Global warming is largely caused by carbon dioxide and other gases absorbing infrared radiation, trapping heat in Earth’s atmosphere – known as the greenhouse effect.
The most accurate climate models use precise measurements of the amount of radiation CO₂ can absorb to calculate how much heat will be trapped in the atmosphere. These models are excellent at predicting future changes in Earth’s climate, but they don’t provide a physical explanation for why this gas can absorb so much radiation, which can make their predictions difficult to explain.
Robin Wordsworth at Harvard University and his colleagues have now shown how CO₂’s heat-trapping properties can be explained in terms of quantum mechanical effects, in particular a phenomenon called the Fermi resonance.
Sign up to our Fix the Planet newsletter
Get a dose of climate optimism delivered straight to your inbox every month.
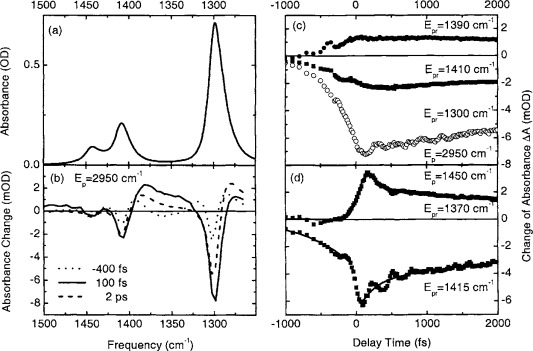
“Rather than just a narrow range of radiation getting absorbed, as you would naively expect, it becomes much broader,” says Wordsworth. “It’s this broadening which is really critical to understanding why carbon dioxide is an important greenhouse gas.”
The Fermi resonance describes how the different directions and patterns in which molecules vibrate can influence each other and make them vibrate more. This is similar to how two pendulums, connected by a shared string, can increase the amplitude of each other’s swinging.
A molecule of CO₂ consists of two oxygen atoms bonded to one carbon atom. Two of the molecule’s vibrations influence each other to make it absorb more light: a side-to-side stretching of the oxygen atoms, and a sidewinder snake-like zigzagging of these atoms.
Wordsworth and his colleagues came up with equations to describe how much radiation CO₂ can absorb based on its physical properties, with and without the Fermi resonance. They found that its light-absorbing features and its warming effect on Earth’s atmosphere could only be reproduced when the resonance was included.
The Fermi resonance was responsible for nearly half of the total warming effect. “Even things that are happening on the scale of our planet are determined, ultimately, by what’s going on at the micro scale,” says Wordsworth.
While it was already known that CO₂ had a particularly large Fermi resonance, having an equation that links this to the greenhouse effect could be useful for quick calculations without running a full climate model, says Jonathan Tennyson at University College London. This could also help physicists model the climate of exoplanets, which can require large amounts of computing power to fully simulate.
Something that Wordsworth and his team couldn’t explain is why CO₂ vibrates in such a unique way – a question that might never be answered without a theory of everything. “There doesn’t seem to be a clear reason why this resonance occurs in CO₂,” says Wordsworth. “One could imagine a different universe where it was slightly different, and carbon dioxide might not have the same effects.”
Reference:
Source: Quantum quirk explains why carbon dioxide causes global warming | New Scientist