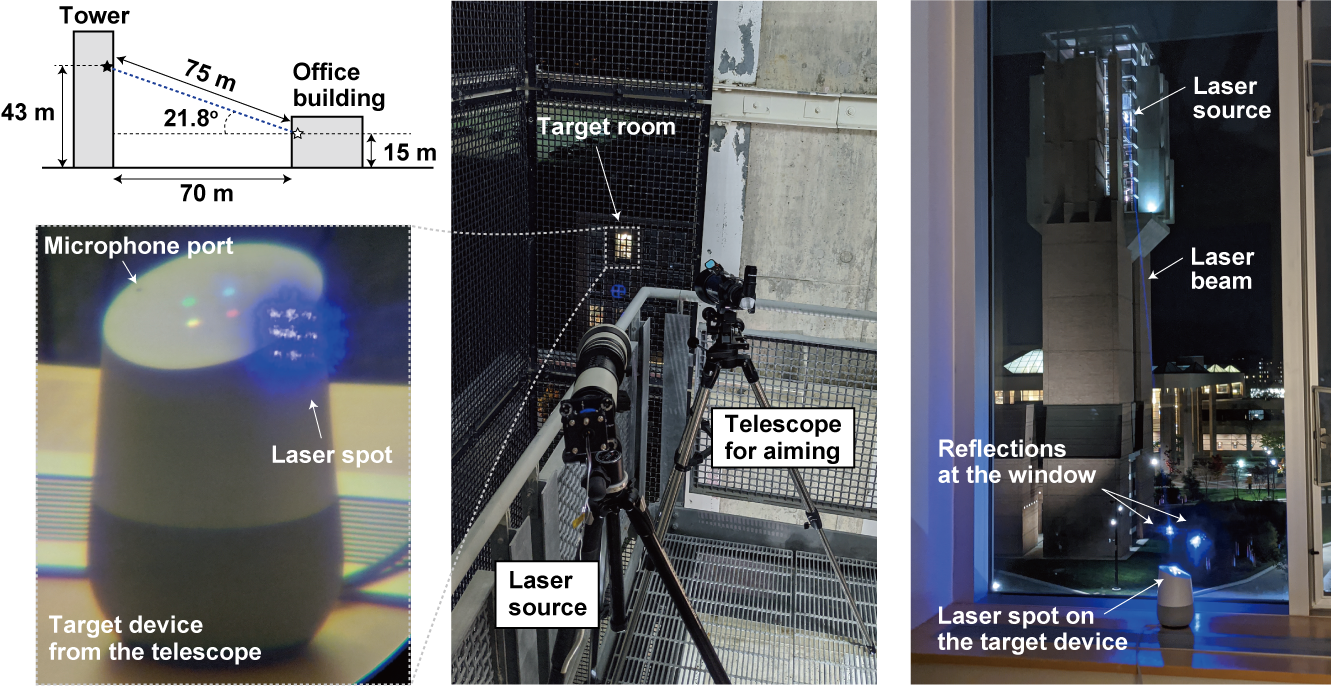
A confidential Sidewalk Labs document from 2016 lays out the founding vision of the Google-affiliated development company, which included having the power to levy its own property taxes, track and predict people’s movements and control some public services.
The document, which The Globe and Mail has seen, also describes how people living in a Sidewalk community would interact with and have access to the space around them – an experience based, in part, on how much data they’re willing to share, and which could ultimately be used to reward people for “good behaviour.”
Known internally as the “yellow book,” the document was designed as a pitch book for the company, and predates Sidewalk’s relationship and formal agreements with Toronto by more than a year. Peppered with references to Disney theme parks and noted futurist Buckminster Fuller, it says Sidewalk intended to “overcome cynicism about the future.”
But the 437-page book documents how much private control of city services and city life Google parent company Alphabet Inc.’s leadership envisioned when it created the company,
[…]
“The ideas contained in this 2016 internal paper represent the result of a wide-ranging brainstorming process very early in the company’s history,” Sidewalk spokesperson Keerthana Rang said. “Many, if not most, of the ideas it contains were never under consideration for Toronto or discussed with Waterfront Toronto and governments. The ideas that we are actually proposing – which we believe will achieve a new model of inclusive urban growth that makes housing more affordable for families, creates new jobs for residents, and sets a new standard for a healthier planet – can all be found at sidewalktoronto.ca.”
[…]
To carry out its vision and planned services, the book states Sidewalk wanted to control its area much like Disney World does in Florida, where in the 1960s it “persuaded the legislature of the need for extraordinary exceptions.” This could include granting Sidewalk taxation powers. “Sidewalk will require tax and financing authority to finance and provide services, including the ability to impose, capture and reinvest property taxes,” the book said. The company would also create and control its own public services, including charter schools, special transit systems and a private road infrastructure.
Sidewalk’s early data-driven vision also extended to public safety and criminal justice.
The book mentions both the data-collection opportunities for police forces (Sidewalk notes it would ask for local policing powers similar to those granted to universities) and the possibility of “an alternative approach to jail,” using data from so-called “root-cause assessment tools.” This would guide officials in determining a response when someone is arrested, such as sending someone to a substance abuse centre. The overall criminal justice system and policing of serious crimes and emergencies would be “likely to remain within the purview of the host government’s police department,” however.
Data collection plays a central role throughout the book. Early on, the company notes that a Sidewalk neighbourhood would collect real-time position data “for all entities” – including people. The company would also collect a “historical record of where things have been” and “about where they are going.” Furthermore, unique data identifiers would be generated for “every person, business or object registered in the district,” helping devices communicate with each other.
There would be a quid pro quo to sharing more data with Sidewalk, however. The document describes a tiered level of services, where people willing to share data can access certain perks and privileges not available to others. Sidewalk visitors and residents would be “encouraged to add data about themselves and connect their accounts, either to take advantage of premium services like unlimited wireless connectivity or to make interactions in the district easier,” it says.
Shoshana Zuboff, the Harvard University professor emerita whose book The Age of Surveillance Capitalism investigates the way Alphabet and other big-tech companies are reshaping the world, called the document’s revelations “damning.” The community Alphabet sought to build when it launched Sidewalk Labs, she said, was like a “for-profit China” that would “use digital infrastructure to modify and direct social and political behaviour.”
While Sidewalk has since moved away from many of the details in its book, Prof. Zuboff contends that Alphabet tends to “say what needs be said to achieve commercial objectives, while specifically camouflaging their actual corporate strategy.”
[…]
hose choosing to remain anonymous would not be able to access all of the area’s services: Automated taxi services would not be available to anonymous users, and some merchants might be unable to accept cash, the book warns.
The document also describes reputation tools that would lead to a “new currency for community co-operation,” effectively establishing a social credit system. Sidewalk could use these tools to “hold people or businesses accountable” while rewarding good behaviour, such as by rewarding a business’s good customer service with an easier or cheaper renewal process on its licence.
This “accountability system based on personal identity” could also be used to make financial decisions.
“A borrower’s stellar record of past consumer behaviour could make a lender, for instance, more likely to back a risky transaction, perhaps with the interest rates influenced by digital reputation ratings,” it says.
The company wrote that it would own many of the sensors it deployed in the community, foreshadowing a battle over data control that has loomed over the Toronto project.