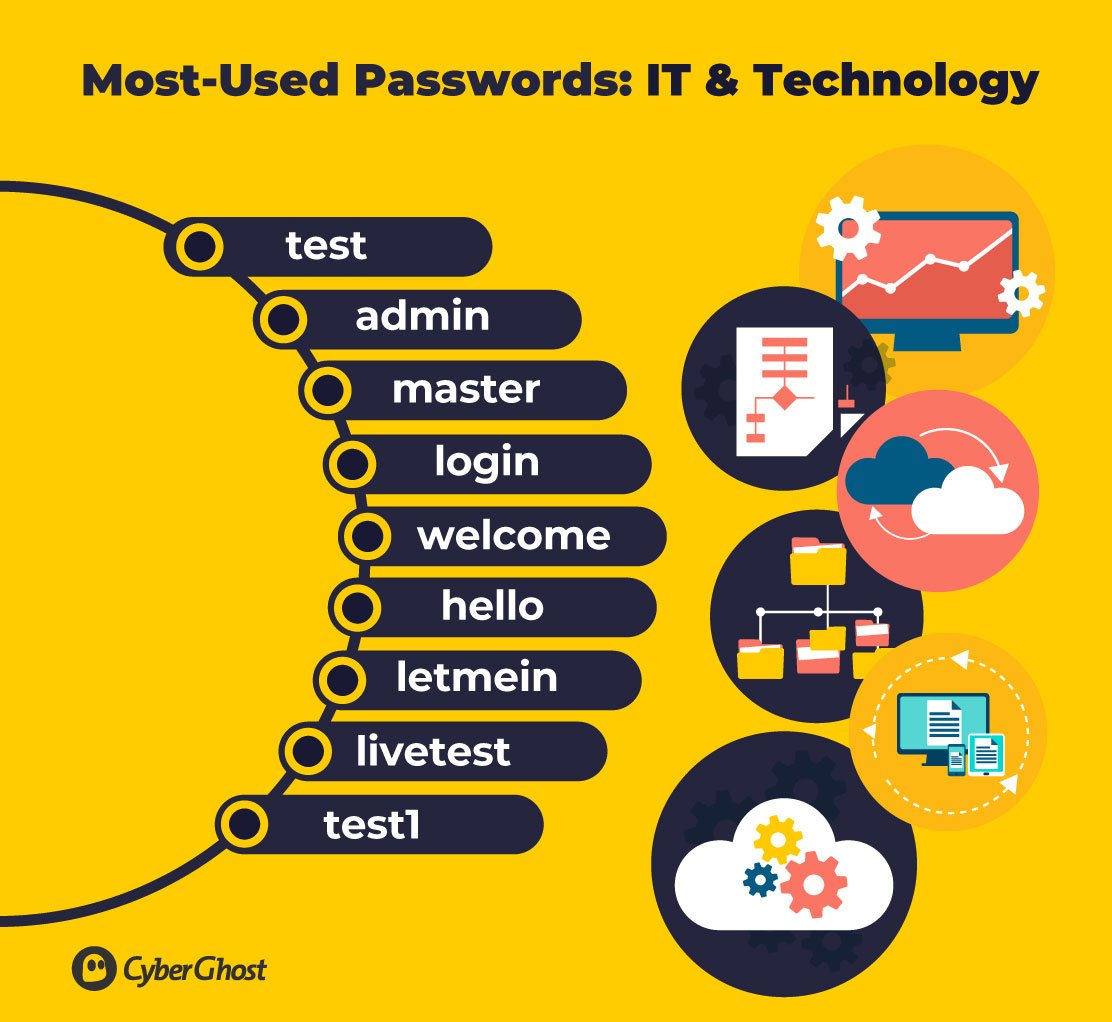
IT & Technology

The constant evolution of technology coincides quite naturally with the rise in tech-related passwords. This is likely linked to the ever-growing necessity for testing by IT departments.
In the last 10 years, we’ve seen a high number of dummy accounts created by developers to test applications and websites. Passwords such as ‘test’, ‘admin’, ‘master’, and ‘login’, have all become more common since 2019, including the many different variations swapping out letters for numbers and adding in symbols.
More often than not, IT departments reuse the same default passwords to test accounts. But this is putting organizations at risk, with many falling victim to botnet attacks as a result of weak, hackable passwords.
