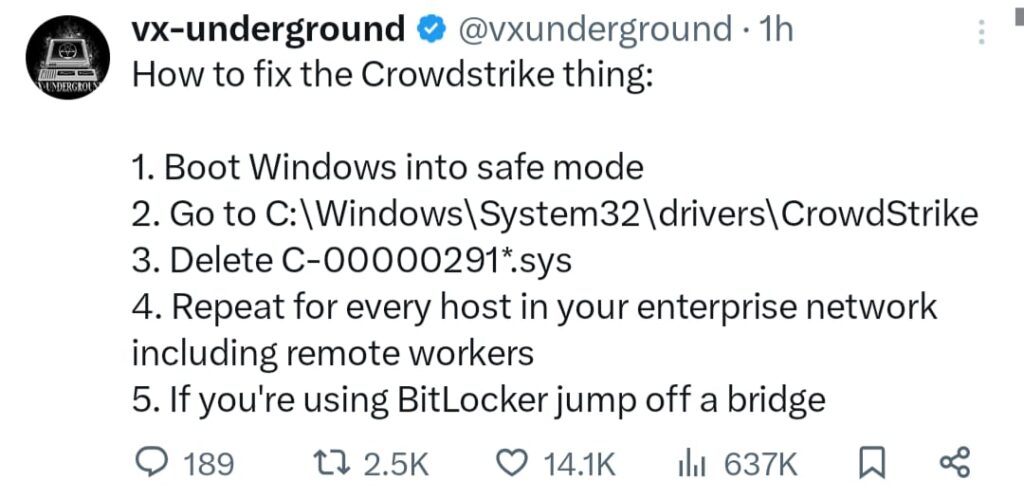
Running a Chromium-based browser, such as Google Chrome or Microsoft Edge? The chances are good it’s quietly telling Google all about your CPU and GPU usage when you visit one of the search giant’s websites.
The feature is, from what we can tell, for performance monitoring and not really for tracking – Google knows who you are and what you’re doing anyway when you’re logged into and using its sites – but it does raise some antitrust concerns in light of Europe’s competition-fostering Digital Markets Act (DMA).
When visiting a *.google.com domain, the Google site can use the API to query the real-time CPU, GPU, and memory usage of your browser, as well as info about the processor you’re using, so that whatever service is being provided – such as video-conferencing with Google Meet – could, for instance, be optimized and tweaked so that it doesn’t overly tax your computer. The functionality is implemented as an API provided by an extension baked into Chromium – the browser brains primarily developed by Google and used in Chrome, Edge, Opera, Brave, and others.
Non-Chromium-based browsers – such as Mozilla’s Firefox – don’t have that extension, which puts them at a potential disadvantage. Without the API, they may offer a worse experience on Google sites than what’s possible on the same hardware with Google’s own browser, because they can’t provide that live performance info.
There is, however, nothing technically stopping Moz or other browser-engine makers implementing a similar extension itself in Firefox, if they so chose.
Crucially though, websites that compete against Google can’t access the Chromium API. This is where technical solutions start to look potentially iffy in the eyes of Europe’s DMA.
Netherlands-based developer Luca Casonato highlighted the extension’s existence this week on social media, and his findings went viral – with millions of views. We understand at least some people have known about the code for a while now – indeed, it’s all open source and can be found here in the preinstalled extension hangout_services.
That name should give you a clue to its origin. It was developed last decade to provide browser-side functionality to Google Hangouts – a product that got split into today’s Google Meet and Chat. Part of that functionality is logging for Google, upon request, stats about your browser’s use of your machine’s compute resources when visiting a *.google.com domain – such as meet.google.com.
Casonato noted that the extension can’t be disabled in Chrome, at least, and it doesn’t show up in the extension panel. He observed it’s also included in Microsoft Edge and Brave, both of which are Chromium based. We reached out to Casonato for more of his thoughts on this – though given the time differences between him in Europe and your humble vulture in the US, we didn’t immediately hear back.
Explanation
If you’ve read this far there’s probably an obvious question on your mind: What’s to say this API is malicious? We’re not saying that, and neither is Casonato. Google isn’t saying that either.
“Today, we primarily use this extension for two things: To improve the user experience by optimizing configurations for video and audio performance based on system capabilities [and] provide crash and performance issue reporting data to help Google services detect, debug, and mitigate user issues,” a Google spokesperson told us on Thursday.
“Both are important for the user experience and in both cases we follow robust data handling practices designed to safeguard user privacy,” the spokesperson added.
As we understand it, Google Meet today uses the old Hangouts extension to, for one thing, vary the quality of the video stream if the current resolution is proving too much for your PC. Other Google sites are welcome to use the thing, too.
That all said, the extension’s existence could be harmful to competition as far as the EU is concerned – and that seems to be why Casonato pointed it out this week.
A lovely explanation, but the fact remains that chromium is sending personal information to a central company: Google, without informing users at all. This blanket explanation could be used to whitewash any information they send through Chromium: the contents of your memory? Improving user experience. The position of your mouse on websites? Improving user experience. It just does not wash.