Since late 2013, this band of cybercriminals has penetrated the digital inner sanctums of more than 100 banks in 40 nations, including Germany, Russia, Ukraine, and the U.S., and stolen about $1.2 billion, according to Europol, the European Union’s law enforcement agency. The string of thefts, collectively dubbed Carbanak—a mashup of a hacking program and the word “bank”—is believed to be the biggest digital bank heist ever.
[…]
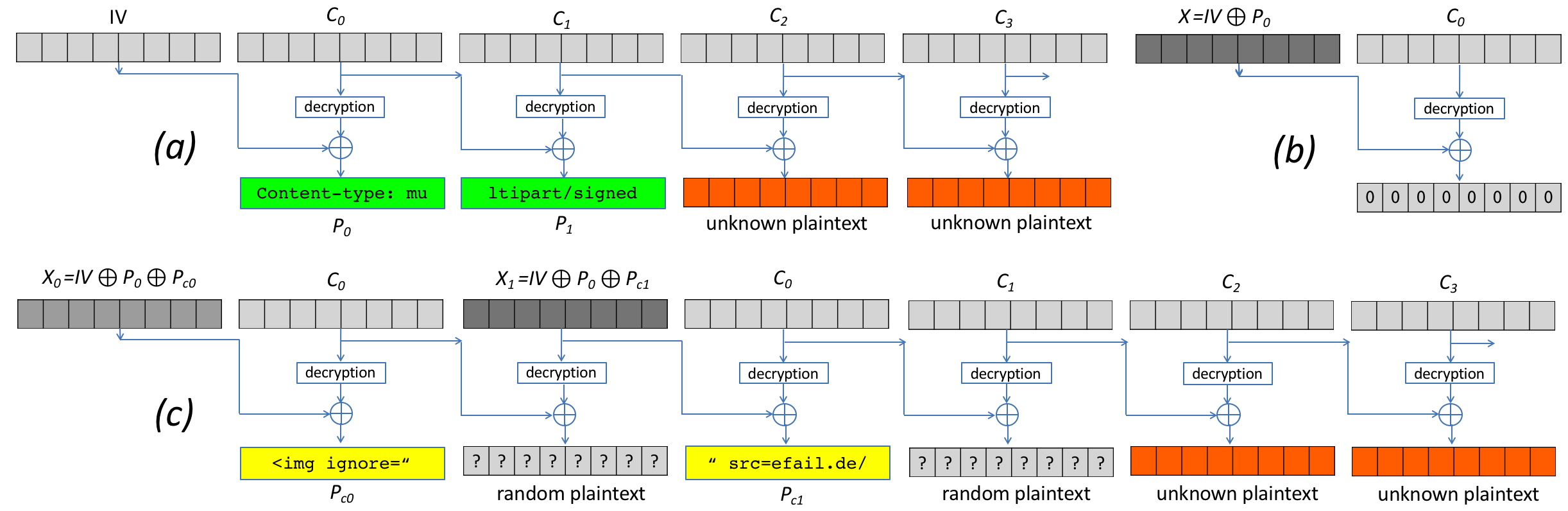
Besides forcing ATMs to cough up money, the thieves inflated account balances and shuttled millions of dollars around the globe. Deploying the same espionage methods used by intelligence agencies, they appropriated the identities of network administrators and executives and plumbed files for sensitive information about security and account management practices.
[…]
For years police and banking-industry sleuths doubted they’d ever catch the phantoms behind Carbanak. Then, in March, the Spanish National Police arrested Ukrainian citizen Denis Katana in the Mediterranean port city of Alicante. The authorities have held him since then on suspicion of being the brains of the operation. Katana’s lawyer, Jose Esteve Villaescusa, declined to comment, and his client’s alleged confederates couldn’t be reached for comment. While Katana hasn’t been charged with a crime, Spanish detectives say financial information, emails, and other data trails show he was the architect of a conspiracy that spanned three continents. And there are signs that the Carbanak gang is far from finished.
[…]
The attackers cased their targets for months, says Kaspersky. The Carbanak crew was looking for executives with the authority to direct the flow of money between accounts, to other lenders, and to ATMs. They were also studying when and how the bank moved money around. The thieves didn’t want to do anything that would catch the eyes of security. State-backed spies use this type of reconnaissance in what’s known as an advanced persistent threat. “In those instances, the attacks are designed to steal data, not get their hands on money,” Emm says. When the time was right, the thieves used the verification codes of bank officers to create legit-looking transactions.
By the fall of 2014, the authorities realized they were dealing with something new. That October, Keith Gross, chair of the cybersecurity group for a European bank lobby, called a crash meeting with experts from Citigroup, Deutsche Bank, and other major European lenders. In a meeting room at Europol’s fortress-like headquarters in The Hague, Kaspersky researchers briefed the bank officials on what they’d found in Ukraine. “I’ve never seen anything like this before,” Troels Oerting, then the head of Europol’s Cybercrime Centre, told the group. “It’s a well-orchestrated malware attack, it’s very sophisticated, and it’s global.”
So Europol went global, too, enlisting help from law enforcement agencies in Belarus, Moldova, Romania, Spain, Taiwan, the U.S., as well as bank industry representatives. It set up a secure online clearinghouse where investigators could cross-check data and find links between the thefts, says Fernando Ruiz, head of operations in Europol’s cybercrime unit. At the heart of its operation was a lab where technicians dissected the two dozen samples of malware identified in the Carbanak thefts. By isolating unique characteristics in the code, detectives could trace where the programs came from and maybe who was using them. The work led them toward Denis Katana’s apartment in Alicante, a four-hour drive southeast of Madrid. “This is what the Spanish police used to open their investigation,” Ruiz says.
[…]
Yet experts point out that even if Katana was the mastermind, he was just one guy in a crime that surely must have had many authors. Unlike the bank jobs of yore, digital heists are amoeba-like ventures that divide over and over again as the malware proliferates. “We’ve already seen the modification of Carbanak and multiple groups using it,” says Kimberly Goody, an analyst at security software maker FireEye Inc. “Same case with Cobalt.”
In recent weeks, employees at banks in the Russian-speaking world have been receiving emails that appear to be from Kaspersky, the security company that unearthed Carbanak. The messages warn recipients that their PCs have been flagged for possibly violating the law and they should download a complaint letter or face penalties. When they click on the attachment, a version of the Cobalt malware infects their networks. It turns out cyberheists may not die even when their suspected perpetrators are nabbed.