Cybercriminals use repetitive, password-guessing tech to break through systems and compromise company devices by guessing combinations of passwords. Weak passwords such as ‘test1’, ‘welcome’, and ‘letmein’ are easily guessable, and only take bots a matter of seconds to correctly decode.
The technology industry is set to explode even more in the next 3 years, with a forecasted growth rate of 104% in emerging tech. Based on recent trends, it’s likely we can expect many more passwords linked to testing and admin in the future.
Applications, Games & Sites

Applications, games, and websites consistently show up in the lists of popular passwords. Worryingly, however, many people are probably choosing a password correlating to the site they’re using, such as ‘google’ to access Gmail accounts and Google Drive, making them some of the worst possible passwords to use.
Both ‘Adobe’ and ‘Photoshop’ were incredibly popular between 2011-2013, as well as variations of these words, but they have since dropped off lists in favor of new, mainstream apps. That doesn’t mean they’re safe to use though – these passwords are easy to guess and hack.
Video-editing apps have grown in popularity with ‘dubsmash’ and ‘animoto’ appearing on lists since 2019. Most probably, this is due to the rise of TikTok with more of us creating videos to post on the platform.
In 2020, ‘evite’ climbed up the rankings, likely as a result of the data breach it experienced in 2019 which compromised data from over 100 million accounts. Again, this is further evidence that users were simply using the name of the platform as their passwords for their accounts.
