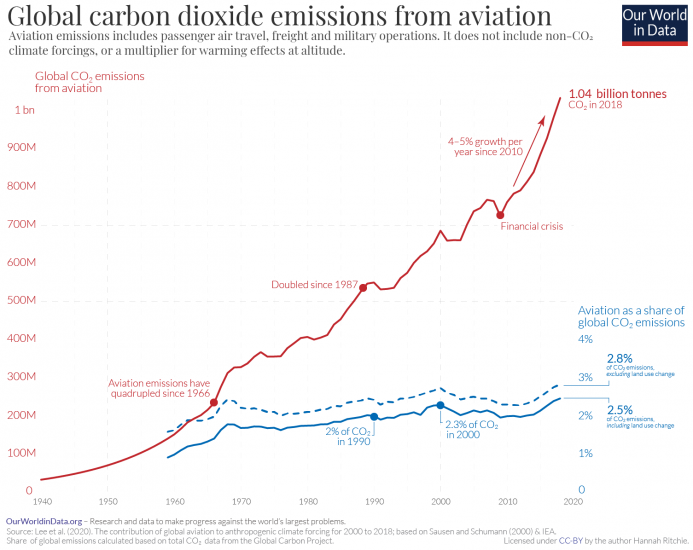
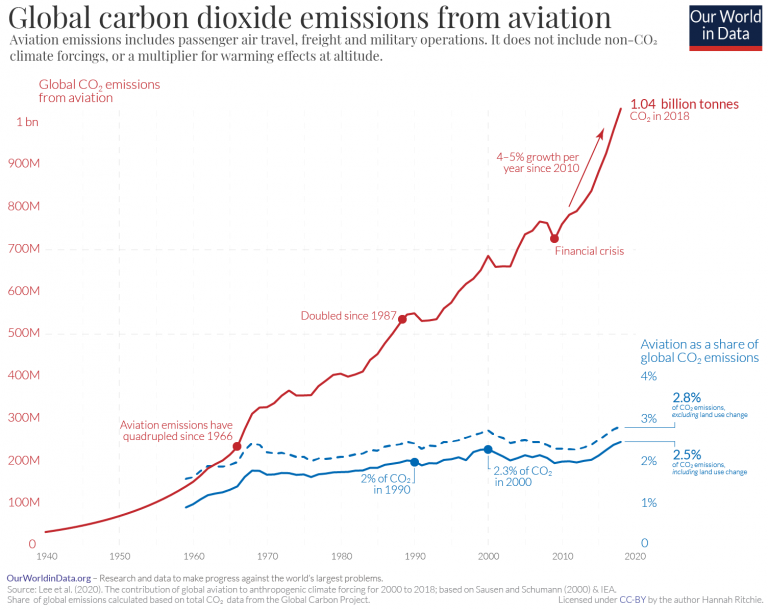
We all knew it was coming. Today, the US government’s Department of Justice filed an antitrust lawsuit against Google. The company, which is a part of Alphabet, is accused of having an unfair monopoly over search and search-related advertising. In addition, the department disagrees with the terms around Android, the most widely-used mobile operating system, that forces phone manufacturers to pre-load Google applications and set Google as the default search engine. That decision stops rival search providers from gaining traction and, as a consequence, ensures that Google continues to make enormous amounts of cash via search-related advertising.
“Google pays billions of dollars each year to distributors—including popular-device manufacturers such as Apple, LG, Motorola, and Samsung; major U.S. wireless carriers such as AT&T, T-Mobile, and Verizon; and browser developers such as Mozilla, Opera, and UCWeb— to secure default status for its general search engine and, in many cases, to specifically prohibit Google’s counterparties from dealing with Google’s competitors,” the lawsuit filing reads.
[…]
Walker also argued that Google competes with platforms such as Twitter, Expedia and OpenTable, which let you search for news, flights and restaurant reservations respectively.” Every day, Americans choose to use all these services and thousands more,” he said.
Some of Google’s rivals feel differently. “We’re pleased the DOJ has taken this key step in holding Google accountable for the ways it has blocked competition, locked people into using its products, and achieved a market position so dominant they refuse to even talk about it out loud,” Gabriel Weinberg, CEO of search engine provider DuckDuckGo said in a Twitter thread. “While Google’s anti-competitive practices hurt companies like us, the negative impact on society and democracy wrought by their surveillance business model is far worse. People should be able to opt out in one click.”
As the Wall Street Journal explains, the Justice Department has been preparing to launch this case for over a year. “Over the course of the last 16 months, the Antitrust Division collected convincing evidence that Google no longer competes only on the merits but instead uses its monopoly power – and billions in monopoly profits – to lock up key pathways to search on mobile phones, browsers, and next generation devices, depriving rivals of distribution and scale,” the Department said in a statement today.
[…]
Today’s lawsuit is arguably the biggest antitrust move since the government’s case against Microsoft in 1998. Back then, the technology company was accused of using its Windows monopoly to push Microsoft-made software such as Internet Explorer. A judge eventually ordered Microsoft to break up into two separate companies. The technology giant appealed, however, and by the end of 2001 it had reached a settlement with the department. “Back then, Google claimed Microsoft’s practices were anticompetitive, and yet, now, Google deploys the same playbook to sustain its own monopolies,” the Justice Department argues in today’s lawsuit filing.
Source: The Department of Justice sues Google over antitrust concerns | Engadget
The timing of this is not coincidental. The DoJ was apparently pushed into this before it was ready in order to look good for the elections.
I have been talking about this since early 2019 and it’s great to see how this has been gaining traction since then