A group of physicists from Russia, Sweden and the U.S. has demonstrated a highly unusual optical effect. They managed to “virtually” absorb light using a material that has no light-absorbing capacity. The research findings, published in Optica, break new ground for the creation of memory elements for light.
The absorption of electromagnetic radiation, including light, is one of the main effects of electromagnetism. This process takes place when electromagnetic energy is converted to heat or another kind of energy within an absorbing material (for instance, during electron excitation). Coal, black paint and carbon nanotube arrays—also known as Vantablack—appear black because they absorb the energy of the incident light almost completely. Other materials, such as glass or quartz, have no absorbing properties and therefore look transparent.
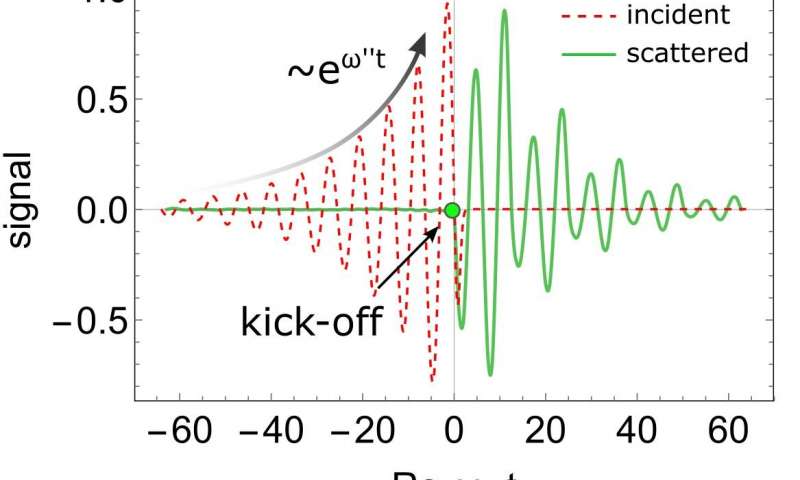
In their theoretical research, the results of which were published in the journal Optica, the physicists managed to dispel that simple and intuitive notion by making a completely transparent material appear perfectly absorbing. To achieve that, the researchers employed special mathematical properties of the scattering matrix—a function that relates an incident electromagnetic field with the one scattered by the system. When a light beam of time-independent intensity hits a transparent object, the light is not absorbed, but is scattered by the material—a phenomenon caused by the unitary property of the scattering matrix. It turned out, however, that if the intensity of the incident beam is varied with time in a certain fashion, the unitary property can be disrupted, at least temporarily. In particular, if the intensity growth is exponential, the total incident light energy will accumulate in the transparent material without leaving it (fig. 1). That being the case, the system will appear perfectly absorbent from the outside
Source: Scientists make transparent materials absorb light