Characters & Celebrities

We’re constantly seeing celebrities and characters pop up in the news, online, and on our TV screens, so it’s no wonder, really, that famous people also find their way into our passwords.
Superheroes are an especially popular choice for passwords, with ‘superman’ and ‘batman’ being used by millions worldwide every year since 2011. But another key trend we’ve seen is fictional characters, especially those from children’s movies and TV shows. ‘tigger’, ‘snoopy’, and ‘scooby’ are all used frequently year after year.
Even the name ‘Justin’ hit the list of most used passwords in 2020, possibly linked to the well-known singer Justin Bieber who released a number one album that year. Similarly, ‘Donald’ (probably after Donald Trump) shot up the list in 2018 during his time as president.
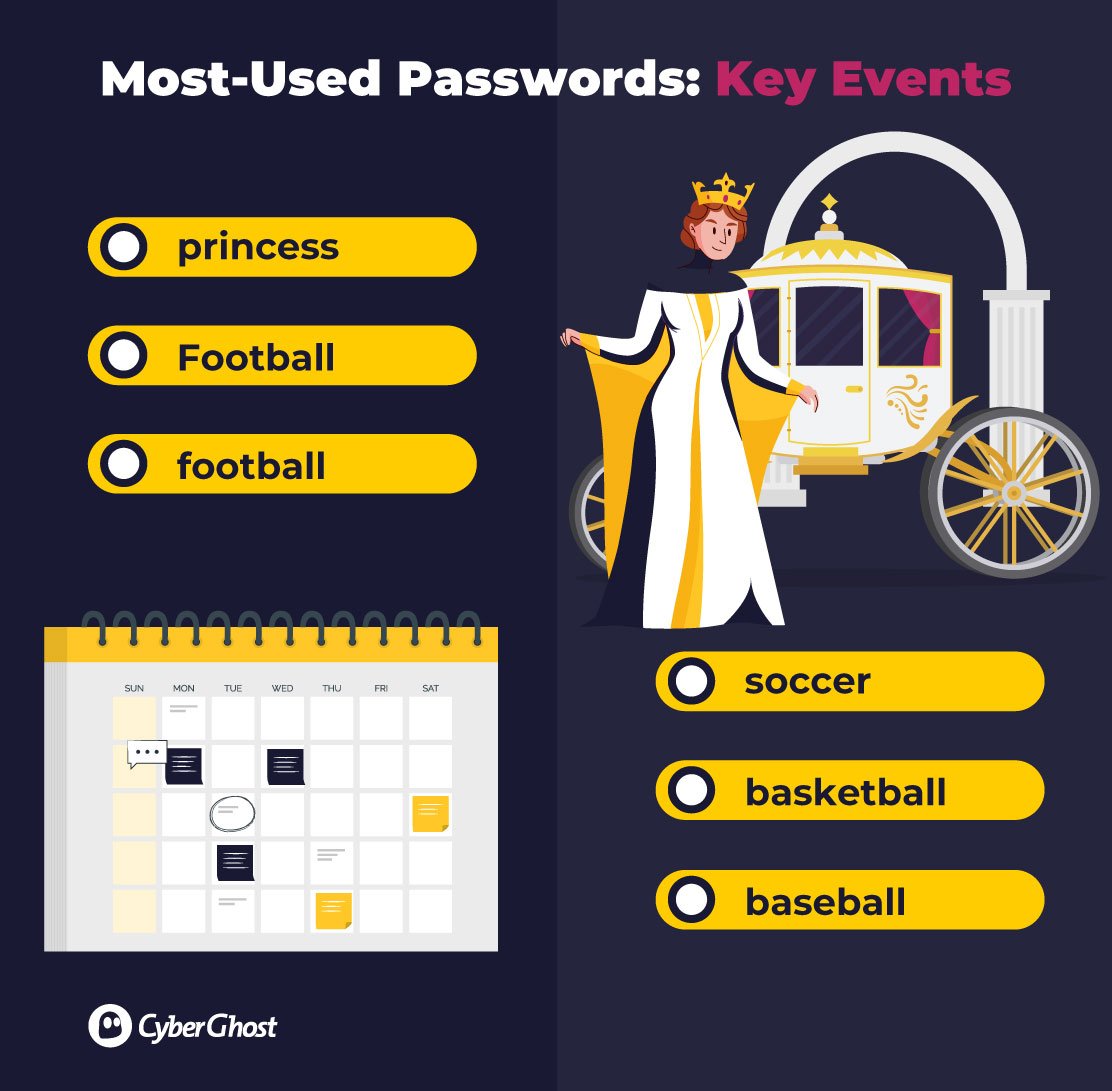
Key Events

Key global events play a key part in password choices, showing that clearly, whatever is at the forefront of our minds is influencing the words that end up protecting our accounts.
In 2011, ‘princess’ became one of the most popular passwords. Incidentally, this coincides with the Royal Wedding of Prince William and Princess Kate, which was watched by more than 160 million viewers around the globe.
We can see similar trends in more recent years.
In 2016, ‘football’ climbed up rankings as one of the most chosen passwords. That same year, football experienced some of the most memorable sports moments to date, including the Euros in France, the summer Olympics in Rio (where Brazil won gold in football), and Leicester City winning the UK Premier League against all odds.
