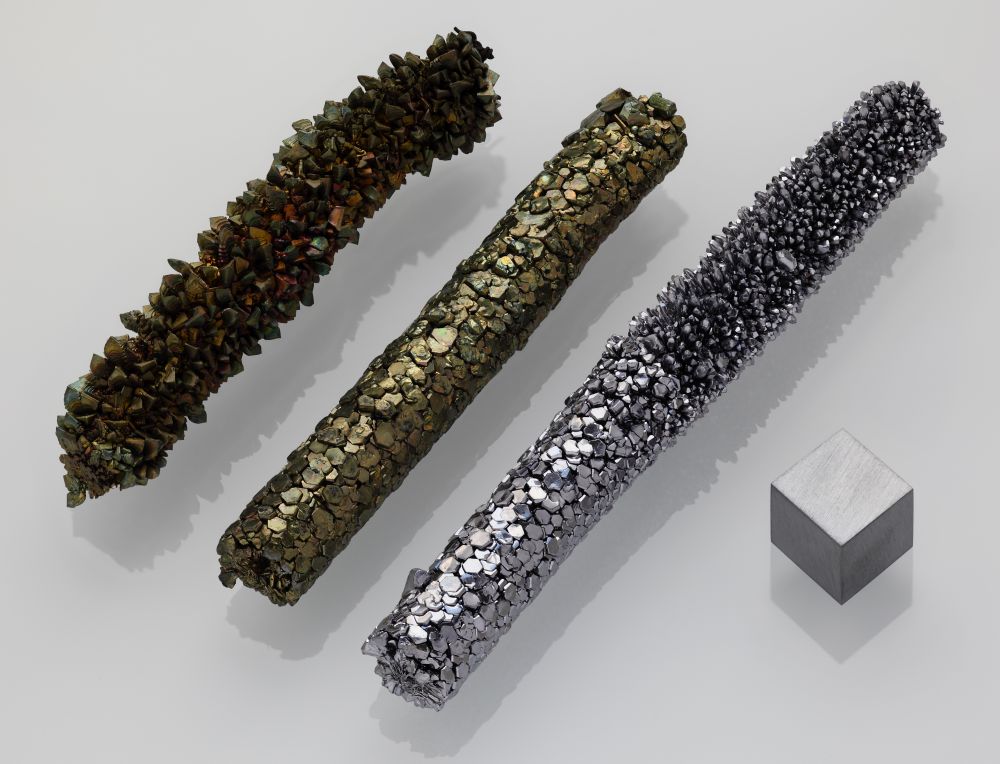
A chemical element so visually striking that it was named for a goddess shows a “Goldilocks” level of reactivity — neither too much nor too little — that makes it a strong candidate as a carbon scrubbing tool.
The element is vanadium, and research by Oregon State University scientists has demonstrated the ability of vanadium peroxide molecules to react with and bind carbon dioxide — an important step toward improved technologies for removing carbon dioxide from the atmosphere.
[…]
how some transition metal complexes can react with air to remove carbon dioxide and convert it to a metal carbonate, similar to what is found in many naturally occurring minerals.
Transition metals are located near the center of the periodic table and their name arises from the transition of electrons from low energy to high energy states and back again, giving rise to distinctive colors. For this study, the scientists landed on vanadium, named for Vanadis, the old Norse name for the Scandinavian goddess of love said to be so beautiful her tears turned to gold.
Nyman explains that carbon dioxide exists in the atmosphere at a density of 400 parts per million. That means for every 1 million air molecules, 400 of them are carbon dioxide, or 0.04%.
“A challenge with direct air capture is finding molecules or materials that are selective enough, or other reactions with more abundant air molecules, such as reactions with water, will outcompete the reaction with CO2,” Nyman said. “Our team synthesized a series of molecules that contain three parts that are important in removing carbon dioxide from the atmosphere, and they work together.”
One part was vanadium, so named because of the range of beautiful colors it can exhibit, and another part was peroxide, which bonded to the vanadium. Because a vanadium peroxide molecule is negatively charged, it needed alkali cations for charge balance, Nyman said, and the researchers used potassium, rubidium and cesium alkali cations for this study.
[…]
vanadium peroxide is a beautiful, purple Goldilocks that becomes golden when exposed to air and binds a carbon dioxide molecule.”
She notes that another valuable characteristic of vanadium is that it allows for the comparatively low release temperature of about 200 degrees Celsius for the captured carbon dioxide.
[…]
“Being able to rerelease the captured CO2 enables reuse of the carbon capture materials, and the lower the temperature required for doing that, the less energy that’s needed and the smaller the cost. There are some very clever ideas about reuse of captured carbon already being implemented — for example, piping the captured CO2 into a greenhouse to grow plants.”
[…]
Story Source:
Materials provided by Oregon State University. Original written by Steve Lundeberg. Note: Content may be edited for style and length.
Journal Reference:
- Eduard Garrido Ribó, Zhiwei Mao, Jacob S. Hirschi, Taylor Linsday, Karlie Bach, Eric D. Walter, Casey R. Simons, Tim J. Zuehlsdorff, May Nyman. Implementing vanadium peroxides as direct air carbon capture materials. Chemical Science, 2024; 15 (5): 1700 DOI: 10.1039/D3SC05381D


 […]
[…]