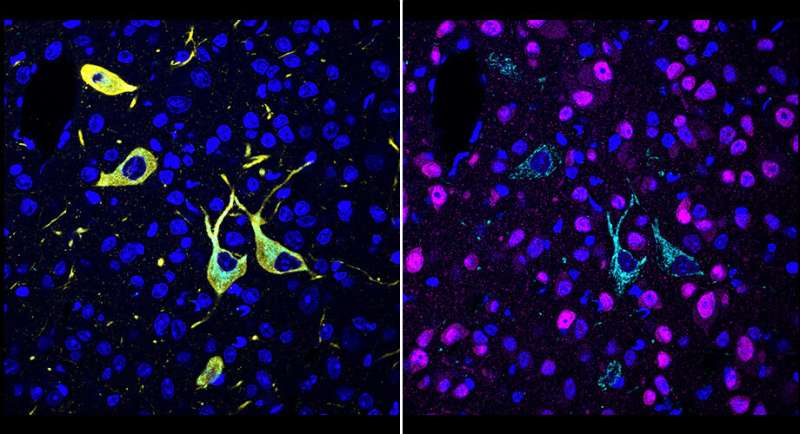
Scientists at Scripps Research have invented a way to image, across different tissues and with higher precision than ever before, where drugs bind to their targets in the body. The new method could become a routine tool in drug development.
Described in a paper in Cell on April 27, 2022, the new method, called CATCH, attaches fluorescent tags to drug molecules and uses chemical techniques to improve the fluorescent signal. The researchers demonstrated the method with several different experimental drugs, revealing where—even within individual cells—the drug molecules hit their targets.
[…]
The CATCH method involves the insertion of tiny chemical handles into drug molecules. These distinct chemical handles don’t react with anything else in the body, but do allow the addition of fluorescent tags after the drug molecules have bound to their targets. In part because human or animal tissue tends to diffuse and block the light from these fluorescent tags, Ye and his team combined the tagging process with a technique that makes tissue relatively transparent.
[…]
In other tests demonstrating the unprecedented precision and versatility of the new method, the scientists showed that they could combine drug-target imaging with separate fluorescent-tagging methods to reveal the cell types to which a drug binds. They also could distinguish drug-target engagement sites in different parts of neurons. Finally, they could see how modestly different doses of a drug often strikingly affect the degree of target engagement in different brain areas.
[…]
Source: New technique shows in detail where drug molecules hit their targets in the body