Fast forward to 2020, and the same trend remerged. ‘Soccer’ hit the list of most popular passwords, following the 2020 Euros and Champions League Final, perhaps relating to an increase in audiences tuning in from the US and Australia where ‘soccer’ is more often used to refer to football.
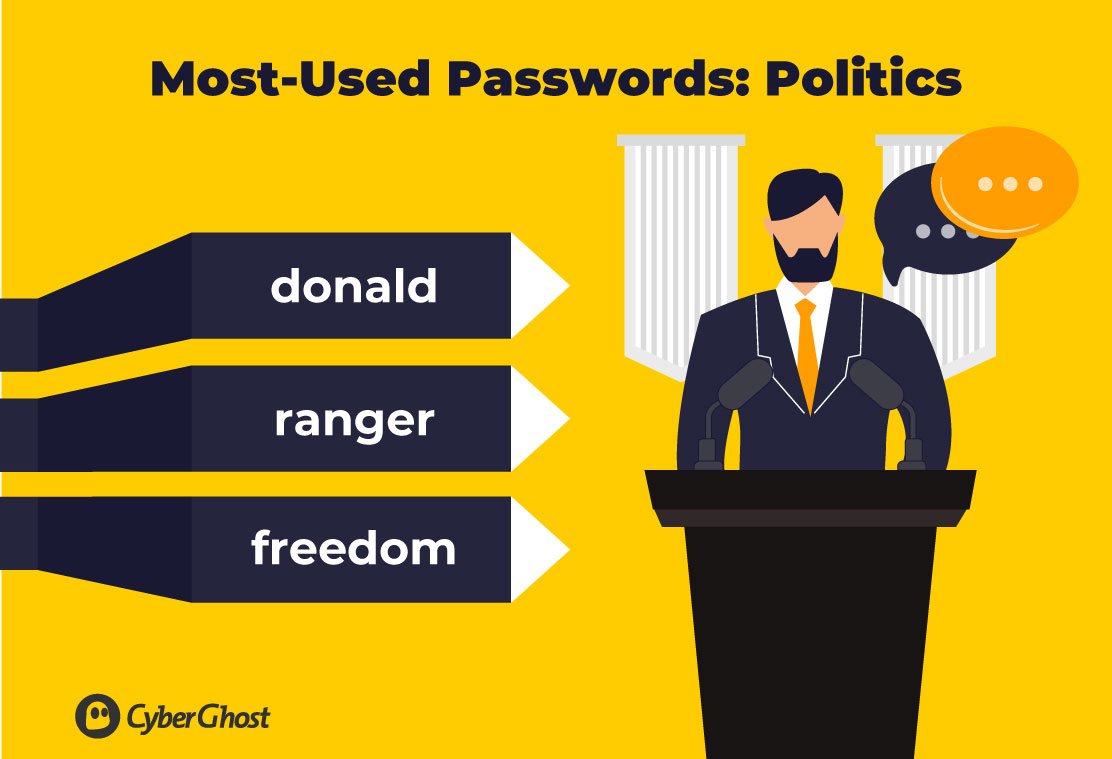
Politics

The political climate is one that’s certainly been turbulent in recent years, with many unprecedented political events around the world and rising conflict. And the world’s most popular password lists reflect that, too.
In 2018, ‘donald’ became one of the most widely used passwords, after Donald Trump’s election as president of the United States in 2017.
Interestingly, we also saw ‘freedom’ become a top password choice in the same year, coinciding with the drastic change in the political climate influenced by Donald Trump.
In 2017, ‘ranger’ also hit the most-used password lists, following the globally shared story of a park ranger’s facial expressions in response to Donald Trump’s salary donation.
The politics category is perhaps not as saturated as others when it comes to passwords, but it clearly shows how the global climate is influencing our password decisions. If we’ve learned anything so far, it’s not to use any president’s or prime minister’s name as your password.
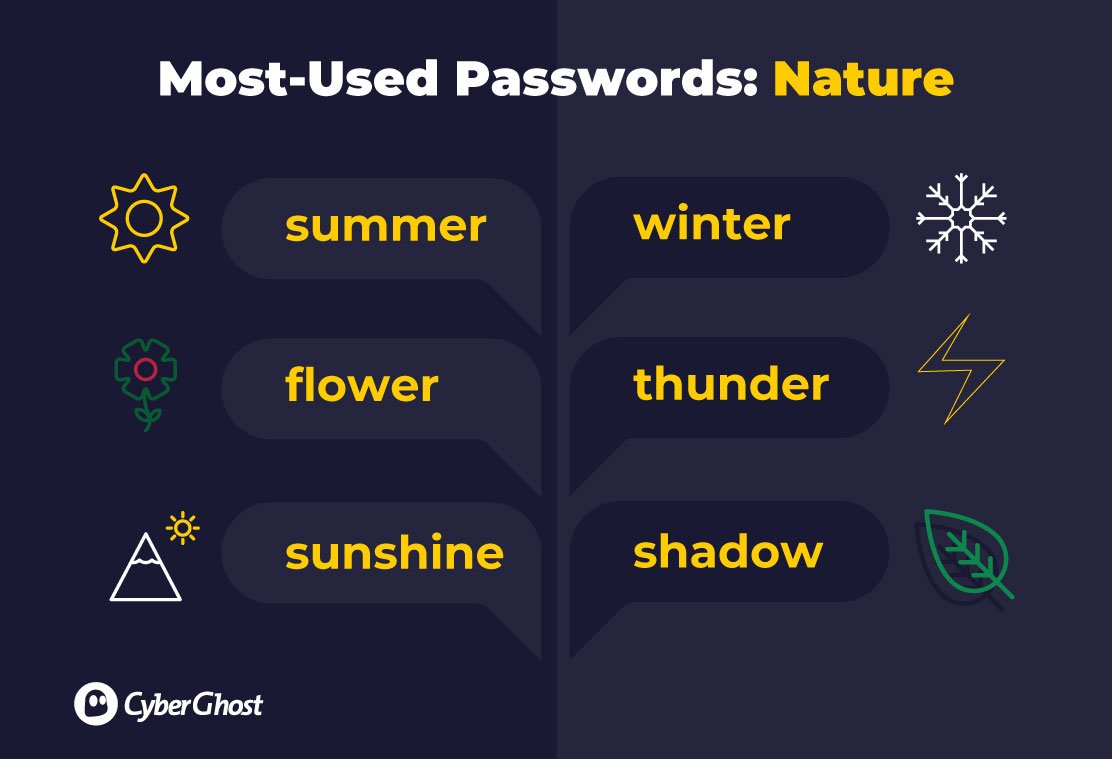
Nature

A common – perhaps expected – theme for passwords over the last decade is nature, including plants, seasons, and even actual weather.
Some of the most-used passwords include ‘summer’, ‘flower’, ‘sunshine’, and ‘winter’, which have made lists year after year. But we’ve even seen ‘thunder’ being used, albeit lower down in the lists.
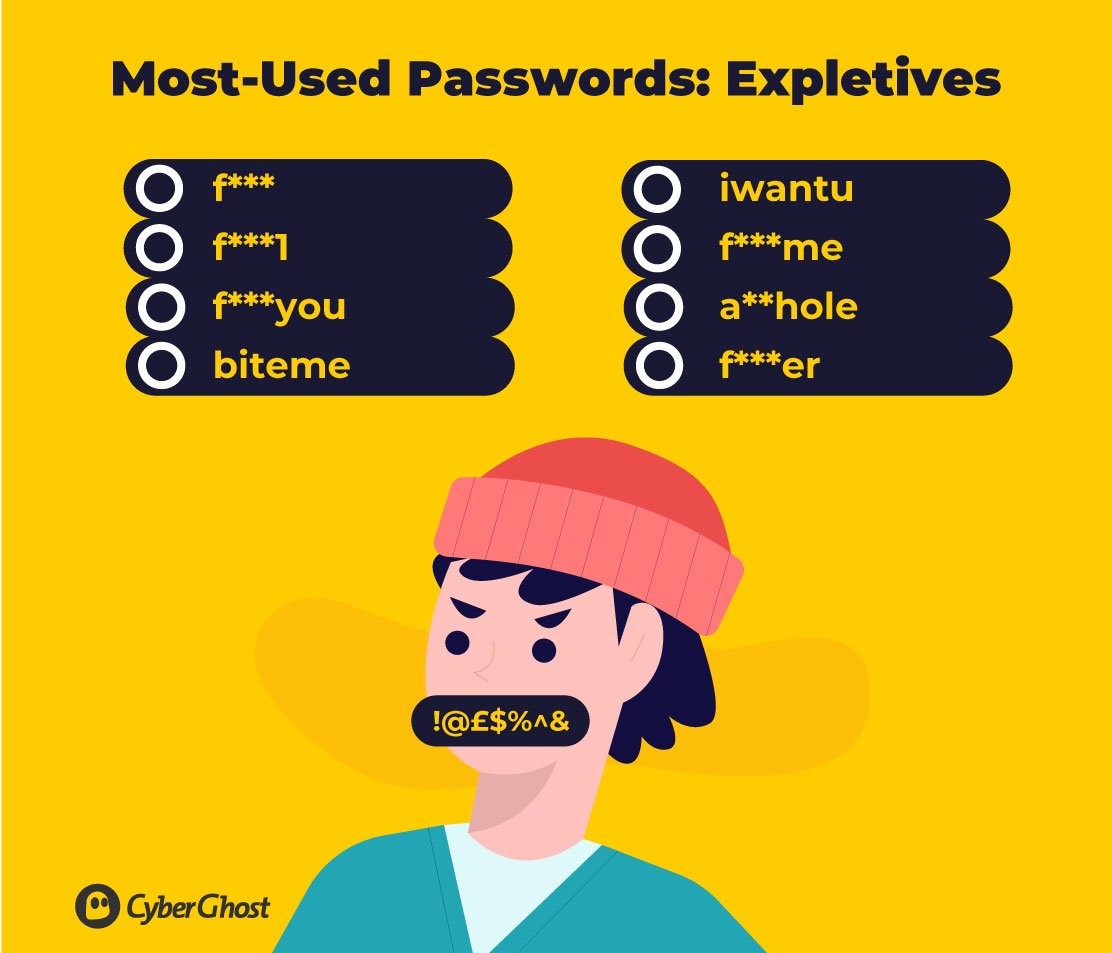
Expletives

Surprisingly, millions of people around the world choose to use expletives as passwords to protect their accounts and confidential information.
Many of the expletives chosen center around the ‘f’ word and variations, including the word with added numbers and other characters, such as ‘f**k1’. Many, however, are related to sexual expletives which we won’t go into detail here.
Some are less offensive, with ‘biteme’ being a common choice of password, as well as ‘iwantu’.
Interestingly, the number of expletives as passwords has gradually increased in the last decade, perhaps because swearing is generally on the rise around the world, too. The number of expletives used in American literature has soared in the last 60 years. In comparison to the 1950s, books published in the modern day are 28 times more likely to include swear words.
According to a BBFC survey, a third of people say they use offensive language more frequently than they did five years ago. Those that fall into the Generation Z category (born after 1996) are the most frequent culprits, 46% of people said they use strong language.
With expletives finding their way into our daily conversations more often, it comes as no surprise, then, that they’re some of our top choices for passwords.
Miscellaneous Categories

A number of passwords can be miscellaneously grouped into common trends over the years. In particular, colors, food, and locations are common choices for passwords.
In the food category, we’ve seen words such as ‘chocolate’, ‘cheese’, ‘butter’, and ‘cookies’ pop up very frequently. Considering the dramatic increase in health and lifestyle resources in recent years (from apps to social media influencers), it’s perhaps reassuring to see that people struggle to choose healthy foods even when setting passwords.
Some of the most common color-related passwords include ‘purple’, ‘blue’, and ‘orange’. Location-wise, it seems US cities and states are most frequently used, with ‘Dallas’, ‘Phoenix’, and ‘Dakota’ all making the top lists – though this may also indicate how often US accounts are targeted by hackers.
Another common theme over the last decade is words relating to love, and in particular ‘iloveyou’. More recently, people have used foreign variations on this three-word phrase, including the Vietnamese translation ‘anh yeu em’ (without spaces, of course).
The Future of Passwords (And Which Ones Not to Use)
Based on the trends we’ve seen over the previous decade, we have a good idea of what passwords people will be using in future and, certainly, which themes will be influencing our security decisions.
The Non-Movers
The usual culprits have made the top 10-20 most popular password lists for 10 years (and more), so there’s no doubt we’ll still be seeing them for years to come.
Numerical sequences, keyboard patterns, and variations of ‘password’ will be around for a long while yet, even with us knowing how hackable these passwords are.
So, if any of your passwords still involve ‘123456’, ‘qwerty’, or ‘passw0rd’, change them immediately.
Rising Names
The world’s most popular names are directly linked to the most-used passwords. In fact, names make up a large majority of the world’s most popular passwords, so we can say with certainty that they’re going nowhere.
New, upcoming baby names are also something to watch out for, as well as the usual contenders. Some of the most common baby names for the next year include Zion, Maeve, Kai, Luca, Mia, and Nova. There’s no doubt cybercriminals will be trying these names to access your accounts, so keep them locked out with a better password.
Pet names are likely to have an influence, too. Steer away from this year’s top dog names, including Bella, Luna, Lola, Max, Alfie, and – you guessed it – Charlie.
Applications & Websites
Based on recents trends, we may possibly see more passwords relating to apps rising in popularity, including Discord, Twitch, Headspace, and Duolingo.
Streaming sites may also find their way into our password choices, especially new contenders with a rapidly growing customer base. ‘Paramount+’ (launched in 2021) and ‘Disney+’ (from 2019) are both names you should avoid in your passwords.
In all honesty, though, even the less popular apps and websites aren’t safe. Cybercriminals can easily use bot attacks to try heaps of different apps and websites names and get access to your accounts.
Movies & TV Shows
Trends over the last decade show that we’re consistently choosing names of popular movies and TV shows, especially ones that are current, eagerly anticipated, or have been released that year.
2022 is set to be a huge year for the film industry, seeing the release of some of the biggest films to date. For that reason, avoid choosing words such as ‘Avatar’, ‘Mission Impossible’ ‘Spiderman’, ‘Jurassic’, and ‘Thor’.
Another trend we’ve noticed is that family-friendly films are a consistent thread. Perhaps parents are trying to set up accounts for their children or install parental controls, and choosing family films or TV shows as easy-to-remember passwords. But if we’ve learned anything so far, it’s that simple password solutions are often the worst.
Key Events
As well as a big year of movies, 2022 will be home to large sporting events. Sports in particular have been a driving force for passwords, from team names and sport types, to key events. So, we know this is something to watch out for.
Some of the biggest events happening next year include the Beijing 2022 Winter Olympics (February), Super Bowl (February), Commonwealth Games (July), MLB All-Star Game (July), and the FIFA World Cup (November). Any password relating to these major events, even if you think it’s unique, should be avoided at all costs.
Presidential elections are also likely to have an influence on password choices, as the ever-changing political climate takes hold.
In particular, Brazil is holding elections during 2022, so as tempting as ‘Bolsonaro’ may be as a new password for your accounts, don’t do it. The US is also holding mid-term elections, which will be a hot topic of debate and most probably a key driver for politically driven password inspiration in 2022.
Top Tips For Unhackable Passwords
Creating a password that’s strong enough to protect your accounts and easy enough for you to remember can feel like a tricky task. But strong passwords really are important for keeping your private information secure and fighting off hackers.
Here are some top tips for creating unhackable passwords.
-
- Keep passwords long: All passwords should be at least 12 characters long – the longer the password, the tougher it is to crack.
- Choose unique words: Avoid picking words that are easy to guess (such as those that fall into all of the categories we’ve identified). And don’t choose words or numbers easily linked to you, such as your date of birth, address, or nickname.
- Use a mixture of characters, letters, and symbols: Passwords that use a mixture of characters, letters, and symbols are harder to guess. You should also use a combination of upper and lowercase letters. Don’t just add ‘123’ to the end of a word, as that’s just as easy to guess as the word itself.
- Create new passwords for different accounts: Don’t use the same password across each account. If a hacker manages to guess the password, they get access to everything, rather than just the one account. To make passwords easier to remember, you could choose a similar word but add something unique to it, such as new numbers or symbols.
- Switch it up: Make sure you regularly change your passwords to minimize the risk of your accounts being compromised. Aim for at least every 3 months, and don’t recycle old passwords.
Human-generated passwords tend to have commonalities, so it’s always safer to opt for a password generator. This generates passwords for you based on a random sequence of letters, numbers, and symbols, which are (nearly) impossible to crack and completely unique.
Without a password manager, these random passwords can be difficult to remember though. Ideally, you should opt for a password manager that can be downloaded as an app or in your browser, such as the CyberGhost Password Manager. This automatically stores passwords for you in an encrypted vault and enters them as needed to log in to your accounts, even across different devices.
Another thing to consider is using a VPN to add another layer of protection while you’re browsing the web.
Even if a hacker can’t guess your password, they may be able to intercept your web traffic and get access to your device. This is especially risky on public Wi-Fi networks, which can be unsecured and rife with hackers looking for opportunities to harvest your credentials.
With access to your device, hackers can easily find your stored passwords, steal your information, and subject you to several cybersecurity threats. However, a VPN encrypts all of your web traffic, adding a layer of security to help prevent cybercriminals from finding you online or hacking your device.
You can add yet more security by using multi-factor authentication. This means that any cybercriminal trying to access your account will also have to enter a second piece of information alongside your password, such as a one-time code sent to your cell phone or an answer to a secret question.
Beyond password managers and two-factor authentication, you should still be taking steps to secure your passwords.
The Bottom Line: Strengthen Your Passwords to Strengthen Your Privacy
Stronger passwords might mean it takes you a few seconds longer to log in to your account, but it’s worth it to protect your information and to keep cybercriminals away.
You might just save yourself from a risky data breach exposing your confidential information. After all, identity theft and fraud are very much real. Data breaches are increasing around the world and hackers are finding new, clever ways to harvest our credentials. We really can’t afford to be lazy with our passwords.
So, even if your dog, Charlie, is your one and only, the reality is his name is being used as a password for millions of other accounts. Maybe it’s time to let Charlie rest and dig out the password manager instead.